A cyber attack is a set of actions performed by threat actors, who try to gain unauthorized access, steal data or cause damage to computers, computer networks, or other computing systems. A cyber attack can be launched from any location. The attack can be performed by an individual or a group using one or more tactics, techniques and procedures (TTPs).

How Cyber Attacks Work
A cyber attack is an intentional effort to damage, disrupt, or steal data from a computer system or network. It can take many forms, but they all involve exploiting vulnerabilities or tricking users.
1. Phishing:
- How it works: Attackers send emails or messages that appear to be from legitimate sources, often tricking recipients into clicking on malicious links or opening attachments.
- Goal: To steal personal information, login credentials, or infect devices with malware.
2. Malware:
- How it works: Malicious software (like viruses, worms, or ransomware) is introduced to a system, often through phishing or downloads from untrusted sources.
- Goal: To steal data, disrupt operations, or hold systems hostage for ransom.
3. Denial of Service Attacks:
- How it works: Overwhelming a system with traffic, making it unavailable to legitimate users.
- Goal: To disrupt services and cause financial loss.
4. SQL Injection:
- How it works: Attackers inject malicious code into a web application to manipulate databases and steal data.
- Goal: To access sensitive information or compromise the system.
5. Social Engineering:
- How it works: Manipulating people into revealing sensitive information or performing actions that benefit the attacker.
- Goal: To gain unauthorized access or steal data.
6. Brute Force Attacks:
- How it works: Automatically guessing passwords using a combination of characters.
- Goal: To gain access to accounts and systems.
7. Zero-Day Exploits:
- How it works: Exploiting vulnerabilities that are unknown to the software vendor.
- Goal: To gain unauthorized access before patches are released.
Types of Cyber Attacks
While there are thousands of known variants of cyber attacks, here are a few of the most common attacks experienced by organizations every day.
Ransomware
Ransomware is malware that uses encryption to deny access to resources (such as the user’s files), usually in an attempt to compel the victim to pay a ransom. Once a system has been infected, files are irreversibly encrypted, and the victim must either pay the ransom to unlock the encrypted resources, or use backups to restore them.
Malware
There are many types of malware, of which ransomware is just one variant. Malware can be used for a range of objectives from stealing information, to defacing or altering web content, to damaging a computing system permanently.
- Botnet Malware—adds infected systems to a botnet, allowing attackers to use them for criminal activity
- Cryptominers—mines cryptocurrency using the target’s computer
- Infostealers—collects sensitive information on the target’s computer
- Banking trojans—steals financial and credential information for banking websites
- Mobile Malware—targets devices via apps or SMS
- Rootkits—gives the attacker complete control over a device’s operating system
DoS and DDoS Attacks
Denial-of-service (DoS) attacks overwhelm the target system so it cannot respond to legitimate requests. Distributed denial-of-service (DDoS) attacks are similar but involve multiple host machines. The target site is flooded with illegitimate service requests and is forced to deny service to legitimate users. This is because servers consume all available resources to respond to the request overload.
Phishing and Social Engineering Attacks
Social engineering is an attack vector that relies heavily on human interaction, used in over 90% of cyberattacks. It involves impersonating a trusted person or entity, and tricking individuals into granting an attacker sensitive information, transferring funds, or providing access to systems or networks.
MitM Attacks
Man-in-the-Middle attacks are breaches that allow attackers to intercept the data transmitted between networks, computers or users. The attacker is positioned in the “middle” of the two parties and can spy on their communication, often without being detected. The attacker can also modify messages before sending them on to the intended recipient.
Fileless Attacks
Fileless attacks are a new type of malware attack, which takes advantage of applications already installed on a user’s device. Unlike traditional malware, which needs to deploy itself on a target machine, fileless attacks use already installed applications that are considered safe, and so are undetectable by legacy antivirus tools.

What are examples of a cyber attack?
