Cyber threat intelligence is a flexible, dynamic technology that uses data collection and analysis gleaned from threat history to block and remediate cyber attacks on the target network. The threat intelligence itself is not a hardware-based solution. Rather, this strategic intelligence involves tactics techniques and procedures and forms a crucial component of an organization’s overall security architecture. Because threats evolve and multiply over time, a cybersecurity system depends on threat intelligence and analysis to ensure it catches as many attacks as possible.

Why is Threat Intelligence Important?
Today, the threat landscape is more dynamic and sophisticated than ever before. Anticipating a threat actor’s next move is incredibly challenging, especially without data to back up any assumptions. Threat intelligence guides an organization’s assessment of threat actors’ past behaviors, what they’ll do next, and where protection is needed.
Threat intelligence has become an increasingly common capability among security tools and is a key component of security architecture that helps security teams detect and investigate threats.
Using threat intelligence, organizations are typically better prepared to:
- Reveal adversarial motives and their tactics, techniques, and procedures (TTPs) to empower cybersecurity stakeholders.
- Understand a threat actor’s decision-making process and help security teams implement incident response.
- Make decisions about cybersecurity investments by illuminating previously unknown information.
- Inform business stakeholders (e.g., executive boards, CISOs, CIOs, and CTOs) about threat actors’ behavior for wiser investments, improved risk mitigation, and more efficient and faster decision-making.
Types of Cyber Threat Intelligence
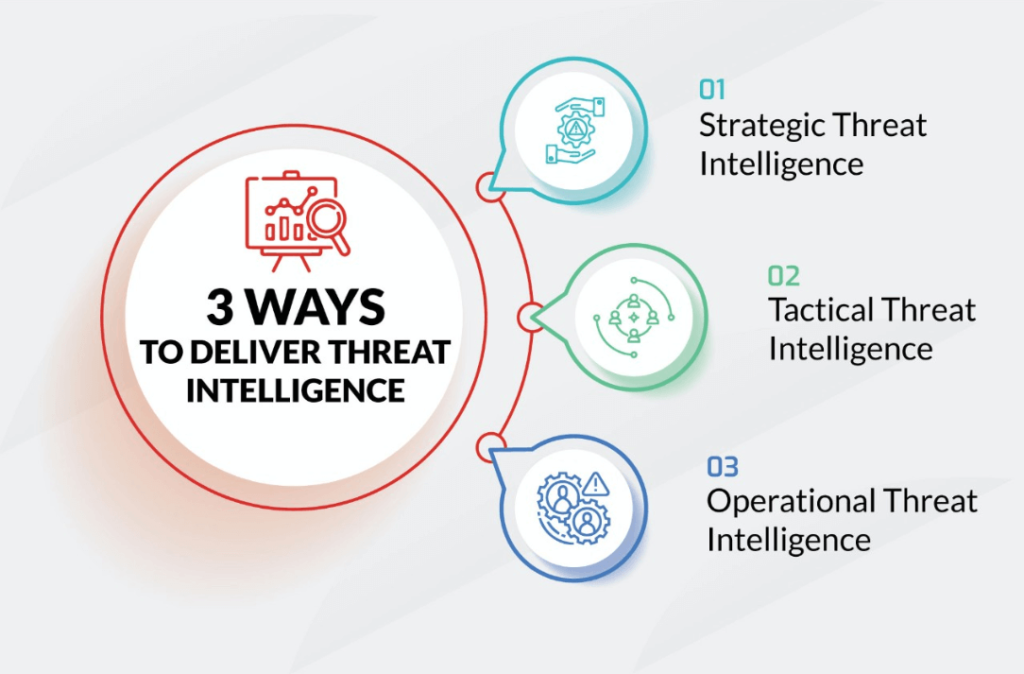
This intelligence can be understood on three different levels – strategic, operational, and tactical:
Tactical intelligence is designed to combat specific threats when and where they happen. It is collected in real-time, as security incidents occur, and informs how your security tools – SIEM, firewall, EDR, etc. – will enact remediation.
Operational intelligence is one step more removed. It takes an overview of potential threats to gauge risk and to oversee remediation methods. This includes information on where an attack may come from, and how likely the attack is to happen. This intelligence might affect remediation policies, and the configuration of specific tools to block potential threats before they become active.
