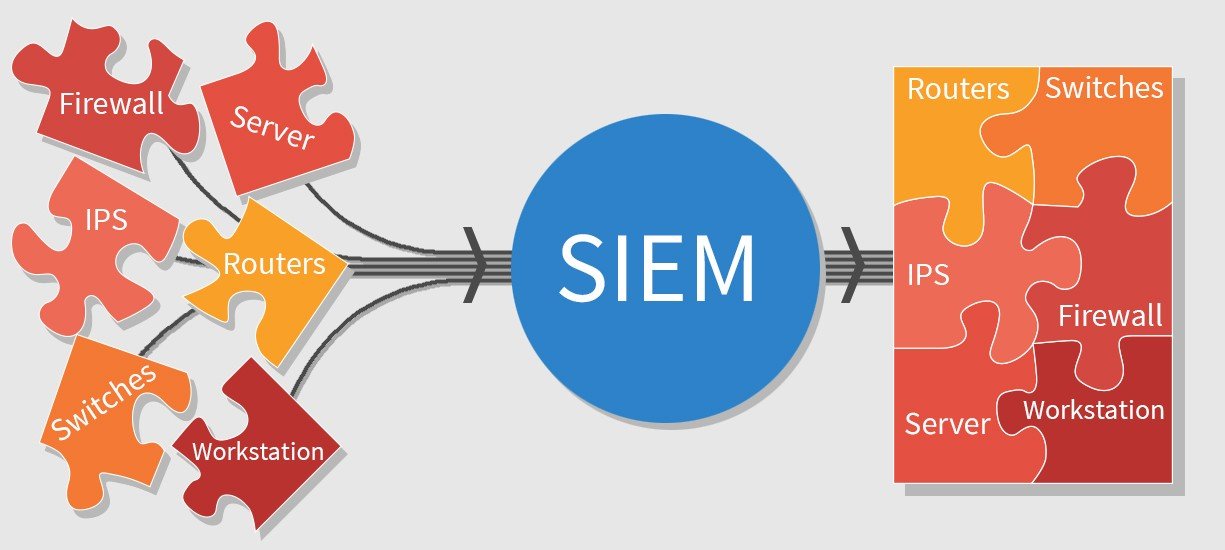
The security information and event management (SIEM) “an approach to security management that combines SIM (security information management) and SEM (security event management) functions into one security management system.”
Security information and event management systems address the three major challenges that limit rapid incident response:
- The vast amount of unaggregated security data makes it hard to see what’s happening and prioritize threats.
- IT teams are understaffed/undertrained due to the cybersecurity skills gap.
- The need to demonstrate compliance takes time away from threat identification and response.
How does SIEM work?
SIEM tools gather event and log data created by host systems throughout a company’s infrastructure and bring that data together on a centralized platform. Host systems include applications, security devices, antivirus filters and firewalls. SIEM tools identify and sort the data into categories such as successful and failed logins, malware activity and other likely malicious activity.
The SIEM software generates security alerts when it identifies potential security issues. Using a set of predefined rules, organizations can set these alerts as a low or high priority.
Why Is SIEM Important?
SIEM systems are critical for organizations mitigating an onslaught of threats. With the average organization’s security operations center (SOC) receiving more than 10,000 alerts per day, and the biggest enterprises seeing over 150,000, most enterprises do not have security teams large enough to keep up with the overwhelming number of alerts. However, the growing risk posed by ever more sophisticated cyber threats makes ignoring alerts quite dangerous. A single alert may mean the difference between detecting and thwarting a major incident and missing it entirely. SIEM security delivers a more efficient means of triaging and investigating alerts. With SIEM technology, teams can keep up with the deluge of security data.
Security information and event management (SIEM) solutions collect logs and analyze security events along with other data to speed threat detection and support security incident and event management, as well as compliance. Essentially, a SIEM technology system collects data from multiple sources, enabling faster incident response to threats. If an anomaly is detected, it might collect more information, trigger an alert, or quarantine an asset.
