Web application security (also known as Web AppSec) is the idea of building websites to function as expected, even when they are under attack. The concept involves a collection of security controls engineered into a Web application to protect its assets from potentially malicious agents.
It involves leveraging secure development practices and implementing security measures throughout the software development life cycle (SDLC), ensuring that design-level flaws and implementation-level bugs are addressed.

What are important web application security strategies?
As mentioned, web application security is a broad, always-changing discipline. As such, the discipline’s best practices change as new attacks and vulnerabilities emerge. But the modern Internet threat landscape is active enough that no organization will be able to get by without certain ‘table stakes’ security services that map to their business’ specific needs:
- DDoS mitigation: DDoS mitigation services sit between a server and the public Internet, using specialized filtration and extremely high bandwidth capacity to prevent surges of malicious traffic from overwhelming the server. These services are important because many modern DDoS attacks deliver enough malicious traffic to whelm even the most resilient servers.
- Web Application Firewall: Which filter out traffic known or suspected to be taking advantage of web application vulnerabilities. WAFs are important because new vulnerabilities emerge too quickly and quietly for nearly all organizations to catch on their own.
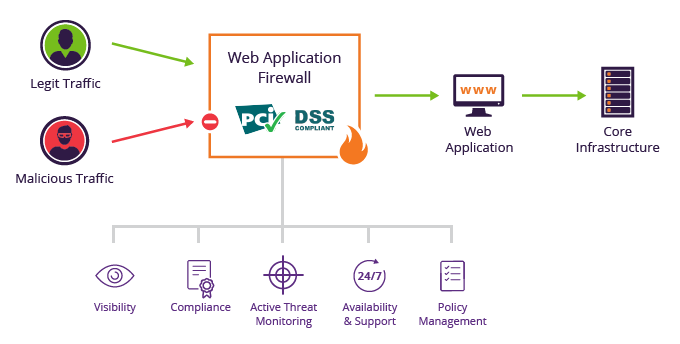
- API gateways: Which help identify overlooked ‘shadow APIs,’ and block traffic known or suspected to target API vulnerabilities. They also help manage and monitor API traffic.
- DNSSES A protocol which guarantees a web application’s DNS traffic is safely routed to the correct servers, so users are are not intercepted by an on-path attacker.
- Encryption certificate management: In which a third party manages key elements of the SSL/TLS encryption process, such as generating private keys, renewing certificates, and revoking certificates due to vulnerabilities. This removes the risk of those elements going overlooked and exposing private traffic.
- Client-side security: Which checks for new third-party JavaScript dependencies and third-party code changes, helping organizations catch malicious activity sooner.
- Attack surface management: actionable attack surface management tools should provide a single place to map your attack surface, identify potential security risks, and mitigate risks with a few clicks.
What Is Web Application Security?
By most estimates, more than three-quarters of all cybercrime targets applications and their vulnerabilities. Web application security products and policies strive to protect applications through measures such as web application firewalls (WAFs), multi-factor authentication (MFA) for users, the use, protection, and validation of cookies to maintain user state and privacy status, and various methods for validating user input to ensure it is not malicious before that input is processed by an application.
Web application security refers to a variety of processes, technologies, or methods for protecting web servers, web applications, and web services such as APIs from attack by Internet-based threats.
Advantages of Web Application Security
Web application security is crucial for protecting sensitive data, maintaining user trust, and safeguarding business operations.
Protection of Sensitive Data
- Data Confidentiality: Prevents unauthorized access to sensitive information such as financial data, personal details, and intellectual property.
- Data Integrity: Ensures that data remains accurate and complete, preventing tampering or modification.
- Data Availability: Guarantees uninterrupted access to critical data and services.
Enhanced User Trust and Reputation
- Customer Confidence: Builds trust among users by demonstrating a commitment to protecting their information.
- Brand Protection: Safeguards the company’s reputation and prevents damage caused by data breaches.
- Regulatory Compliance: Helps organizations adhere to industry-specific regulations and standards (e.g., GDPR, HIPAA, PCI DSS).
Cost Reduction
- Reduced Financial Losses: Prevents financial losses due to data breaches, including legal fees, regulatory fines, and loss of revenue.
- Lower Insurance Premiums: Strong security measures can lead to reduced insurance costs.