Strategic intelligence is a high-level overview of your organization’s threat landscape in terms of geographic, political, and business trends. This type of intelligence will present broad trends and identify if new security tools are needed, and is usually presented to key decision makers in an organization, such as C-level executives.
Benefits of Using Cyber Threat Intelligence
Cyber threat intelligence can introduce a number of additional benefits for organizations beyond the scope of mitigation, including:
- Risk reduction: Increased visibility across the threat landscape into current threats and emerging cyberattacks may help organizations identify and assess risks with a proactive approach to preparation.
- Improved security posture: Understanding the TTPs used in past attacks can help organizations implement the appropriate security controls to prevent or mitigate future cyberattacks.
- Cost reduction: Cyber threat intelligence is often cost-effective and may lower the overall financial burden of security incidents including data breaches, which can be expensive.
- Regulatory compliance: Organizations that must adhere to various regulations such as GDPR, SOX, HIPAA, etc. can use cyber threat intelligence to help establish and maintain compliance.
What to Look for in a Threat Intelligence Solution
Although threatintelligence is a necessary element of any cybersecurity approach to limit risk, make sure the system you implement is adequate for your requirements. Regardless of the size or nature of your organization, there are a few components of a threat intelligence solution you will need to have in place to contain risk.
Simplified access to diverse data
The more raw datafrom a variety of sources, the better, as each data collection point in a threat history dataset, if they come from the right sources, can be used to defend against a bad actor. Therefore, the more you have, the stronger your defenses will be. You will also need threat intelligence and analysis that incorporates machine learning capabilities because this directly impacts the size and quantity of your datasets.
Machine-learning capabilities
Machine learning has the ability to recognize patterns and use these in a threat intelligence solution to predict threats before they hit your network. Those in charge of IT security can leverage machine learning-generated datasets to detect and then evaluate a wide array of dangers, including advanced persistent threats (APTs), malware, ransomware, and zero-day threats, adding practicality to their threat intelligence.
Automated action
A cyberthreat intelligence program must incorporate automated responses to threats. Automation can serve several purposes. Automating threat intelligence data collection and detection relieves IT security teams of responsibilities involving targeting and logging every threat that engages the attack surface. Moreover, when cyber strategic intelligence incorporates automated action steps once a threat has been identified, the network and its connected devices are better protected.
While some threat behavior analysis is best done using human problem-solving and creative thinking, threats can be automatically contained and eliminated by the intelligence system. With the intelligence system, you can also automate measures to shield the rest of the network from the threat, such as malware analysis within a sandboxed environment.
Cross-industry support
While nothing can—or should—eliminate the competitive element within each industry vertical, in many ways, cyber threat intelligence security is a team effort on the part of the multiple analysts. A comprehensive cyber threat intelligence and analysis solution incorporates insights from various professionals and organizations within your industry, as well as within the cyber threat intelligence community.
Cyber Threat Intelligence Tools
Cyber threat intelligence tools help protect current vulnerabilities as well as future ones by collecting and analyzing threat information from several external sources.
- Data-driven: When a malicious attack is initiated, a “fingerprint” or cyber threat indicator is left behind. A cyber threat intelligence tool should gather data from cyber threat indicators to protect in both a predictive and proactive manner.
- Flexible: Most organizations want cyber intelligence tools to be compatible with any IT infrastructure and environment they may have.
- External-focused: Cyber intelligence tools may be integrated with internal systems to assist in threat detection, but they should prioritize scanning external sources like data feeds and repositories for any emerging threats.
- Comprehensive: Cyber intelligence tools must provide complete protection. This means that it should be able to scan large numbers of external feeds from all across the world, including the dark web.
- Extensible: Cyber threat intelligence tools should also be extensible and seamless enough to connect to any cybersecurity landscape. It should be able to co-exist with varying environments, compliance tools, and hardware variants.
What Organizations are Getting Wrong about Cyber Threat Intelligence
Understanding the value to their business
Even though threat intelligence focuses on important business problems, it is easy for decision-makers to underestimate its value. This is often due not to a lack of comprehension on the part of stakeholders but insufficient explanation and presentation on the part of the cybersecurity team. A cyber threat analysis presentation can easily devolve into a showy and confusing display of graphics and statistics, losing its teeth along the way.