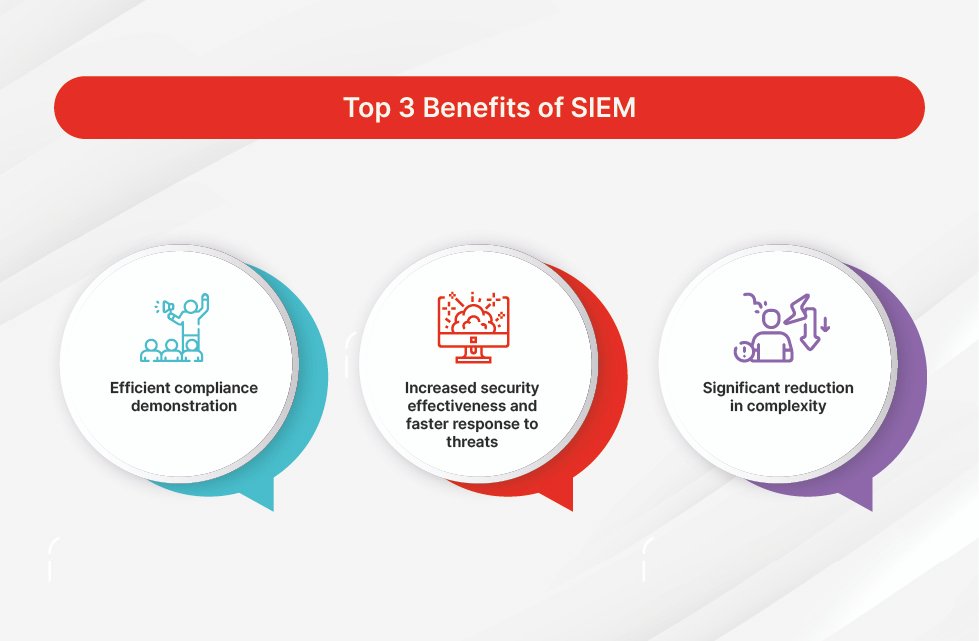
Benefits of SIEM
Benefits of SIEM include the following:
- It shortens the time it takes to identify threats significantly, minimizing the damage from those threats.
- SIEM offers a holistic view of an organization’s information security environment, making it easier to gather and analyze security information to keep systems safe. All an organization’s data goes into a centralized repository where it’s stored and easily accessible.
- Companies can use SIEM for a variety of use cases that revolve around data or logs, including security programs, audit and compliance reporting, help desk and network troubleshooting.
- SIEM supports large amounts of data so organizations can continue to scale out and add more data.
- SIEM provides threat detection and security alerts.
SIEM Features and Capabilities
Alerting – Analyzes events and helps escalate alerts to notify security staff of immediate issues, either by email, other types of messaging, or via security dashboards.
Dashboards and Visualizations – Creates visualizations to allow staff to review event data, see patterns, and identify activity that does not conform to standard processes or event flows.
Compliance – Automates the gathering of compliance data, producing reports that adapt to security, governance and auditing processes for standards like HIPAA, PCI/DSS, HITECH, SOX, and GDPR.
Retention – Stores long-term historical data to enable analysis, tracking, and reporting for compliance requirements. Especially important in forensic investigations, which can occur long after the fact.
Incident Response – Provides case management, collaboration, and knowledge sharing around security incidents, allowing security teams to quickly synchronize on the essential data, communicate, and respond to a threat.
SOC Automation – Integrates with other security solutions using APIs, and lets security staff define automated playbooks and workflows that should be executed in response to specific incidents.
Next-Gen SIEM Capabilities
SIEM is a mature technology and the next generation of SIEMs provide new capabilities:
- User and entity behavior analytics in advanced SIEMs go beyond rules and correlations, leveraging AI and deep learning techniques to look at patterns of human behavior. This can help detect insider threats, targeted attacks, and fraud.
- Security orchestration and automation response Next-gen SIEMs integrate with enterprise systems and automate incident response. For example, the SIEM may detect an alert for ransomware and perform containment steps automatically on affected systems, before the attacker can encrypt the data, while simultaneously creating communications or other notifications.
New SIEM platforms provide additional advanced capabilities such as:
Automated incident response – Once a SIEM detects a certain type of security event, it can execute a pre-planned sequence of actions to contain and mitigate the incident. SIEMs are becoming full security orchestration and automation response (SOAR) tools.
Complex threat identification – Correlation rules can’t capture many complex attacks, because they lack context, or can’t respond to new types of incidents. With automatic behavioral profiling, SIEMs can detect behavior that suggests a threat.
Detection without rules or signatures – Many threats facing your network can’t be captured with manually-defined rules or known attack signatures. SIEMs can use machine learning to detect incidents without pre-existing definitions.
