What is critical infrastructure?
Critical infrastructure is the collection of systems, networks and public works that a government considers essential to its functioning and safety of its citizens. The specific infrastructure that each nation considers critical varies. It usually includes electrical grids, public services and communication systems. Special attention must be given to protect critical infrastructure from cyber attacks.
Critical infrastructure cybersecurity
Critical infrastructure is important to day-to-day life and the safety of civilians. Protecting it is becoming more and more important as malicious actors are increasingly targeting critical infrastructure. These attacks can come from ransomware gangs trying to extort money or advanced persistent threat groups attempting to disrupt another country’s operations.
There have been examples where a cyber attack has impacted a nation’s critical infrastructure. Smaller incidents may only leak information, as with cyberespionage. Larger attacks could severely impact operations. Attacks on hospitals have even sadly resulted in the loss of life.
Why Is Critical Infrastructure security Important?
Critical infrastructure, encompassing power grids, water supply, transportation, and communication networks, is the lifeblood of modern society. Its security is paramount as disruptions can have far-reaching consequences. A cyberattack or physical damage to these systems can lead to widespread power outages, economic losses, and supply chain disruptions.
Beyond economic impacts, critical infrastructure security is a matter of national security.
How Do We Protect And Manage Risks to Critical Infrastructure?
The responsibility for protecting critical infrastructures lies with the Cybersecurity and Infrastructure Security Agency (CISA), a DHS agency that Congress created in November 2018. The agency leads the coordinated national effort to protect critical infrastructure, with three key aims:
Managing the risk faced by critical infrastructure
Critical infrastructure risk is managed by the National Risk Management Center (NRMC), which is an entity within CISA. NRMC aims to identify and address the biggest risks that the U.S.’s critical infrastructure faces through analysis, planning, and collaboration. It does this by identifying and prioritizing the most significant risks that critical infrastructure faces and taking actions that will mitigate the risks.
Enhancing the security of critical infrastructure
Improving security is fundamental to protecting critical infrastructure. This includes enhancing physical security, such as ensuring doors are locked and placing effective fences to protect buildings. It also includes deploying effective cybersecurity solutions to protect organizations’ networks, systems, and users, as well as identifying and addressing their virtual vulnerabilities. Organizations also must practice good cyber hygiene by preventing the use of weak passwords, patching vulnerabilities, and avoiding phishing scams and malware attacks.
Enhancing the resilience of critical infrastructure
Critical infrastructure needs to be resilient to changing conditions, as well as withstand and recover from disruption. This means strength against physical and cyber threats, which require a comprehensive cybersecurity defense program.
Advantages of Critical Infrastructure Security
Critical infrastructure security offers a multitude of benefits that extend far beyond preventing disruptions.
- Economic Prosperity: A secure critical infrastructure is a cornerstone of economic growth. It fosters investor confidence, enables efficient operations, and minimizes costly downtime due to attacks or failures.
- Public Safety and Well-being: By safeguarding essential systems like power grids, water supply, and healthcare, critical infrastructure security directly protects public health and safety. It ensures the availability of essential services during emergencies and reduces the risk of widespread harm.
- National Security: A resilient critical infrastructure is a vital component of national security. It prevents adversaries from using critical systems as weapons, safeguards sensitive information, and maintains the continuity of government operations.
- Risk Mitigation: Proactive security measures help identify vulnerabilities and implement countermeasures, reducing the likelihood and impact of cyberattacks, natural disasters, and other threats.
- Global Competitiveness: A secure and reliable critical infrastructure enhances a nation’s global competitiveness by attracting businesses and investments. It demonstrates a commitment to safety, resilience, and innovation.
In essence, investing in critical infrastructure security is an investment in the overall well-being of a society, protecting lives, livelihoods, and national interests.
Disadvantages of Critical Infrastructure Security
While the benefits of critical infrastructure security are substantial, there are also challenges and potential drawbacks:
- High Costs: Implementing and maintaining robust security measures can be expensive, requiring significant investments in technology, personnel, and training.
- Operational Challenges: Enhanced security measures can sometimes introduce complexities and slow down operations, potentially affecting efficiency and productivity.