To prevent this kind of misunderstanding, it is crucial for the threat analysis team to outline the specific business problems that arise due to the threats described during the dissemination phase. Also, action steps should be detailed, including how they may benefit the business’s bottom line.
The wrong feed
Because there are so many feeds to choose from in a threat analysis system, it can be easy to pick one that is not relevant to your business. It is important to identify the best feed for your operation. This is often similar to the feed other businesses in your sector and of similar size use, but your infrastructure or products and services may sometimes require a different feed than very similar businesses.
Also, keep in mind that if your attack surface includes the personal data of specific executives or others in your company, a different feed may be necessary than if you were only trying to protect your digital assets, for instance. There are many factors that will determine how you choose your feed, but with careful planning, you can make the right choice.
Key components for actionable threat intelligence
Threat history data
Data, data, and more data. Actionable threat intelligence needs an excess of threat history data. Cyber threat analysis and machine learning capabilities produce valuable insights. Both improve with larger data sets. If the cyber threat intelligence only has a threat data set of 10, it can only possibly proactively block 10 threats. As the data set increases, the threat intelligence will gain greater knowledge of malicious threats potentially threatening your network. In addition, ML-based analysis algorithms continue to improve as the data increases.
Automated detection/blocking
Having precise cyber threat analysis, machine learning capabilities, and extensive threat history data is great, but the cyber threat intelligence system needs to be able to leverage these tools to automate action. It needs to not just react to detected threats but take proactive action to permanently block threats.
The volume of cyber threats is increasing exponentially and likely will continue to do so for the foreseeable future. Manual actions simply will not keep pace. As a result, it is imperative that businesses deploy a unified threat management solution capable of identifying a threat in Asia and instantaneously blocking that threat in South America.
Cyber threat analysis
Cyber threat intelligence must have well-designed cyber threat analysis. Businesses are handling more data than ever, so the financial incentive for hackers is greater than ever and hackers are becoming more sophisticated and more coordinated. This presents new challenges that require more innovative cyber threat analysis techniques.
Machine learning capabilities
Two of the most concerning trends in threat defense are an increase in the volume of threats and the quick evolution of common threats. In order to keep up with these trends, cyber threat intelligence needs to leverage machine learning in threat situations.
Machine learning can recognize patterns and predict threats in massive data sets, all at machine speed. The security operations teams can leverage this to rapidly detect and prioritize advanced threats that require in-depth human analysis. To develop effective machine learning capabilities, organizations should consider the following requirements:
- Dataset diversification and precision. Balanced representation of malware encountered by organizations of various industries, sizes, and geolocations, and delivered through different attack vectors is essential for comprehensive coverage.
- Multilayered processing. Each processing stage of a machine learning pipeline should improve fidelity and accuracy of detections to ensure that security teams deal with prioritized and context-rich detections.
- Correlation of endpoint and network data. By correlating results of multilayered processing, the system should reinforce detections, improve precision and self-learning capabilities, and detect more threats faster.
- In-depth domain expertise and continuously trained classifiers. Domain knowledge and continuous learning is a crucial part of the puzzle when building a robust machine learning system that isn’t easy to manipulate.
