Application security aims to protect software application code and data against cyber threats. You can and should apply application security during all phases of development, including design, development, and deployment.
Use security systems such as firewalls, web application firewalls (WAF), and intrusion prevention systems (IPS).
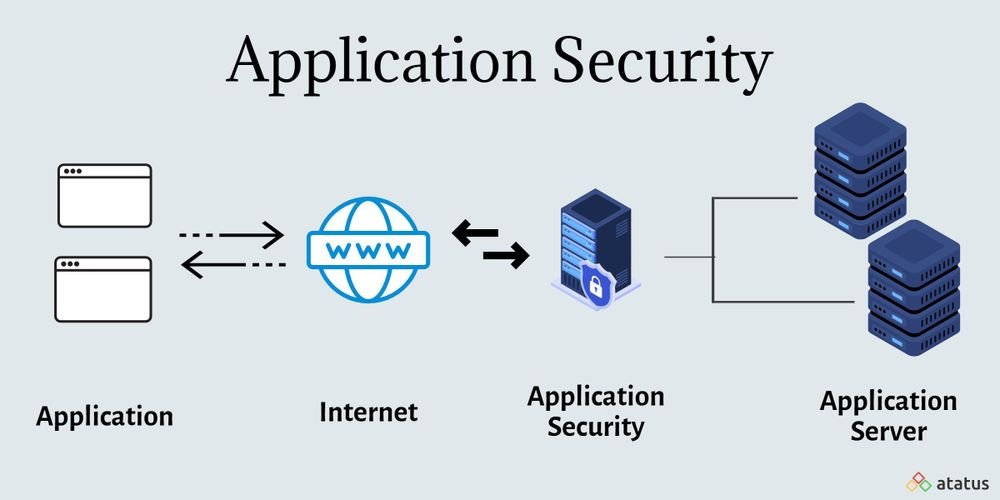
Why is application security important?
If your organization handles customer data (and virtually all businesses do), application security is essential. It’s vital that you implement security solutions that monitor and manage app vulnerabilities because data is a prized asset for attackers. Whether it’s your customers’ data, proprietary product secrets, or confidential employee information, attackers can use it for nefarious purposes.
Application security demonstrates a proactive approach to security, rather than a reactive one. Protecting your apps from the start is significantly smarter than simply hoping an attack doesn’t happen—and then when it does, hurrying to try and fix the problem. A proactive approach to application security can give you an edge when it comes to mitigation. You might be able to fix a problem before it even has a chance to affect your operations or customers.
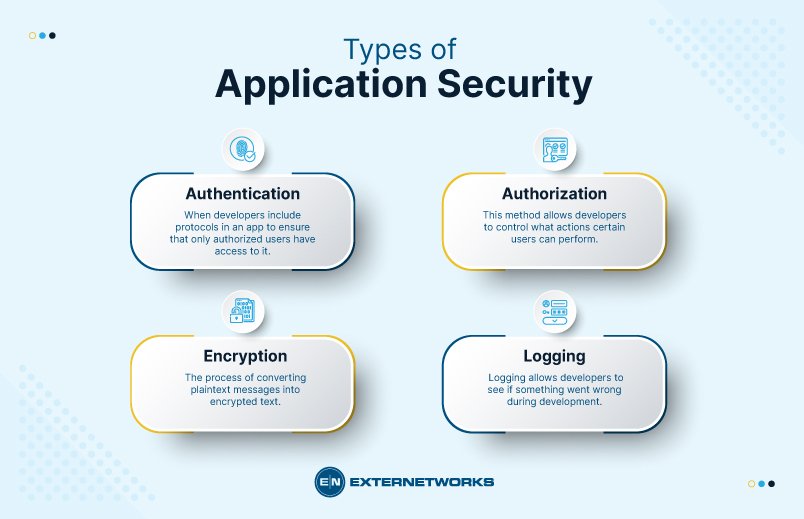
Types of Application Security
Authentication, authorization, encryption, logging, and application security testing are all examples of application security features. Developers can also use code to reduce security flaws in applications.
Authentication
When developers include protocols in an application to ensure that only authorized users have access to it. Authentication procedures verify that the user is who they claim to be. When logging into an application, this can be performed by requiring the user to supply a user name and password. Multi-factor authentication necessitates the use of multiple forms of authentication, such as something you know (a password), something you have (a mobile device), and something you are (a biometric).