- False Positives: Security systems may generate false alarms, leading to unnecessary disruptions and investigations.
- Regulatory Burden: Compliance with security regulations can be time-consuming and resource-intensive, adding administrative overhead.
- Talent Shortage: Finding and retaining skilled cybersecurity professionals can be difficult, especially in specialized areas related to critical infrastructure.
- Balancing Security and Accessibility: Striking the right balance between security and accessibility is challenging, as excessive security measures can hinder legitimate users.
- Emerging Threats: The constantly evolving threat landscape requires continuous adaptation and investment, making it difficult to stay ahead of cybercriminals.
It’s essential to weigh these challenges against the potential consequences of a security breach to determine the optimal level of investment and protection for critical infrastructure.
Critical infrastructure in the United States
The United States government gives the following explanation for critical infrastructure:
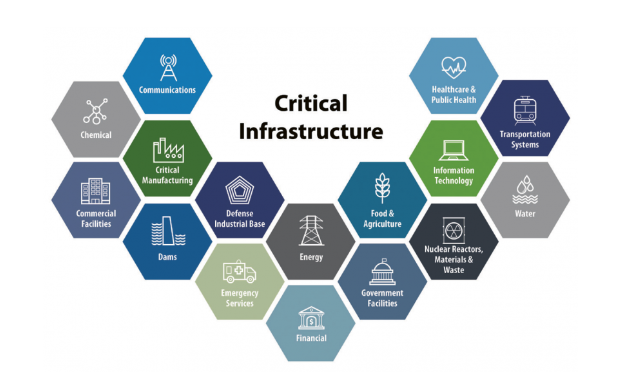
There are 16 critical infrastructure sectors whose assets, systems and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof.
- Chemical
- Commercial facilities
- Communications
- Critical manufacturing
- Dams
- Defense industrial base
- Emergency services
- Energy
- Financial services
- Food and agriculture
- Government facilities
- Healthcare and public healt
Chemical sector
Overseen by the Department of Homeland Security (DHS), it covers the manufacturing, storage, transportation and use of potentially dangerous chemicals. It includes base chemicals, specialty chemicals, agricultural chemicals and consumer products.
Commercial facilities sector
Overseen by DHS, it has eight subsectors: entertainment and media, gaming, lodging, outdoor events, public assembly, real estate, retail and sports leagues.
Communications sector
Overseen by DHS, it covers privately owned communications infrastructure, including satellite, terrestrial, wireless communications and the internet.
Critical manufacturing sector
Overseen by DHS, it includes manufacturing that has national significance. The subsectors include primary metals manufacturing; machinery manufacturing; electrical equipment, appliance and component manufacturing; and transportation equipment manufacturing.
Dams sector
Overseen by DHS, it includes water retention and control services.
Defense industrial base sector
Overseen by the Department of Defense, it includes research, design, production and maintenance of military weapons systems.
Emergency services sector
Overseen by DHS, it includes emergency management, emergency medical services, fire and rescue services, law enforcement, public works and other specialty emergency services.
Energy sector
Overseen by the Department of Energy, it covers the production and distribution of electricity, oil and natural gas.
Financial services sector
Overseen by the Department of the Treasury, it covers banks, credit unions, insurance companies and investment institutions. It protects the ability to deposit, withdraw, loan, invest and transfer funds.
Food and agriculture sector
Overseen by the Department of Agriculture and the Department of Health and Human Services (HHS), it includes farms, restaurants and food manufacturing.
Government facilities sector
Overseen by DHS and the General Services Administration, it covers federal, state, local and tribal government facilities. It includes government offices, embassies, courthouses, schools, national monuments and election facilities.
Healthcare and public health sector
Overseen by HHS, it helps to protect against infectious disease, infectious disease outbreaks and terrorism.
Critical Infrastructure Protection
Critical infrastructure protection (CIP) is the process of securing the infrastructure of organizations in critical industries. It ensures that the critical infrastructures of organizations in industries like agriculture, energy, food, and transportation receive protection against cyber threats, natural disasters, and terrorist threats.