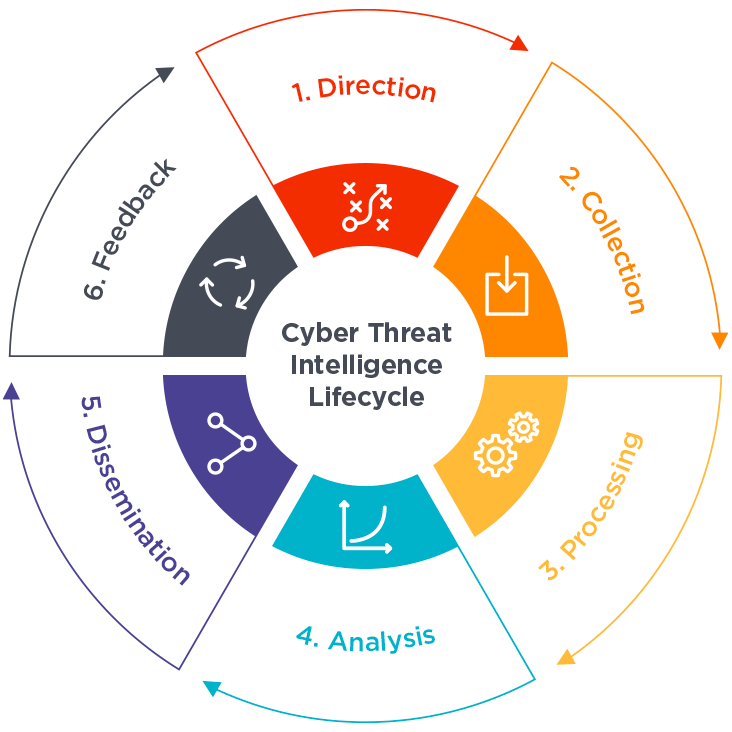
The Threat Intelligence Life Cycle
For most organizations, the threat intelligence life cycle consists of six stages: direction, collection, processing, analysis, dissemination, and feedback. However, the specific activities performed during each phase of the threat intelligence life cycle are often slightly different depending on the organization and are usually determined by a combination of unique factors including use cases, priorities, and risk.
Ideally, key stakeholders will clearly define the organization’s goals and objectives for threat intelligence before any other phases begin to ensure the success of the entire life cycle. Once threat intelligence goals are set, they may be subject to change depending on the data collected and the feedback received. Data is gathered from a wide variety of sources, including internal, technical, and human components, and then used to develop a more complete picture of potential and actual threats.
Data vs intelligence
An effective cybersecurity intelligence system makes a clear distinction between threat data collection and threat intelligence to stop threat actors. Cyber threat intelligence includesdata collection and processing to detect, stop, and mitigate threats. Data collection, on its own, provides useless information until it is analyzed in the context of intelligence. The analysis reveals operational intelligence such as the types of threats that may be imminent, weaknesses in the network, and the different sourcesof threats. This is collated and implemented into a cyber threat intelligence and analysis system.
In other words, data collection is one of the building blocks of cyber threat intelligence. Cyber intelligence security professionals, given the right tools, can use threat data feeds and technical information regarding the network and business to formulate a more complete protection plan for the organization.
Types of Cyber Threat Attacks
A cyberattack occurs when there is any type of unauthorized access to a system or network by a third party, carried out by a threat actor.
By SentinelOneJune 24, 2021
Cyber Threat Intelligence (CTI) involves collecting and analyzing information about potential threats. This guide explores the importance of CTI in proactive cybersecurity measures and incident response.
Learn about the types of threat intelligence, sources, and how to integrate CTI into your security strategy. Understanding CTI is crucial for organizations to stay ahead of emerging threats.

What is Cyber Threat Intelligence?
According to Gartner, threat intelligence is “evidence-based knowledge (e.g., context, mechanisms, indicators, implications, and action-oriented advice) about existing or emerging menaces or hazards to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard.”
In cybersecurity, threat intelligence is the data an organization collects, processes, and analyzes to better understand threat actors’ motives, targets, and attack behaviors. Using this information, organizations can make fast, informed decisions to protect themselves against threat actors in the future.
It’s important to note the difference between threat intelligence and threat information: threat information is the data itself without context, while threat intelligence involves analyzing the information and using it to inform any decisions about what steps to take next.
Why is Threat Intelligence Important?
Today, the threat landscape is more dynamic and sophisticated than ever before. Anticipating a threat actor’s next move is incredibly challenging, especially without data to back up any assumptions. Threat intelligence guides an organization’s assessment of threat actors’ past behaviors, what they’ll do next, and where protection is needed.
Threat intelligence has become an increasingly common capability among security tools and is a key component of security architecture that helps security teams detect and investigate threats.
Using threat intelligence, organizations are typically better prepared to:
- Reveal adversarial motives and their tactics, techniques, and procedures (TTPs) to empower cybersecurity stakeholders.
- Understand a threat actor’s decision-making process and help security teams implement incident response.