Authorization
A user may be authorized to access and use the application after being authenticated. By comparing the user’s identification to a list of authorized users, the system may verify that the user has permission to access the application. In order for the application to match only validated user credentials to the approved user list, authentication must take place before authorization.
Encryption
Other security measures can safeguard sensitive data from being seen or utilized by a cybercriminal after a user has been verified and is using the application. Traffic containing sensitive data that flows between the end-user and the cloud in cloud-based applications can be encrypted to keep the data safe.
Logging
If a security breach occurs in an application, logging can assist in determining who gained access to the data and how they did so.
Benefits of application security
Application security is crucial for businesses of all sizes to protect their digital assets and maintain customer trust. Here are some of the key benefits:
Protection of Sensitive Data
- Data breaches prevented: Secure applications safeguard confidential information like customer data, financial records, and intellectual property from unauthorized access.
- Compliance adherence: Many industries have strict data privacy regulations. Strong application security helps meet these requirements.
Reduced Financial Losses
- Cost of breaches minimized: Data breaches can be extremely costly due to legal fees, lost revenue, and damage to reputation. Application security helps mitigate these expenses.
- Insurance premiums reduced: Some insurers offer discounts for organizations with robust security measures.
Enhanced Reputation and Customer Trust
- Improved brand image: A secure application demonstrates a commitment to customer data protection, boosting brand reputation.
- Increased customer confidence: Customers are more likely to trust businesses with strong security practices, leading to increased loyalty and referrals.
Business Continuity
- Reduced downtime: Secure applications are less likely to experience disruptions caused by cyberattacks, ensuring business continuity.
- Operational efficiency: Strong security practices can streamline operations and reduce the risk of errors.
Risk Mitigation
- Vulnerability reduction: Regular security assessments and testing identify and address vulnerabilities before they can be exploited.
- Threat prevention: Application security measures can deter attackers and prevent successful breaches.
Competitive Advantage
- Innovation acceleration: A secure environment fosters innovation by allowing businesses to focus on development without worrying about security risks.
- Market differentiation: Demonstrating a strong commitment to security can set a business apart from competitors.
Application Security Tools and Solutions
Web Application Firewall
A WAF monitors and filters HTTP traffic that passes between a web application and the Internet. WAF technology does not cover all threats but can work alongside a suite of security tools to create a holistic defense against various attack vectors.
Runtime Application Self-Protection
RASP technology can analyze user behavior and application traffic at runtime. It aims to help detect and prevent cyber threats by achieving visibility into application source code and analyzing vulnerabilities and weaknesses.
Vulnerability Management
Vulnerability management is a critical aspect of application security. It involves identifying, classifying, prioritizing, and mitigating software vulnerabilities. Vulnerability management tools scan your applications for known vulnerabilities, such as those listed in the Common Vulnerabilities and Exposures (CVE) database.
Software Bill of Materials
A Software Bill of Materials (SBOM) is a comprehensive list of components in a piece of software. It provides transparency into an application’s composition, making it easier to track and manage any vulnerabilities. An SBOM can include details about the open-source and proprietary components, libraries, and modules used in the software.
Software Composition Analysis
SCA tools create an inventory of third-party open source and commercial components used within software products. It helps learn which components and versions are actively used and identify severe security vulnerabilities affecting these components.
Static Application Security Testing
SAST tools assist white box testers in inspecting the inner workings of applications. It involves inspecting static source code and reporting on identified security weaknesses.
Dynamic Application Security Testing
DAST tools assist black box testers in executing code and inspecting it at runtime. It helps detect issues that possibly represent security vulnerabilities. Organizations use DAST to conduct large-scale scans that simulate multiple malicious or unexpected test cases.
Interactive Application Security Testing
IAST tools employ SAST and DAST techniques and tools to detect a wider range of security issues. These tools run dynamically to inspect software during runtime. It occurs from within the application server to inspect the compiled source code.
How does Application Security Work?
Application security works by identifying potential threats and preventing them from reaching end users. For example, if a hacker were to try to log into a bank account using stolen credentials, the application would detect this attempt and prevent the user from being able to complete the transaction.
To protect against these kinds of attacks, applications need to identify and block any attempts at the unauthorized activity. To accomplish this, they typically rely on two main methods:
- Identify the source of the attack (source identification)
- Block the attack (prevention)
Prevention
To prevent an attack, applications perform checks and determine whether a particular action is allowed. The most common form of prevention involves checking the validity of client input parameters. If a parameter is invalid, the application returns an error message instead of performing the requested operation.