CIP typically involves securing critical infrastructures such as supervisory control and data acquisition (SCADA) systems and networks, as well as industrial control systems (ICS) and operational technology (OT). Popular CIP solutions from Fortinet include SCADA for securing critical infrastructure and OT for critical infrastructure protection.
CIP Technologies For Enterprises
Many of the critical infrastructure protection examples discussed above use the following enterprise technologies:
- Deep CDR: Content disarm and reconstruction (CDR) disassembles a file into its constituent parts and eliminates any potential threats.
- Proactive DLP: Data loss prevention technology (DLP) protects sensitive information via metadata removal, automatic document redaction, or watermark addition rather than blocking files.
- Multiscanning: Multiscanning technology makes anti-malware solutions resilient and significantly enhances malware detection rates and outbreak detection times.
- File-based vulnerability: This technology searches for flaws in files and applications before they are installed, so IT teams can fix any vulnerabilities.
- Threat intelligence: To avoid malware outbreaks or stop them, threat intelligence analyzes malicious patterns, making it easier to identify threats.
- Sandbox: Sandboxes run untested code and third-party software in an environment that has no access to the company’s network. They can also be used to contain threats in a safe, insulated environment, enabling you to observe how they behave.
- Endpoint compliance: This enables enterprises to identify, evaluate, and correct applications that do not adhere to established operational and security regulations.
- Endpoint vulnerability assessment: This ensures that all programs are running with the most recent versions, strengthening endpoint security. Automatic patching can quickly fix vulnerabilities after they have been found.
- Malware detection on endpoints: This evaluates an endpoint for any suspicious activity by checking the libraries and processes that are running.
- Endpoint application removal: This enables the removal of security solutions, including antivirus software and firewalls, that are not appropriate or approved for the work environment. It can remove potentially unwanted applications (PUA) as well.
Challenges in Critical Infrastructure Security
Securing critical infrastructure is a complex task fraught with challenges. Here are some of the most significant:
Technological Challenges
- Legacy Systems: Many critical infrastructure systems are built on outdated technologies, making them vulnerable to modern threats. Upgrading these systems is often costly and disruptive.
- Interconnectedness: Critical infrastructure components are highly interconnected, creating a complex attack surface. A breach in one system can cascade to others.
- IoT Devices: The increasing number of IoT devices in critical infrastructure introduces new vulnerabilities and attack vectors.
- Supply Chain Risks: The global supply chain for critical components can be compromised, leading to vulnerabilities in the final product.
Human Factors
- Skill Shortages: There is a global shortage of cybersecurity professionals with expertise in critical infrastructure protection.
- Awareness and Training: Many employees in critical infrastructure sectors lack adequate cybersecurity awareness and training.
- Insider Threats: Employees with authorized access can pose significant risks due to negligence, malice, or coercion.
Organizational and Regulatory Challenges
- Risk Assessment: Identifying and prioritizing risks in complex systems is challenging.
- Cost and Resource Constraints: Securing critical infrastructure requires substantial investments, often exceeding available budgets.
- Regulatory Compliance: Adhering to multiple, often conflicting regulations can be burdensome and costly.
- Public-Private Partnerships: Effective collaboration between government and private sector entities is essential but often hindered by bureaucracy and differing priorities.
Threat Landscape
- Advanced Persistent Threats (APTs): Highly sophisticated and persistent attackers target critical infrastructure with advanced techniques.
- Cyber Warfare: Nation-state actors pose significant threats, targeting critical infrastructure for strategic advantage.
- Emerging Threats: New threats, such as ransomware and supply chain attacks, continually evolve.
Addressing these challenges requires a multifaceted approach involving technology, people, processes, and collaboration.
Why Does Critical Infrastructure Security Matter?
Critical infrastructure often encompasses industrial control systems (ICS), including supervisory control and data acquisition (SCADA) systems, which are used to automate industrial processes in critical infrastructure industries. Attacks against SCADA and other industrial control systems are serious concerns. They have the potential to create wide-scale compromise in vital systems, such as transportation, oil and gas supply, electrical grids, water distribution, and wastewater collection.