Lateral movement – Attackers move through a network by using IP addresses, credentials, and machines, in search of key assets. By analyzing data from across the network and multiple system resources, SIEMs can detect this lateral movement.
Entity behavior analysis – Critical assets on the network such as servers, medical equipment or machinery have unique behavioral patterns. SIEMs can learn these patterns and automatically discover anomalies that suggest a threat.
Choosing A SIEM Vendor: Your Buying Guide
“The global security information and event management market accounted for $2.59B in 2018 and is expected to grow at a CAGR of 10.4% during the forecast period 2019 – 2027, to $6.24B by 2027,” according to a recent SIEM report by Research and Markets.
This fast-growing market feeds a lot of competition, so it’s important to know what to look for in a security information and event management solution. At the very least, a SIEM solution must be able to:
- Collect data from every security device
- Aggregate, correlate, and analyze the data
- Automate wherever possible
- Monitor business services, not just devices
For more details on what really matters when selecting a SIEM solution, read the eBook.
Most organizations will want more than just basic functionality from a security information and event management solution. The following checklist provides guidance on specific features that will maximize return on investment (ROI):
SIEM tools and software
There are a wide variety of SIEM tools on market, but the following is just a sample:
SolarWinds Security Event Manager. The SolarWinds Security Event Manager SIEM tool automatically detects threats, monitors security policies and protects networks. The tool offers features such as integrity monitoring, compliance reporting and centralized log collection.
Splunk. Splunk is an on-premises SIEM system that supports security monitoring and offers continuous security monitoring, advanced threat detection, incident investigation and incident response.
IBM QRadar. The IBM QRadar SIEM platform provides security monitoring for IT infrastructures. It features log data collection, threat detection and event correlation.
LogRhythm. LogRhythm is a SIEM system for smaller organizations. It unifies Log Management, network monitoring and endpoint monitoring, as well as forensics and security analytics.
Exabeam. Exabeam Inc.’s SIEM portfolio offers a data lake, advanced analytics and a threat hunter.
NetWitness. The RSA NetWitness platform is a threat detection and response tool that includes data acquisition, forwarding, storage and analysis.
Datadog Cloud SIEM. Datadog Cloud SIEM from Datadog Security is a cloud-native network and management system. The tool features both real-time security monitoring and log management.
Log360. The Log360 SIEM tool offers threat intelligence, incident management and SOAR features. Log collection, analysis, correlation, alerting and archiving features are available in real time.

SIEM Use Cases
Security monitoring
SIEMs help with real-time monitoring of organizational systems for security incidents. A SIEM provides a unique perspective on security incidents because it has access to multiple data sources — for example, it can combine alerts from an intrusion detection system (IDS) with information from an antivirus (AV)product and authentication logs. It helps security teams identify security incidents that no individual security tool can see, and helps them focus on alerts from security tools that have special significance.
Advanced threat detection
SIEMs can help detect, mitigate, and prevent advanced threats, including:
- Malicious insiders – A SIEM can use browser forensics, network data, authentication, and other data to identify insiders planning or carrying out an attack.
- Data exfiltration (sensitive data illicitly transferred outside the organization) – A SIEM can pick up data transfers that are abnormal in their size, frequency, or payload.
- Outside entities, including advanced persistent threats (APTs) – A SIEM can detect early warning signals indicating that an outside entity is carrying out a focused attack or long-term campaign against the organization.
Forensics and incident response
SIEMs can help security analysts determine that a security incident is taking place, triage the event, and define immediate steps for escalation and remediation.
Even if an incident is known to security staff, it takes time to collect data to fully understand the attack and stop it — the SIEM can automatically collect this data and significantly reduce response time. When security staff discovers a historic breach or security incident that needs to be investigated, SIEMs provide rich forensic data to help uncover the kill chain, threat actors, and mitigation.
Compliance reporting and auditing
SIEMs can help organizations prove to auditors and regulators that they have the proper safeguards in place and that security incidents are known and contained.
Many early adopters of SIEMs used it for this purpose: aggregating log data from across the organization and presenting it in audit-ready format. Modern SIEMs automatically provide the monitoring and reporting necessary to meet standards like HIPAA, PCI/DSS, SOX, FERPA, and HITECH.