Prevention occurs when the application automatically performs actions based on its knowledge of handling situations. You added a product to your shopping cart but haven’t paid for it. Your browser requests the server to confirm that you will not pay for it.
Preventing these attacks requires developers to anticipate every possible scenario and write code to deal with them. There’s no way to know which scenarios will occur. Many applications use heuristics to predict the likelihood of various attacks.
Application Security with Imperva
Web Application Firewall – Prevent attacks with world-class analysis of web traffic to your applications.
Runtime Application Self-Protection – Real-time attack detection and prevention from your application runtime environment goes wherever your applications go. Stop external attacks and injections and reduce your vulnerability backlog.
API Security – Automated API protection ensures your API endpoints are protected as they are published, shielding your applications from exploitation.
Advanced Bot Protection – Prevent business logic attacks from all access points – websites, mobile apps and APIs. Gain seamless visibility and control over bot traffic to stop online fraud through account takeover or competitive price scraping.
Attack Analytics – Ensures complete visibility with machine learning and domain expertise across the application security stack to reveal patterns in the noise and detect application attacks, enabling you to isolate and prevent attack campaigns.
Client-Side Protection – Gain visibility and control over third-party JavaScript code to reduce the risk of supply chain fraud, prevent data breaches, and client-side attacks.
How to enable application security
A security-by-design approach means your applications start off with a clean, well-protected slate. But beyond this method, there are several other application security best practices businesses should keep in mind as they finetune their strategy.
- Treat your cloud architecture, whether public or on-prem, as insecure. Defaulting to this mindset eliminates complacency and comfort in assuming the cloud is secure enough.
- Apply security measures to each component of your application and during each phase of the development process. Be sure you include the appropriate measures to each unique component.
- A crucial but time-consuming strategy is to automate the installation and configuration processes. Even if you have already completed these processes previously, you’ll need to re-do them for your next-generation applications.
- Simply establishing security measures is not enough. Be sure to frequently test and retest them to ensure they are working properly. In the event of a breach, you’ll be thankful you detected and remediated any faults.
- Take advantage of SaaS offerings to offload time-consuming security tasks and refocus your scope to more high-value projects. SaaS is both relatively affordable and doesn’t require a dedicated IT team to configure products.
Application Security Approaches
Different approaches will uncover different subsets of the application’s security flaws, and they’ll be most effective at different stages of the development lifecycle. They all reflect the various time, effort, cost, and vulnerability trade-offs.
- Design Review
The architecture and design of the application can be examined for security flaws before code is created. The construction of a threat model is a popular strategy used at this phase. - White-box Security Review or Code Review
A security engineer delves into the application by manually inspecting the source code and looking for security issues. Vulnerabilities unique to the application can be discovered through understanding the application. - Black-box Security Audit
This is accomplished solely through the use of an application to test it for security flaws; no source code is necessary. - Automated Tooling
Many security tools can be automated by including them in the development or testing process. Automated DAST/SAST tools that are incorporated into code editors or CI/CD systems are examples. - Coordinated Vulnerability Platform
Many websites and software providers offer hacker-powered application security solutions through which individuals can be recognized and compensated for reporting defects.
What are Application Security Risks?
- Vulnerabilities
- Malicious activities
- Privacy violations
Vulnerabilities
A vulnerability is a weakness or flaw in the design of an application that allows attackers to compromise the system. A vulnerability could take several forms, including buffer overflows, SQL injection, cross-site scripting, etc. Vulnerability management is one of the most important aspects of securing an application because vulnerabilities can lead to malicious activities such as stealing confidential information, defacing websites, or launching denial-of-service attacks.
Malicious Activities
Malicious activities include violating the website’s terms of service, such as posting inappropriate content or accessing sensitive information without authorization. They also include actions taken by third parties who gain access to the site through the attacker’s exploit gain access to the site through an exploit in the application. For example, if an attacker gains control over a user’s session cookie, she may be able to view other users’ personal information.
Privacy Violations
Privacy violations involve violating the privacy of individuals using the application. Examples include obtaining personally identifiable information (PII) about users without their consent, collecting PII without permission, or sharing PII outside the organization.
Application security is a subset of network security since both terms called privacy violation involve another term involving collecting or using personally identifiable information (PII) without permission.