- Improved Efficiency: Secure systems can operate more efficiently without the disruption caused by security incidents.
Business Continuity
- Minimized Downtime: Protects against attacks that can disrupt business operations.
- Disaster Recovery: Enables faster recovery from security incidents.
- Competitive Advantage: A strong security posture can provide a competitive advantage by demonstrating a commitment to customer protection.
Legal and Ethical Obligations
- Compliance: Adherence to data protection laws and regulations.
- Ethical Responsibility: Protecting user privacy and data.
Disadvantages of Web Application Security
Complexity and Cost
- Resource Intensive: Implementing and maintaining robust security measures requires significant time, effort, and financial resources.
- Ongoing Costs: Security is an ongoing process that demands continuous investment in tools, personnel, and updates.
- Skill Shortage: Finding qualified security professionals can be challenging and expensive.
Evolving Threat Landscape
- New Threats: Cybercriminals are constantly developing new attack techniques, making it difficult to stay ahead.
- Zero-Day Vulnerabilities: Exploits that target unknown vulnerabilities can be difficult to defend against.
- Complex Attack Vectors: Modern attacks often involve multiple attack vectors, making defense challenging.
Balancing Security with User Experience
- Friction: Excessive security measures can create friction for users, leading to frustration and decreased usability.
- False Positives: Security systems may mistakenly flag legitimate activities as threats, causing inconvenience.
- Performance Impact: Some security measures can impact application performance.
Reliance on Third-Party Components
- Supply Chain Risks: Vulnerabilities in third-party libraries or components can expose the application to risks.
- Dependency Management: Keeping track of and updating third-party components can be complex.
Human Error
- Social Engineering: Employees can be tricked into revealing sensitive information or clicking on malicious links.
- Accidental Errors: Mistakes by developers or administrators can create security vulnerabilities.
Why is web security testing important?
Web security testing aims to find security vulnerabilities in Web applications and their configuration. The primary target is the application layer (i.e., what is running on the HTTP protocol). Testing the security of a Web application often involves sending different types of input to provoke errors and make the system behave in unexpected ways. These so called “negative tests” examine whether the system is doing something it isn’t designed to do.
It is also important to understand that Web security testing is not only about testing the security features (e.g., authentication and authorization) that may be implemented in the application. It is equally important to test that other features are implemented in a secure way (e.g., business logic and the use of proper input validation and output encoding). The goal is to ensure that the functions exposed in the Web application are secure.
What are the different types of security tests?
Every app should go through the testing procedure because it aids in the detection of security flaws. Different forms of security testing are used to test every component of the program.
- Vulnerability Scanning
- Security Scanning
- Penetration Testing
- Risk Assessment
- Security Auditing
- Ethical Hacking

Vulnerability Scanning
This sort of security testing comprises the use of automated tools to discover system bugs. Vulnerability scanners check at web apps from the outside in order to detect cross-site scripting (XSS), SQL injections, command injections, and unsecured server settings, among other things. The disadvantage of vulnerability scanning is that it can trigger a system crash if it mistakenly believes it’s doing something inappropriate.
Security Scanning
The goal of security scanning is to determine the system’s overall security level by identifying weak spots and defects. The security scan must be more difficult the more complex the system or network is. It can be done once, but most software development businesses prefer to scan for vulnerabilities on a routine basis.
Penetration Testing
Pentesting is the act of simulating a cyberattack in order to find vulnerable flaws. Application penetration testing, which looks for technical flaws, and infrastructure penetration testing, which looks at servers, firewalls, as well as other hardware, are the two most frequent types of penetration testing.
Risk Assessment
The process of identifying and implementing critical security measures in software is known as a security risk assessment. It also emphasizes the avoidance of security flaws and vulnerabilities. Organizations can use a complete security assessment to establish risk levels for systems, servers, apps, and other devices, assess their criticality in terms of business operations and implement preventive policies based on the evaluation results.
Security Auditing
The practice of testing and evaluating the security of a company’s information system is known as security auditing. A security audit can be used to check the effectiveness of a company’s security plan, detect malicious software, and certify compliance with the laws.