- Make decisions about cybersecurity investments by illuminating previously unknown information.
- Inform business stakeholders (e.g., executive boards, CISOs, CIOs, and CTOs) about threat actors’ behavior for wiser investments, improved risk mitigation, and more efficient and faster decision-making.
The Threat Intelligence Life Cycle
For most organizations, the threat intelligence life cycle consists of six stages: direction, collection, processing, analysis, dissemination, and feedback. However, the specific activities performed during each phase of the threat intelligence life cycle are often slightly different depending on the organization and are usually determined by a combination of unique factors including use cases, priorities, and risk.
Ideally, key stakeholders will clearly define the organization’s goals and objectives for threat intelligence before any other phases begin to ensure the success of the entire life cycle. Once threat intelligence goals are set, they may be subject to change depending on the data collected and the feedback received. Data is gathered from a wide variety of sources, including internal, technical, and human components, and then used to develop a more complete picture of potential and actual threats.
Most of the time, threat information is compiled into a threat intelligence feed: a continuous data stream that provides information about threats including lists of IoCs such as malicious URLs or emails, malware hashes, and suspicious IP addresses. The data populating threat intelligence feeds is often drawn from several sources, including open-source intelligence feeds, network and application logs, and third-party feeds.
Once enough data is collected, it is turned into actionable intelligence that is both timely and clear to everyone, including key stakeholders who will use the information to improve future threat intelligence life cycles and refine their decision-making processes.
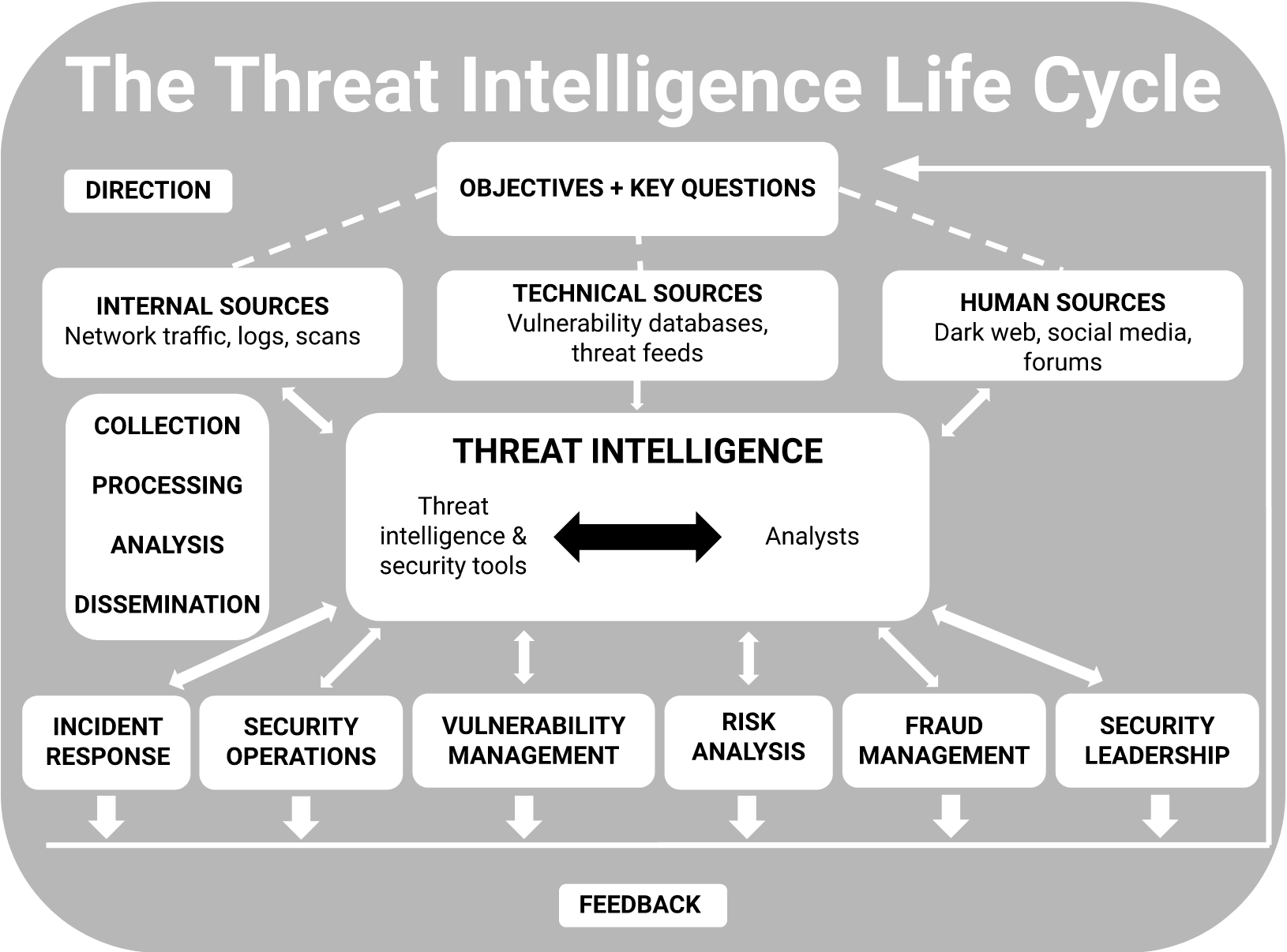
1. Direction
This phase of the threat intelligence life cycle is where stakeholders set goals for the overall threat intelligence program. Direction typically involves understanding and articulating:
- The assets that need protecting
- The potential impact of losing assets or interrupting processes
- The types of threat intelligence required to protect assets and respond to threats
- The priorities about what to protect
2. Collection
This phase of the threat intelligence life cycle involves gathering information that addresses the most important intelligence requirements. Data collected is usually a combination of finished information (e.g., intelligence reports from experts and vendors) and raw data (e.g., malware signatures or leaked credentials).
Collection typically occurs through a variety of sources, including:
- Metadata and logs from internal networks and security devices
- Threat data feeds from industry organizations and cybersecurity vendors
- Conversations and interview with knowledgeable sources
- Open source news and blogs
- Websites and forms
- Closed sources such as dark web forums
3. Processing
