Cybersecurity management refers to an organization’s strategic efforts to safeguard information resources. It focuses on the ways businesses leverage their security assets, including software and IT security solutions, to safeguard business systems.
These resources are increasingly vulnerable to internal and external security threats such as industrial espionage, theft, fraud, and sabotage. Cybersecurity management must employ a variety of administrative, legal, technological, procedural, and employee practices to reduce organizations’ risk exposure.

Importance of risk management in cybersecurity
Protection from attacks: It helps identify potential threats and vulnerabilities, allowing organizations to implement appropriate safeguards and reduce the likelihood of successful attacks.
Protection from attacks: It helps identify potential threats and vulnerabilities, allowing organizations to implement appropriate safeguards and reduce the likelihood of successful attacks.
Minimizing damage: In the event of a breach, a well-defined risk management plan helps organizations contain the damage, recover lost data, and resume normal operations quickly.
Cost reduction: By proactively addressing risks, organizations can avoid the potentially high costs associated with data breaches, legal liabilities, and reputational damage.
Compliance: Many industries have regulations and standards related to cybersecurity. Risk management helps organizations demonstrate compliance and avoid penalties.
Improved decision-making: By understanding the potential risks and their impact, organizations can make informed decisions about resource allocation and security investments.
Competitive advantage: A strong cybersecurity posture, built on effective risk management, can enhance customer trust and provide a competitive edge in the marketplace.
components of cybersecurity risk management
- Risk identification: Identifying potential threats and vulnerabilities within an organization’s systems and infrastructure.
- Risk assessment: Evaluating the likelihood and potential impact of identified risks.
- Risk treatment: Developing and implementing strategies to mitigate, transfer, accept, or avoid risks. management plan to address changing threats and vulnerabilities.
Types of Cybersecurity Management
Cybersecurity management is a broad field encompassing various strategies and techniques to protect digital assets.
Core Cybersecurity Management Areas
- Information Security Management (ISM): Focuses on protecting the confidentiality, integrity, and availability of an organization’s information assets.
- Network Security Management: Safeguards the network infrastructure from unauthorized access, misuse, and disruption.
- Application Security: Ensures the security of software applications and data they handle.
- Data Security: Protects data from unauthorized access, disclosure, modification, or destruction.
- Identity and Access Management (IAM): Controls access to systems and data based on user identity and roles.
- Disaster Recovery and Business Continuity Management: Plans for and responds to disruptions, ensuring business continuity.
- Compliance and Risk Management: Identifies, assesses, and manages cybersecurity risks to meet regulatory requirements.
Specialized Cybersecurity Management Areas
- Cloud Security: Protects data and applications stored in the cloud.
- IoT Security: Secures internet-connected devices and their communication.
- Mobile Security: Protects mobile devices and data from threats.
- Critical Infrastructure Security: Safeguards essential systems and services.
- Operational Security: Protects day-to-day operations from cyber threats.
Cybersecurity Management Processes
- Risk Assessment: Identifies and evaluates potential threats and vulnerabilities.
- Vulnerability Management: Discovers, assesses, and prioritizes vulnerabilities.
- Incident Response: Develops and implements plans to respond to security incidents.
- Security Awareness Training: Educates employees about cybersecurity best practices.
Cybersecurity Management Frameworks
- NIST Cybersecurity Framework: Provides a structured approach to managing cybersecurity risk.
- ISO 27001: International standard for information security management systems.
- CIS Controls: A set of prioritized actions to improve cybersecurity.
Advantage of Cybersecurity Management
Risk Mitigation
- Proactive identification of threats: Helps anticipate potential attacks and vulnerabilities.
- Effective risk assessment: Prioritizes threats based on their likelihood and impact.
- Implementation of countermeasures: Reduces the chances of successful attacks.
Cost Reduction
- Preventive measures: Avoids costly incident response and recovery efforts.
- Compliance adherence: Prevents hefty fines and legal penalties.
- Business continuity: Minimizes disruptions and financial losses.
Reputation Protection
- Customer trust: Builds confidence in the organization’s ability to protect sensitive data.