Ethical Hacking
The process of breaking into a system to uncover vulnerabilities before a harmful attacker can find and exploit them is known as “ethical hacking.” Ethical hackers may utilize the very same tactics and tools as cybercriminals, but only with the authorization of the authorized person; they must also notify management of any vulnerabilities discovered throughout the process.
What features should be reviewed during a web application security test?
- Application and server configuration. Potential defects are related to encryption/cryptographic configurations, Web server configurations, etc.
- Input validation and error handling. SQL injection, cross-site scripting (XSS), and other common injection vulnerabilities are the result of poor input and output handling.
- Authentication and session management. Vulnerabilities potentially resulting in user impersonation. Credential strength and protection should also be considered.
- Authorization. Testing the ability of the application to protect against vertical and horizontal privilege escalations.
- Business logic. These are important to most applications that provide business functionality.
- Client-side logic. With modern, JavaScript-heavy webpages, in addition to webpages using other types of client-side technologies (e.g., Silverlight, Flash, Java applets), this type of feature is becoming more prevalent.
The Need for Web Application Security
The world is becoming more digital, and web applications are used in virtually all aspects of human life, from social to financial. Therefore, web applications represent a lucrative target for attackers, and the potential threats are growing and increasing in severity.
There are several reasons why organizations should prioritize web application security:
- Growing threats: Cybercriminals are on the lookout for vulnerabilities in web applications to exploit for malicious purposes. These attacks can lead to significant financial loss, damage to brand reputation, and loss of customer trust.
- Compliance requirements: Many governments and industries have strict regulations around data security and privacy. Failing to meet these regulations can result in hefty fines, lawsuits, and loss of business.
- Technical complexity: The complexity of web applications is growing. With the rise of mobile applications, cloud computing, and microservices architectures, the attack surface for web applications is expanding. This complexity makes it more challenging to secure web applications.
What Are Web Application Attacks?
Web application attacks are malicious attempts to exploit vulnerabilities in web applications or mobile apps. These attacks aim to disrupt business operations, steal sensitive data, or gain unauthorized access to an organization’s IT infrastructure.
Common Types of Web Application Attacks:
- SQL Injection: Exploiting vulnerabilities in SQL queries to access or modify database data.
- Cross-Site Scripting (XSS): Injecting malicious scripts into a vulnerable website to steal user information or hijack sessions.
- Cross-Site Request Forgery (CSRF): Tricking a user into performing actions on a website they trust, without their knowledge.
- Injection: Similar to SQL injection, but covers other types of injections like OS command injection, LDAP injection, etc.
- Broken Authentication and Session Management: Weak or missing authentication mechanisms allowing unauthorized access.
- Sensitive Data Exposure: Improper protection of sensitive data, leading to data breaches.
Impact of Web Application Attacks
- Financial loss: Due to data breaches, fraud, or business disruption.
- Reputation damage: Loss of customer trust and confidence.
- Legal consequences: Non-compliance with data protection regulations.
Prevention and Mitigation
To protect against web application attacks, organizations should:
- Follow secure coding practices.
- Conduct regular security audits and penetration testing.
- Implement a web application firewall (WAF).
- Keep software and applications up-to-date with the latest patches.
- Educate employees about security best practices.
What are the strategies to secure Web applications?
Today, web applications are a critical aspect of business and everyday life. By using web applications, both businesses and individuals can simplify and get more things done with fewer resources, achieving objectives much faster than they could before.
- They no longer need a warehouse full of meticulously organized paperwork.
- There is little or no need to rely on actual physical mail now for communication.
- Most marketing efforts are now highly web-focused.
- Even customer service is now pointing you to websites instead of 1-800 phone numbers.
Web applications can help target a proliferating amount of clientele and customers in ways that were never available to before. Web apps can interact with your customers to communicate, offer product support, and keep their business.
Because we are using web applications for so many things and passing so much sensitive information around via so many different types of online channels, we should next be obliged to also take a hard stance at protecting and securing that information.
To date, no web technology has proven itself invulnerable beyond all doubt. New threats pop up every single day that require at least some change or improvement in implementing countermeasures and general web-focused security. To improve the overall quality of web applications, developers should abide by these rules.
Different uses for web app security testing
Testing every type of web technology
Web applications themselves come in a number of different flavors. These include mobile apps, single page apps (SPA) and progressive web apps (PWA). Each has a distinct set of requirements for security testing. SPAs, for instance, make heavy use of JavaScript – which is notoriously difficult for automated scanners to process.