The connections and interdependencies between infrastructure systems and sectors mean that, if one or more functions fail or experiences a blackout, there can be an immediate, negative impact on multiple sectors.
Cybercriminals have learned they can extract substantial ransoms from their victims, and nation-states can more effectively bully rival countries with demonstrations of their cyberwarfare capabilities.
Challenges to Securing Control Systems in Critical Infrastructure
This factor, combined with rising threat and regulatory landscapes, has increased the burden for organizations trying to secure their critical infrastructure. Some of these challenges include:
- Gaining granular visibility over operational network traffic at the application and user levels to validate proper or anomalous use.
- Segmenting networks with sufficient access controls to limit extraneous and internal attack vectors while meeting stringent performance requirements, such as ISA 62443.
- Protecting unpatched commercial off-the-shelf (COTS) systems from known cyberthreats and reducing downtime due to cyber incidents or patching.
- Preventing advanced cyberattacks, which utilize zero-day methods to disrupt production, compromise information integrity or exfiltrate intellectual property.
- Managing disjointed, distributed network and endpoint security products.
- Securing unmanaged, unsecured IoT and connected devices.
- Complying with regulations such as NERC CIP, TSA Security Directives and NIST CSF as well as efficiently providing information for audits.
- Insuring operations and security of remote outside plant environments with security solutions ruggedized and compliant for a wide range extreme conditions.
Understanding Cyber Security in Critical Infrastructure
The Cybersecurity features of critical infrastructure have rapidly emerged in a digital society and are doing more on online networks. Present-time civilization is largely based on a variety of networks and computer systems in which power supply systems, transportation infrastructure, hospitals, banks, and other institutions of the financial systems operate.
The hard practice of cyber security has another side of vulnerability wherein the dependence on digital technology may lead to a broken cyber defense system becoming one of the targets for cybercriminals. Cybersecurity in critical infrastructure is not only about technicality but it is a matter of historic priority to shrink the chances of economic crisis, public disorder, and national threat.
Cyber Security in Critical Infrastructure Threat Landscape
Cyber threats may compromise critical infrastructure and can come in many different forms, such as:
- Cyber Warfare: Cyber threats could be launched by states and actors granted state support to implement espionage, launching cyberattacks that collapse critical services or destroy advisory systems.
- Cyber Terrorism: Cyber terrorist groups and other non-state actors can engage in such attacks to create a sense of chaos, terror, and fear.
- Cyber Crime: Bypassing security systems poses an appealing opportunity, as organized crime groups exploit vulnerabilities in critical infrastructures to steal or demand money, or to produce service interruptions.
- Insider Threats: Insiders who are evil-minded or employees who are negligent with care are very close to serious risks. They can access vital systems by either exploiting some vulnerabilities or unintentionally leading to security lapses.

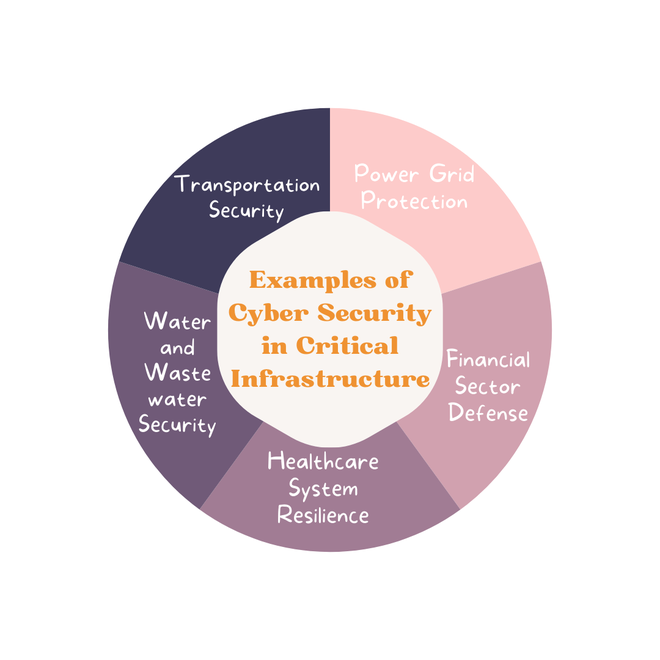
Examples of Cyber Security in Critical Infrastructure
- Transportation Security: The incorporation of encryption methods to protect military traffic management and communication networks such as the ones used in air, rail, and waterway transportation is a good example of cybersecurity in critical infrastructure, through adopting biometric authentication methods and using restrictions to prohibit unauthorized people from coming into critical assets such as airports and harbors.