- Investor confidence: Maintains a positive image and attracts investments.
- Brand loyalty: Preserves customer relationships and market share.
Operational Efficiency
- Improved decision-making: Provides data-driven insights for security investments.
- Streamlined processes: Ensures efficient security operations.
- Enhanced productivity: Minimizes security-related disruptions.
Competitive Advantage
- Differentiation: Demonstrates a strong commitment to security.
- Market opportunities: Opens doors to new business partnerships.
- Customer acquisition: Attracts customers who value data privacy.
Disadvantage of Cybersecurity Management
While cybersecurity is essential for protecting digital assets, it’s not without its challenges.
Financial Implications
- High costs: Implementing and maintaining robust cybersecurity measures can be expensive, especially for small and medium-sized businesses. This includes investments in hardware, software, personnel, and ongoing training.
- Potential for financial loss: Despite investments in cybersecurity, breaches can still occur, leading to significant financial losses due to data recovery, legal fees, and reputational damage.
Operational Challenges
- Complexity: Managing a complex cybersecurity infrastructure can be overwhelming, requiring specialized skills and knowledge.
- Resource intensive: Cybersecurity demands significant time, effort, and personnel to effectively monitor and respond to threats.
- Disruption: Implementing security measures can sometimes disrupt business operations, leading to temporary inefficiencies or productivity losses.
Human Factor
- Employee errors: Human error remains a leading cause of security breaches, as employees may inadvertently click on malicious links or fall victim to social engineering attacks.
- Difficulty in hiring and retaining talent: Finding qualified cybersecurity professionals can be challenging and expensive, leading to talent shortages.
Evolving Threat Landscape
- Constant adaptation: Cyber threats are constantly evolving, requiring organizations to stay updated on the latest attack vectors and mitigation strategies.
- Zero-day vulnerabilities: New vulnerabilities are discovered regularly, making it difficult to protect against all potential threats.
Balancing Security and Usability
- User experience impact: Excessive security measures can hinder user experience and productivity. Finding the right balance between security and usability is crucial.
Cybersecurity Risk Management Trends
Risks in the digital supply chain
Attacks on the digital supply chain can yield a significant return on investment, as cyber criminals have come to realize. More dangers are anticipated as new vulnerabilities proliferate throughout the supply chain. This is primarily because third parties, which have varying levels of cybersecurity, have become a primary attack vector for bad actors.
For example, even though your environment is relatively secure, a criminal may use a provider in your supply chain with access to your system as a conduit to infiltrate your network.

Expanding attack surface
Attack surfaces on enterprise systems are growing. Risks related to IoT, open-source software, cloud computing, complicated digital supply chains, social media, and other technologies are leaving many organizations exposed to attackers. To handle a wider range of security exposures, companies must look beyond conventional security monitoring, detection, and response methodologies.
This may involve developing internal and external business systems, as well as automating security gap identification. Chief information security officers (CISOs) can use external attack surface management (EASM) technologies, digital risk protection services (DRPS), and cyber asset attack surface management (CAASM) to implement these kinds of systems.
Wider distribution of cybersecurity responsibilities
Executives now want more adaptive security as enterprise cybersecurity demands and expectations mature. To do this, it is best to spread cybersecurity decision-making, accountability, and responsibility throughout the organization, rather than keeping them centralized.
This is particularly important because of the increasing size and complexity of organizations, which may make it difficult for a single person or small team to handle cybersecurity management on their own.
Best Practices in Cybersecurity Management
Understand your IT assets and environment
Effective cybersecurity management requires in-depth knowledge of the IT environments and resources within your firm, including all data and other digital assets, BYOD devices, systems, networks, third-party services, technologies, endpoints, and other relevant items.
Awareness of all the elements of your IT landscape is critical, especially because each facet of your network can be used to penetrate your system. Also, it is imperative that you assess your assets and monitor your IT environment continuously.
Deploy a risk management strategy
Managing risk without a well-thought-out and effective cybersecurity risk management strategy is counterproductive. Organizations must create sound strategies and plans to keep them up-to-date.