The prevailing cyber attack definition can be very broad, depending on the kind of assault criminals decide to launch. Here are a couple of example scenarios:
- Malware: A company does not take the appropriate cyber attack prevention steps and allows its employees to visit any website they like. An employee goes to a fake site that automatically downloads malware onto their computer. The malware sets up a backdoor for a future ransomware attack.
- Phishing: A phishing email, one of the most common cyber attack types, gets sent to an employee telling them they need to update their bank account password. They are led to a fake site, and a hacker collects all the information they put in.
These cyber attack examples are fairly simple—not the sophisticated types some criminal syndicates unleash—but they are still some of the most common methods malicious actors use to exploit companies and their employees.
How often do cyber attacks occur?
Cyber attacks hit businesses every day. Former Cisco CEO John Chambers once said, “There are two types of companies: those that have been hacked, and those who don’t yet know they have been hacked.” According to the Cisco Annual Cybersecurity Report, the total volume of events has increased almost fourfold between January 2016 and October 2017.
Why Do People Launch Cyber Attacks?
There are many reasons behind the launch of cyber attacks, from financial profit and business intelligence to cyber war and political gain.
- Financial gain: The main reason that people launch cyber attacks is for financial gain. Cyber attacks are typically cheap to create, build, and launch, but offer huge rewards. For example, the average cost of a data breach is a huge $3.86 million, according to a Ponemon Institute and IBM report.
- Business intelligence: Some cyber attacks are more business-motivated, with attackers using techniques like phishing to steal user credentials, infiltrate business networks, and access sensitive business information.
- State-sponsored attacks: Cyber attacks are also launched for political reasons, and many cyber attacks have been traced back to hackers working for nation-states. These include a Russian attack against the Ukrainian power grid in 2016 and the Iranian state-sponsored cyber attack group APT33.
- Hacktivism: Other cyber attacks are launched to raise political awareness, also known as hacktivism. Famous hacktivists, such as Anonymous and WikiLeaks, launch attacks against governments and large organizations to build awareness of various political issues, internet regulation and censorship, and government control.
- Personal reasons: Some cyber attacks are launched for personal reasons, usually by disgruntled or former employees. These individuals will steal sensitive data and sell it for profit or to damage an organization they feel treated them unfairly.
Cyber Threat Actors
In order to respond effectively to a cyberattack, it’s imperative to know the threat actors and understand their tactics, techniques, and procedures.
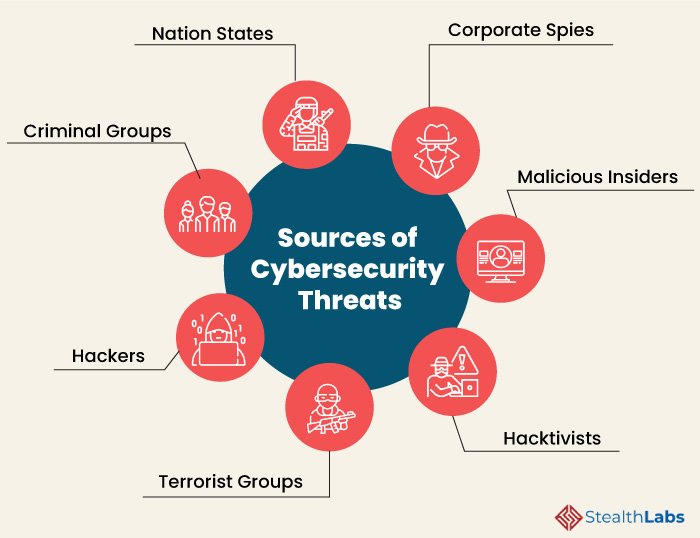
1) Nation States
Cyber attacks by a nation can inflict detrimental impact by disrupting communications, military activities, and everyday life.
2) Criminal Groups
Criminal groups aim to infiltrate systems or networks for financial gain. These groups use phishing, spam, spyware, and malware to conduct identity theft, online fraud, and system extortion.