- Power Grid Protection: Cyber security of critical infrastructure is a major need for power grid systems provided by electrical systems. Among these will be the installation of new types of firewalls and IDS (intrusion detection systems) that will have the ability to defend against online attacks that attempt network accesses with the intent to compromise power distribution, transmission, and generation infrastructure. Automated anomaly detection and traffic network monitoring also allow the detection of cyber breaches ahead of time, penetration testing, and vulnerability assessments,
Best Practices for Critical Infrastructure Security
Securing critical infrastructure is a complex challenge, but adhering to best practices can significantly enhance protection. Here are some key strategies:
Risk Assessment and Management
- Comprehensive Risk Assessment: Identify, assess, and prioritize potential threats and vulnerabilities.
- Risk Mitigation: Develop and implement strategies to reduce or eliminate identified risks.
- Business Continuity Planning: Create plans for maintaining essential functions in case of disruptions.
Technological Controls
- Network Segmentation: Isolate critical systems and data to limit the impact of a breach.
- Access Control: Implement strong access controls, including multi-factor authentication and role-based access.
- Cybersecurity Hygiene: Follow fundamental security practices like patching, antivirus, and intrusion detection.
- Data Protection: Encrypt sensitive data, both at rest and in transit.
- Incident Response Planning: Develop and test incident response plans to minimize damage and recovery time.
Human Factors
- Employee Training: Provide regular cybersecurity awareness training to employees.
- Security Culture: Foster a strong security culture within the organization.
- Insider Threat Mitigation: Implement measures to prevent and detect insider threats.
Collaboration and Information Sharing
- Information Sharing: Participate in information sharing initiatives to learn from others and share threat intelligence.
- Public-Private Partnerships: Collaborate with government agencies and industry peers to address shared challenges.
- Regulatory Compliance: Adhere to relevant industry standards and regulations.
Emerging Technologies
- Artificial Intelligence and Machine Learning: Utilize AI and ML for threat detection and response.
- Cybersecurity Automation: Automate routine security tasks to improve efficiency and reduce human error.
By implementing these best practices, organizations can significantly enhance the security of critical infrastructure, protecting against a wide range of threats.
Conclusion
Critical infrastructure security is imperative for the functioning of modern society. Its protection is essential to safeguard economic prosperity, public safety, and national security. While challenges such as technological complexities, human factors, and evolving threats persist, a comprehensive and proactive approach is vital.
By combining robust technological controls, effective risk management, strong human factors considerations, and collaborative partnerships, organizations can significantly enhance the resilience of critical infrastructure. Continuous adaptation to emerging threats and the integration of new technologies will be crucial in maintaining a secure and reliable critical infrastructure ecosystem.
Ultimately, the protection of critical infrastructure is a shared responsibility that requires collaboration between government, industry, and the public to create a more secure and resilient future.
FAQs
Securing critical infrastructure is vital to ensuring the American people have access to services like drinking water, electricity, and food. It is also crucial to protecting high-value industries from cyberattacks, such as the chemical, communications, emergency services, healthcare, information technology, and transportation sectors.
In terms of cybersecurity, critical infrastructure can be termed as those complex interconnected ecosystem which includes assets, systems, and networks that gives us the necessary functions which are required for our way of life such as transportation and communication systems, water and power lines, etc.
Major threats to critical infrastructure include cyber warfare, cyber terrorism, cyber crime, and insider threats. Cyber threats in critical infrastructure is mainly classified into three different categories such as natural threats which includes the hazards like earthquake and tsunami, Human-caused threats that includes cyber attacks, rioting, explosions and bombing .