Staying compliant
Certain industries also have their own very specific needs. Finance and e-commerce, for instance, are heavily regulated by cybersecurity compliance standards due to the level of data they hold on their customers. This makes security testing critical.
Automating at scale
The size of an organization using security testing will also affect its chosen solution. Certainly at the enterprise level – where many thousands of web apps might sit within a single portfolio – automation is vital. But an automated vulnerability scanner can’t employ creativity like a human can, so manual penetration tests should always be carried out.
Penetration testing
Penetration testers (or pentesters) are the experts who can simulate attacks on your “vault” in order to improve it. And pentesting itself sits under the larger umbrella of ethical hacking. Ethical hacking also includes bug bounty hunters, who will race to find security bugs in a web app if a bounty is offered. One way to initiate this is through a scheme like HackerOne.
Secure development
As we touched on earlier, a prime factor in securing a bank vault would be to ensure that it was built well in the first place. Traditionally, web app security is delayed until after development has ended, which causes delays and can cost a great deal of money. Quite simply, it’s difficult to develop software and worry about security at the same time.
But the power of automated security testing allows a DevSecOps approach. DevSecOps empowers developers to write secure code. And because security is built in, rather than tagged on at the end, apps are more secure on release day. The best DevSecOps solutions even educate the developers who use them – meaning fewer bugs to fix in the first place.
What are Web Application Security Testing Tools?
Web application security testing checks websites and web app elements to spot potential security weaknesses. It crawls networks, databases, and application codebases to identify vulnerabilities that attackers can exploit to raid the sensitive data in your web application. Some of the most common vulnerabilities that web app scanners protect against include SQL injections, cross-site scripting (XSS), malicious code, and misconfigurations.
You can operate these scanners manually or automate them. In automation mode, they crawl your application on a schedule, analyzing input fields, forms, and other website elements. This is ideal for routine scans and contributes to maintaining a secure-by-design system. Manual web application security testing is typically used for in-depth assessments, enabling you to interact more directly with the application.
Key Features for Web Application Security Testing Tools
Accuracy and Low False Positives
If your tool flags a vulnerability that doesn’t exist, it will send the team on a wild goose chase, burning time and resources. Web app security testing is generally great for ensuring low false positives, because it finds results in the runtime context of the application.
Automated Scanning and Scheduling
A web app security testing must monitor your website or app and its assets without human assistance to ensure continuous and (relatively) low effort risk detection and remediation. It should also allow you to schedule the crawling sessions for continuous monitoring. Using a security orchestrator like Jit, you can easily schedule and automate all your web app scans.
Integration with Development Tools
Your scanning tool should seamlessly integrate with:
- CI/CD pipelines to trigger scans based on new deployments
- Development tools like code repositories and integrated development environments
- Security tools like web application firewalls, audit tools, and penetration testing tools
- Project management tools like Jira
These integrations ensure continuous security testing and facilitate collaboration between development and security teams.
Reporting and Remediation Guidance
Web application security testing must provide rich and insightful reports to track progress over time and highlight recurring gaps. It is to give you an easy-to-understand view of your website performance once a scanning session is completed. The tool must also produce steps to guide you in addressing the issues raised.
Conclusion
Web application security is a critical component of overall cybersecurity. The rapid evolution of technology, coupled with the increasing sophistication of cyber threats, makes it a complex and ever-changing landscape.
- Secure coding practices: Building security into the application from the ground up.
- Regular security assessments: Identifying vulnerabilities early on.
- Robust testing: Ensuring the application can withstand attacks.
- Strong authentication and authorization: Protecting access to sensitive data.
- Data protection: Implementing measures to safeguard sensitive information.
- Incident response planning: Preparing for the inevitable security breach.
- Staying informed: Keeping up with the latest threats and countermeasures.
Collaboration between development, security, and operations teams is crucial for effective web application security. By working together, organizations can create a more resilient security posture.
FAQs
Web application security is crucial to protecting data, customers, and organizations from data theft, interruptions in business continuity, or other harmful results of cybercrime.
A number of different teams within an organization could be responsible for cloud security: the network team, security team, apps team, compliance team or the infrastructure team