3) Hackers
Hackers explore various cyber techniques to breach defenses and exploit vulnerabilities in a computer system or network. They are motivated by personal gain, revenge, stalking, financial gain, and political activism. Hackers develop new types of threats for the thrill of challenge or bragging rights in the hacker community.
4) Terrorist Groups
Terrorists conduct cyber attacks to destroy, infiltrate, or exploit critical infrastructure to threaten national security, compromise military equipment, disrupt the economy, and cause mass casualties.
5) Hacktivists
Hacktivists carry out cyberattacks in support of political causes rather than for financial gain. They target industries, organizations, or individuals who don’t align with their political ideas and agenda.
6) Malicious Insiders
97% of surveyed IT leaders expressed concerns about insider threats in cyber security. Insiders can include employees, third-party vendors, contractors, or other business associates who have legitimate access to enterprise assets but misuse that accesses to steal or destroy information for financial or personal gain.
7) Corporate Spies
Corporate spies conduct industrial or business espionage to either make a profit or disrupt a competitor’s business by attacking critical infrastructure, stealing trade secrets, and gaining access.
What to Do When You Suffer a Cyber Security Attack
Recently, the question is not if a cyber security assault will happen, but when. Breach incidents are frequent, take many different shapes, and are worrying for the firms involved. However, organizations can benefit much from other organizations’ experiences that have survived an assault.
Since so many steps are involved in identifying and responding to an attack as rapidly as possible, a real team effort is necessary. The firm must have rules in place prescribing the proper procedure and teaching its staff. Organizations without distinct reporting structures may find themselves in trouble.
An action strategy is essential. This should specify who is in charge of organizing the response and the necessary outside parties. Internally staging fake assaults would help guarantee that stakeholders know their duties.
Cyber Attack Prevention: Common Cybersecurity Solutions
Following are a few security tools commonly deployed by organizations to prevent cyber attacks. Of course, tools are not enough to prevent attacks—every organization needs trained IT and security staff, or outsourced security services, to manage the tools and effectively use them to mitigate threats.
Web Application Firewall
A WAF protects web applications by analyzing HTTP requests and detecting suspected malicious traffic. This may be inbound traffic, as in a malicious user attempting a code injection attack, or outbound traffic, as in malware deployed on a local server communicating with a command and control (C&C) center.
DDoS Protection
A DDoS protection solution can protect a network or server from denial of service attacks. It does this using dedicated network equipment, deployed on-premises by the organization, or as a cloud-based service. Only cloud based services are able to deflect large scale DDoS attacks, which involve millions of bots, because they are able to scale on demand.
Bot Protection
Bots make up a large percentage of Internet traffic. Bots put a heavy load on websites, taking up system resources. While some bots are useful (such as bots that index websites for search engines), others can perform malicious activities. Bots can be used for DDoS, to scrape content from websites, automatically perform web application attacks, spread spam and malware, and more.
Cloud Security
Almost all organizations today manage infrastructure, applications, and data in the cloud. Cloud systems are especially vulnerable to cyber threats, because they are commonly exposed to public networks, and often suffer from a low level of visibility, because they are highly dynamic and running outside the corporate network.
Database Security
Databases typically hold sensitive, mission critical information, and are a prime target for attackers. Securing databases involves hardening database servers, properly configuring databases to enable access control and encryption, and monitoring for malicious activities.
Threat Intelligence
Threat intelligence operates in the background and supports many modern security tools. It is also used directly by security teams when investigating incidents. Threat intelligence databases contain structured information, gathered from a variety of sources, about threat actors, attack tactics, techniques, and procedures, and known vulnerabilities in computing systems.
What to do during a cyber attack
For businesses experiencing a cyber attack, it’s important to act fast. The goals should be to stop the attack and mitigate its impact:
Mobilize your team The first thing to do is mobilize staff who have responsibility for cybersecurity. Ideally, they will have been trained to know how to respond in the event of an attack.
Identify the type of cyber attack Knowing what type of attack is occurring will ensure you know where to focus your attention and how best to contain and recover from the attack. As well as establishing the type of attack, it’s important to understand its likely source, the extent of the attack and its probable impact.