This phase of the threat intelligence life cycle involves transforming collected data into a usable format, with different means of processing for different collection methods. For instance, raw data must be processed by humans or machines in order to be considered usable, and all human reports should be correlated and ranked, deconflicted, and checked.
4. Analysis
This phase of the threat intelligence life cycle involves turning processed information into intelligence that can inform decisions. For example, those decisions could involve whether to investigate a potential threat, what actions an organization should immediately take to block an attack, how to strengthen security controls, or how much of an investment in additional security resources is justifiable.
The presentation of this analysis is also important. Organizations may collect and process endless amounts of information and then present it in a way that can’t be understood or used by decision-makers.
To communicate analysis with a non-technical audience, consider the following recommendations:
- Be concise
- Avoid overly technical terms and confusing jargon
- Articulate issues in business terms
- Include a recommended course of action
The format used to present such information will depend on the intelligence itself and the intended audience. Intelligence teams often provide analysis via a variety of formats, including live videos, slide decks, and formal reports.
5. Dissemination
This phase of the threat intelligence life cycle involves distributing the finished intelligence output to the right departments and teams.
For each intended audience, ask the following questions:
- What threat intelligence does the team need, and how can external information support their activities?
- How can intelligence be presented to make it easy to understand and actionable?
- How often should intelligence teams provide updates and other information?
- What media should be used to disseminate intelligence?
- How should teams follow up if they have any questions?
6. Feedback
Regular feedback from a variety of stakeholders and teams enables cyber threat intelligence analysts to adjust the threat intelligence life cycle so it meets the requirements of each team, especially as business goals and priorities change.
This phase clarifies the overall priorities and the requirements of the security teams that consume the intelligence. Ultimately, their unique needs will guide all future phases of the intelligence life cycle, including:
- What types of data to collect
- How to turn that data into useful information
- How to present that information as actionable intelligence
- Who should receive which types of intelligence, how quickly it should be disseminated, and how quickly to respond to follow-up questions
Types of Cyber Threat Attacks
A cyberattack occurs when there is any type of unauthorized access to a system or network by a third party, carried out by a threat actor. Although various terms are often used interchangeably to describe different types of cyberattacks, there are some important differences worth noting.