Application Security and APM
There is a symbiotic relationship between application performance management and application security. Improved visibility into highly distributed or complex environments, such as microservices architecture and cloud applications, is possible with an effective APM strategy.
By providing a full picture of an application’s infrastructure and components, measuring ideal performance with dynamic baselining, and alerting when discrepancies or abnormalities are identified, the APM data can assist improve software security. When combined with application security solutions, APM can provide redundancy and additional support for your safety program by increasing the depth of information about the inner workings of your application and system.
Application Security Best Practices
Perform a Threat Assessment
Having a list of sensitive assets to protect can help you understand the threat your organization is facing and how to mitigate them. Consider what methods a hacker can use to compromise an application, whether existing security measures are in, and if you need additional tools or defensive measures.
Shift Security Left
Companies are transitioning from annual product releases to monthly, weekly, or daily releases. To accommodate this change, security testing must be part of the development cycle, not added as an afterthought. This way, security testing doesn’t get in the way when you release your product.
Prioritize Your Remediation Ops
Vulnerabilities are growing, and developers find it difficult to address remediation for all issues. Given the scale of the task at hand, prioritization is critical for teams that want to keep applications safe.
Measure Application Security Results
It is important to measure and report the success of your application security program. Identify the metrics that are most important to your key decision makers and present them in an easy-to-understand and actionable way to get buy-in for your program.
Manage Privileges
It is important to limit privileges, especially for mission critical and sensitive systems. Application security best practices limit access to applications and data to those who need them, when they need them—this is known as the least privilege principle. Least privilege is critical for two reasons:
- Hackers might compromise less privileged accounts, and it is important to ensure that they cannot gain access to sensitive systems.
- Insider threats are just as dangerous as external attackers. If insiders go bad, it is important to ensure that they never have more privileges than they should—limiting the damage they can do.
What is Application Security Testing?
Application Security Testing (AST) ensures software security, and encompasses the strategies, practices, and technologies dedicated to identifying software vulnerabilities throughout the software development lifecycle (SDLC). It involves making certain that applications, whether they are web-based, mobile, desktop, or embedded software applications are built, maintained, and operated in a way that prevents unauthorized access or alterations.
Types of Application Security Testing
Black Box Security Testing
In a black box test, the testing system does not have access to the internals of the tested system. This is the perspective of an outside attacker. A testing tool or human tester must perform reconnaissance to identify systems being tested and discover vulnerabilities. Black box testing is highly valuable but is insufficient, because it cannot test underlying security weaknesses of applications.
White Box Security Testing
In a white box test, the testing system has full access to the internals of the tested application. A classic example is static code analysis, in which a testing tool has direct access to the source code of the application. White box testing can identify business logic vulnerabilities, code quality issues, security misconfigurations, and insecure coding practices. White-box testing can also include dynamic testing, which leverages fuzzing techniques to exercise different paths in the application and discover unexpected vulnerabilities.
Gray Box Security Testing
In a gray-box test, the testing system has access to limited information about the internals of the tested application. For example, the tester might be provided login credentials so they can test the application from the perspective of a signed-in user. Gray box testing can help understand what level of access privileged users have, and the level of damage they could do if an account was compromised.
Conclusion
Application security is an indispensable facet of modern cybersecurity. As applications become increasingly complex and interconnected, the potential attack surface expands, necessitating a robust and proactive approach to safeguarding them.
Key takeaways from the world of application security:
- It’s a continuous process: Security is not a one-time event but an ongoing journey that requires constant vigilance and adaptation.
- Collaboration is crucial: Effective application security demands close cooperation between development, security, and operations teams.
- Defense-in-depth strategy: Implementing multiple layers of security controls is essential to mitigate risks effectively.
- Security by design: Integrating security into the development lifecycle from the outset is paramount.
- People, process, and technology: A holistic approach encompassing these three elements is vital for success.
- Staying updated: Keeping pace with evolving threats and vulnerabilities is crucial.
In conclusion, application security is a complex but essential challenge that organizations must address to protect their digital assets, maintain customer trust, and comply with regulations. By adopting a comprehensive and proactive approach, organizations can significantly reduce their exposure to cyber risks and build a resilient security posture.
FAQs
Application security aims to protect software application code and data against cyber threats. You can and should apply application security during all phases of development, including design, development, and deployment.
Application security engineers are responsible for establishing and enforcing security standards and best practices within an organization. They conduct regular security assessments, identify vulnerabilities, and work with development teams to remediate them.