Contain the breachIt’s essential to identify and shut down all access that attackers might have into your systems. With any type of cyber attack, you should move promptly to:
- Disconnect the affected network from the internet
- Disable all remote access to the network
- Re-route network traffic
- Change all vulnerable passwords
The objective should be to prevent attackers from having access to your system. You can then work to return the system to a more secure working condition.
Assess and repair the damage
Once the attack has been contained, you need to determine whether any critical business functions have been compromised, what data may have been affected by the breach, which systems have been accessed, and whether any unauthorized entry points remain.
Report the attack
You may need to report the attack to the proper authorities, which will vary by jurisdiction. If your business has cyber liability insurance, contact your insurance provider for advice on what to do next.
Communicate with customers
It’s likely that you will need to notify customers, especially if the attack has impacted any customer data.

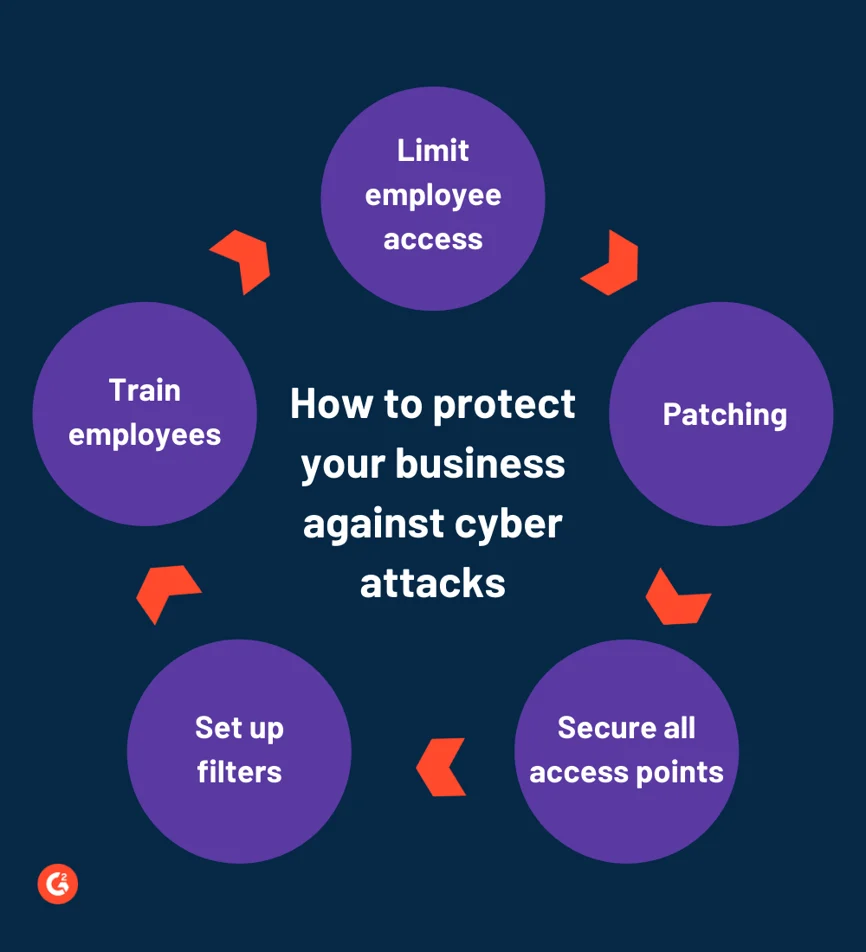
How to protect your business against cyber attacks
Mitigating the cyber threats of an attack calls for more than an anti-virus installation. It needs constant vigilance and awareness. However, it can be simplified by following some cybersecurity best practices.
Limit employee access: Reducing human error chances can be highly beneficial in protecting the remote cases of a data breach. Allow your employees to access only the information that they require for their tasks. If an employee leaves the company or transfers elsewhere, remove all of their information from the systems.