Threat
A threat is a person or event with the potential for negatively impacting valuable assets. Although a variety of cyber threats may exist at any given time, threats themselves symbolize the possibility of an attack occurring, rather than the actual attack itself.
Threats may pose an imminent danger, but do not cause harm until they are acted upon by a threat actor. The term “threat” is often used in reference to a wide variety of malicious activities that seek to damage, steal, or prevent access to data. Once a threat becomes a reality, it is then known as a cyberattack.
Vulnerability
A vulnerability is an inherent defect in a network, software, or system’s design that can be exploited by threat actors to damage, steal, or prevent access to assets. The most common types of vulnerabilities include system misconfigurations, out-of-date or unpatched software, missing or weak authorization credentials, missing or poor data encryption, and zero-day vulnerabilities (which are defined below).
Exploit
An exploit is a method threat actors use to take advantage of a vulnerability. It might include software, data, or commands that manipulate the vulnerability so the threat actor is free to perform unwanted or unauthorized actions.
Web Application Attack
A web application attack occurs when vulnerabilities in web applications allow threat actors to gain unauthorized access to sensitive data residing on a database server. The most common types of web application attacks are:
- SQL injections occur when a threat actor adds malicious code into an input form which is submitted into the database and changes, deletes, or reveals data.
- Cross-Site Scripting (XXS) attacks involve a threat actor uploading malicious script code onto a website that can be used to steal data or perform other unwanted actions
Advanced Persistent Threat
An advanced persistent threat (APT) is a broad term describing an attack campaign in which a threat actor establishes a long-term presence on a network to conduct reconnaissance or collect highly sensitive data. APT attacks typically require more resources than a standard web application attack, and the targets are often carefully chosen and well-researched.
Phishing: This is a type of social engineering attack wherein a threat actor impersonates a trusted contact and sends the target spam emails. When the target opens the email and clicks on the malicious link or opens the malicious attachment, the threat actor can gain access to confidential information and even account credentials. Some phishing attacks are also designed to trick users into installing malware.
Malware: One of the most common types of cyberattacks today, a malware attack is when a threat actor uses malicious software to infiltrate a system or network. Malware attacks can include viruses, worms, spyware, ransomware, adware, and trojans. Typically, malware breaches a system or network through a vulnerability and is often executed via phishing emails. When the user clicks a link, installs software, or uses an infected pen drive, the malware is downloaded on the device and can spread.
Conclusion
Cyber Threat Intelligence (CTI) is an indispensable asset in the ever-evolving landscape of cybersecurity. It serves as the eyes and ears of an organization, providing critical insights into potential threats, attacker tactics, and vulnerabilities. By transforming raw data into actionable intelligence, CTI empowers organizations to proactively defend against cyberattacks, minimize damage, and build resilience.
Key takeaways:
- Proactive Defense: CTI enables organizations to anticipate threats, rather than simply reacting to incidents.
- Informed Decision Making: By understanding the threat landscape, organizations can make informed decisions about resource allocation and risk management.
- Faster Incident Response: CTI accelerates incident response by providing context and enabling swift containment.
- Competitive Advantage: Organizations with robust CTI programs can gain a competitive edge by safeguarding their reputation and intellectual property.
However, CTI is not without its challenges. The volume and complexity of cyber threats necessitate continuous adaptation and investment. Effective CTI requires skilled analysts, robust data management, and collaboration across the organization.
In conclusion, cyber threat intelligence is no longer a luxury but a necessity for organizations of all sizes. By embracing CTI and fostering a culture of intelligence-driven security, businesses can significantly enhance their ability to withstand the relentless onslaught of cyberattacks.
FAQs
Cyber threat intelligence involves using data to gather information about threats that an organization may be exposed to. Every organization needs a certain amount of cyber intelligence to stay ahead of attackers.
Cyber threat intelligence (CTI) is essential for modern cybersecurity, offering crucial insights to anticipate, identify, and mitigate advanced threats. The recent cyber-attacks on French diplomatic entities by Nobelium, a notorious Russian cyber-espionage group, underscore the importance of robust CTI.