The Future of SIEM
Companies usually will express two primary concerns regarding the ability of their existing technologies to handle cybersecurity threats now and in the future. First, SIEM solutions don’t usually support very large workloads (i.e., big data) and struggle to handle the large numbers of alerts and contextual data required. Second, most tools that detect, investigate, and respond to threats are unintuitive.
How to choose the right SIEM product
The key to selecting the right SIEM tool varies depending on a number of factors, including an organization’s budget and security posture. However, companies should look for SIEM tools that offer the following capabilities:
- compliance reporting;
- incident response and forensics;
- database and server access monitoring;
- internal and external threat detection;
- real-time threat monitoring, correlation and analysis across a variety of applications and systems;
- an intrusion detection system, IPS, firewall, event application log, and other application and system integrations;
- threat intelligence
Challenges of SIEM
SIEM (Security Information and Event Management) is a powerful tool for cybersecurity, but it comes with its own set of challenges. Let’s explore some of the common ones:
Data Volume and Complexity
- Massive data ingestion: SIEMs process enormous amounts of data from various sources, which can be overwhelming.
- Data normalization: Transforming data into a usable format can be complex and time-consuming.
- Data retention: Deciding how long to retain data for compliance and investigation purposes is a challenge.
Alert Fatigue
- Excessive alerts: Too many alerts can lead to analysts becoming overwhelmed and missing critical incidents.
- False positives: Incorrectly identified threats can waste valuable time and resources.
- Prioritization: Determining which alerts require immediate attention is difficult.
Skill Gap
- SIEM expertise: Finding skilled professionals to manage and analyze SIEM data is challenging.
- Continuous learning: The cybersecurity landscape is constantly evolving, requiring constant training and updates.
Cost
- High implementation costs: SIEM solutions can be expensive to purchase, deploy, and maintain.
- Ongoing expenses: Licensing, hardware, and personnel costs continue after implementation.
Integration Challenges
- Data source compatibility: Integrating data from different sources can be complex.
- API limitations: Some data sources may have limited API capabilities, hindering data collection.
Compliance Requirements
- Data retention policies: Meeting regulatory requirements for data retention can be challenging.
- Incident response: Ensuring compliance with incident response procedures is crucial.
False Negatives
- Missed threats: Failing to detect actual threats can have severe consequences.
- Rule tuning: Fine-tuning SIEM rules to reduce false negatives is time-consuming and requires expertise.
Evolution of Threats
- Adapting to new threats: SIEM solutions must be updated to detect emerging threats.
- Threat intelligence integration: Incorporating threat intelligence data is essential for effective threat hunting.
Overcoming These Challenges
While SIEMs present challenges, there are strategies to mitigate them:
- Data management: Implement data normalization, classification, and retention policies.
- Alert management: Use advanced analytics, correlation rules, and prioritization techniques.
- Skill development: Invest in training and certifications for SIEM analysts.
- Cost optimization: Consider cloud-based SIEMs, managed services, and cost-effective hardware.
- Integration strategies: Develop a comprehensive integration plan and use data connectors.
- Compliance framework: Establish a robust compliance framework and conduct regular audits.
- Threat intelligence: Leverage threat intelligence feeds to enhance threat detection.
By addressing these challenges proactively, organizations can maximize the benefits of their SIEM investment and improve their overall security posture.
SIEM Solutions
SIEM has become a basic component of cybersecurity. However, not all SIEM solutions are created equal. When deciding on which SIEM to adopt, it is important to keep in mind that SIEM is not an isolated solution but should be part of a larger security strategy. Some of the top SIEM solutions are listed below.
Exabeam Fusion
As a next-gen SIEM, Exabeam Fusion is a cloud-delivered solution that uses a behavior-based approach for Threat Detection, Investigation, and Response (TDIR). By aggregating all relevant events and weeding out illegitimate events, Fusion SIEM boosts analyst productivity and detects threats missed by other tools. This improves detection rates and response time, and ensures that all alerts are considered — even those coming from “noisy” systems that generate many alerts.
Splunk
Splunk has a popular SIEM solution. What sets it apart from other vendors is its ability to handle both security as well as application and network monitoring use cases. This makes it popular with both security personnel as well as IT operations users. Like most top SIEM solutions, Splunk’s SIEM provides information in real time, and the user interface is relatively user-friendly. Pricing is based on workloads protected.