Patch management: It is crucial to patch and update every piece of software on every device used by your employees. Do not delay downloading OS updates, as they usually have enhanced security features.
Secure all networks and access points: Optimize each network and wireless access point for your company’s use. Change the administrative password on new devices, set WAP to avoid broadcasting to SSID, and avoid using WEP.
Effective Strategies to Prevent Cyber Attacks
The prevalence of cyberattacks remains persistent in the modern digital landscape. Cybercriminals persistently enhance their techniques to exploit security vulnerabilities and acquire unauthorized access to sensitive information.
1) Keep Software Up to Date
One of the easiest and most productive ways of protecting to against cyberattacks is to update your software on a regular basis. Software patches that fix security flaws are commonly included within updates.
You can remove potential points of entry for cybercriminals and protect your systems from attacks by immediately installing updates for your operating system, programs, and security tools.
2) Use Strong Passwords and Multifactor Authentication
The first line of defense against unauthorized access is a password. Use a combination of upper- and lowercase letters, numbers, and special characters to create strong passwords for your accounts.
Easy information like your full name or birthdate should be prevented.
3) Educate and Train Employees
Prioritizing employee training and education is an essential approach for avoiding cyberattacks. Employees can learn about the most recent threats and best practices for preventing cyber attacks by taking part in complete cybersecurity awareness programs.
4) Use intrusion detection systems and firewalls
Your inner layer and potential attacks are kept separate by firewalls. Incoming and outgoing network traffic is watched over and filtered, and malicious attempts to gain access are stopped. In order to identify the potential attacks, Intrusion Detection Systems (IDS) analyze network traffic.
Cyber attack trends
Cybercriminals are constantly evolving their tactics, making it crucial for businesses and individuals to stay informed about the latest cyber attack trends.
- Mobile malware: With the increasing use of mobile devices for work and personal activities, cybercriminals are targeting them more frequently with malware designed to steal data, track location, or launch phishing attacks. Businesses should enforce strong mobile security policies for employees.
- Weaponization of artificial intelligence (AI): Attackers are increasingly using AI-powered tools to automate social engineering attacks, analyze vast amounts of data to identify vulnerabilities, and even develop new malware strains. Organizations need to be aware of these potential threats and implement AI-powered security solutions to counter them.
- Internet of Things (IoT) security concerns: The expansion of internet-connected devices (IoT) creates new attack surfaces. Many IoT devices have weak security protocols, making them vulnerable to exploitation. Businesses and consumers need to be cautious about the security of the IoT devices they use.
Conclusion
Cyber attacks are an ongoing and ever-evolving threat. As technology advances, so do the tactics and strategies employed by cybercriminals. The consequences of successful attacks can be severe, ranging from financial loss and data breaches to disruptions in critical infrastructure.
To effectively combat cyber threats, a multifaceted approach is necessary. This includes:
- Strong security measures: Implementing robust firewalls, antivirus software, and intrusion detection systems.
- Regular updates: Keeping software and operating systems up-to-date with the latest security patches.
- User education: Raising awareness among employees and individuals about best practices for online safety, including password management, phishing prevention, and social engineering tactics.
- Incident response planning: Developing and practicing emergency response plans to minimize the impact of cyber incidents.
- International cooperation: Fostering collaboration between governments, businesses, and organizations to address global cyber threats.
The fight against cybercrime is a continuous battle. As new threats emerge, we must adapt our strategies and invest in innovative solutions to protect our digital world. By understanding the nature of cyber attacks and taking proactive measures, we can mitigate risks and build a more resilient online environment.
FAQs
Cyber attacks are much more likely to occur through mundane errors like a user choosing an easy-to-guess password or not changing the default password on something like a router. ‘Phishing’ is also a common way to gain access to a system, this involves extracting personal information under false pretences.
For individuals, cyberattacks can result in identity theft, loss of sensitive personal data, and financial harm. The psychological impact of being a victim of a cyberattack can also lead to a sense of vulnerability and mistrust in digital interactions.