LogRhythm
LogRhythm is a pioneer of SIEM and earned itself a solid reputation. Log Rythm ’s solution also incorporates many analytical tools, as well as incorporating AI and log correlation. While integrating with LogRhythm is relatively hassle-free, there is a steeper learning curve as it is not considered as user-friendly as other SIEMs.
IBM QRadar SIEM
IBM QRadar SIEM allows you to view your IT infrastructure in real time. It is a modular architecture that facilitates the detection and prioritization of threats. It supports multiple logging protocols and offers various configuration-side options, as well as high-end analytics. The solution provides an app store where customers can download additional IBM and 3rd party content to use with QRadar.
SIEM and PCI DSS compliance
SIEM tools can help an organization become PCI DSS compliant. This security standard reassures a company’s customers that their credit card and payment data will remain safe from theft or misuse.
A SIEM can meet the following PCI DSS requirements:
- Unauthorized network connection detection – PCI DSS compliant organizations need a system that detects all unauthorized network connections to/from an organization’s IT assets. A SIEM solution can be used as such a system.
- Searching for insecure protocols – A SIEM is able to document and justify the use of an organization’s permitted services, protocols and ports, as well as document security features implemented for insecure protocols.
- Inspect traffic flows across DMZ – PCI compliant organizations need to implement a DMZ that manages connections between untrusted networks (e.g., the internet) and a web server. Additionally, inbound internet traffic to IPs within the DMZ need to be limited while outgoing traffic dealing with cardholder details must be evaluated.
How to Choose a SIEM Provider
All the SIEM systems we listed above are robust solutions with a broad user base. When selecting a SIEM, evaluate the vendor’s track record and market position, and pay special attention to functionality.
Core SIEM Capabilities
- Threat detection – SIEMs provide accurate threat detection with the aid of rules and behavior analytics. They also aggregate threat feeds, backlists and geolocations.
- Threat intelligence and security alerting – many SIEMs connect your security system to a threat intelligence feed. This ensures your business is up to date on the latest cyber threats. SIEMs also aggregate and normalize your security data, cross-checking various sources, assessing your system activity, and alerting you anytime they identify a suspicious event.
- Compliance assessment and reporting – compliance is one of the biggest hurdles for any business, and it is only getting more complex. Regulations such as FFIEC, HIPAA and PCI, define how and what data needs to be stored. Failing to meet regulatory requirements can have catastrophic results for a business.
Best practices to implementing SIEM
Follow these best practices while implementing SIEM:
- Set understandable goals. The SIEM tool should be chosen and implemented based on security goals, compliance and the potential threat landscape of the organization.
- Apply data correlation rules. Data correlation rules should be implemented across all systems, networks and cloud deployments so data with errors in it can be more easily found.
- Identify compliance requirements. This helps ensure the chosen SIEM software is configured to audit and report on correct compliance standards.
- List digital assets. Listing all digitally stored data across an IT infrastructure aids in managing log data and monitoring network activity.
- Record incident response plans and workflows. This helps ensure teams can respond to security incidents rapidly.
- Assign a SIEM administrator. A SIEM administrator ensures the proper maintenance of a SIEM implementation.

Conclusion
SIEM (Security Information and Event Management) has evolved into an indispensable tool for organizations navigating the complex and ever-evolving threat landscape. By aggregating, correlating, and analyzing vast volumes of security data, SIEM empowers security teams to detect threats promptly, respond effectively, and maintain compliance.
While challenges such as data overload, alert fatigue, and skill shortages persist, the benefits of a well-implemented SIEM are undeniable. It provides enhanced visibility into the IT environment, accelerates incident response, improves compliance posture, and ultimately strengthens an organization’s overall security posture.
As technology continues to advance, SIEM solutions are incorporating advanced analytics, machine learning, and automation to address these challenges and deliver even greater value. By investing in skilled personnel, robust data management strategies, and continuous improvement, organizations can harness the full potential of SIEM and build a resilient security architecture.
In conclusion, SIEM is not merely a technology; it’s a strategic asset that empowers organizations to protect their critical assets and maintain business continuity in an increasingly hostile digital world.
FAQs
SIEM solutions collect logs and analyze security events along with other data to speed threat detection and support security incident and event management, as well as compliance.
SIEM technology gathers security-related information from servers, end-user devices, networking equipment, and applications, as well as security devices.