Prior to planning, determine your level of risk tolerance and then create a risk profile. Include roles for all employees and key stakeholders, incident response and escalation strategies, and other relevant information.
Make cybersecurity risk management an element of company culture
Even well-crafted cybersecurity risk management policies and processes are useless if they are not properly implemented throughout the firm. So make sure to convey your ideas, plans, and procedures to all parties involved. Integrate cybersecurity risk management within the values and culture of the company. Each party involved in managing cyber threats needs to be aware of, understand, and embrace their responsibilities.
4. Use continuous, adaptive, and actionable risk assessments
Risk identification and assessment are two of the most crucial components of risk management. Risks associated with cybersecurity are always changing. A change in company procedures or the introduction of new technologies, for example, can change your risks significantly. As a result, the organization’s general risk assessment has to be adjusted. To ensure effective security, your procedures must be continuously assessed for deficiencies—and improved.
Difference B/W Cybersecurity & Cybersecurity Management
Cybersecurity is the practice of protecting computer systems, networks, and data from digital attacks. It focuses on the technical aspects of safeguarding information, including implementing security measures, tools, and technologies.

Cybersecurity Management is the broader process of overseeing and controlling cybersecurity efforts within an organization. It involves strategic planning, risk assessment, policy development, incident response, compliance, and overall governance of cybersecurity activities.
Cybersecurity Management Capabilities and Tools
Cybersecurity management encompasses a broad spectrum of capabilities and tools designed to protect an organization’s digital assets. This involves strategic planning, risk assessment, implementation, and continuous monitoring of security measures.
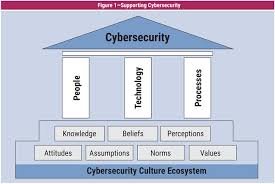
Key capabilities include risk management, incident response, compliance adherence, security awareness training, and business continuity planning. Tools supporting these capabilities range from vulnerability scanners and penetration testing suites to security information and event management (SIEM) platforms and identity and access management (IAM) systems. Effective cybersecurity management requires a holistic approach that combines people, processes, and technology to mitigate cyber risks and ensure business continuity.

What is cybersecurity management and policy, and why does it matter?
Cybersecurity management involves the strategic planning, operations, implementation, and monitoring of cybersecurity practices within an organization.
A cybersecurity manager is responsible for ensuring that their organization’s information systems, networks, and data are protected from cyber threats. While cybersecurity itself is included in this field, cybersecurity management also involves overseeing policies, physical security, risk management, data governance, education and training, contractor and vendor management, and disaster preparedness.
The best cybersecurity managers prioritize the bigger picture in their decision making, which gives businesses an organization-wide, enterprise approach to protecting their information systems, networks, and data.
What does employment look like in the cybersecurity field?
The cybersecurity field is experiencing unprecedented growth, making it an exciting and promising career path.
High Demand, Low Supply
- Talent Shortage: There’s a significant gap between the number of cybersecurity professionals and the number of open positions. This leads to competitive salaries and excellent job security.
- Diverse Roles: The industry offers a wide range of roles to suit different skill sets and interests, from entry-level analysts to top-level executives.
Areas of Employment
- Corporations: Most companies, regardless of size, need cybersecurity experts to protect their digital assets.
- Government Agencies: Government organizations at all levels rely heavily on cybersecurity professionals to safeguard sensitive information.
- Consulting Firms: Cybersecurity consulting firms offer specialized services to organizations in need of expert guidance.
- Military and Intelligence: These sectors often require highly skilled cybersecurity professionals to protect national security.
Types of Cybersecurity Jobs
The cybersecurity field is vast, with roles spanning various specializations:
- Information Security Analyst: Monitors systems for security breaches and implements countermeasures.
- Cybersecurity Engineer: Designs and implements security solutions to protect networks and systems.
- Digital Forensics Analyst: Investigates cybercrimes by collecting and analyzing digital evidence.
- Security Architect: Develops and oversees the security infrastructure of an organization.
- Penetration Tester (Ethical Hacker): Identifies vulnerabilities in systems and networks to improve security.
- Security Manager: Oversees the overall security program of an organization.
- Chief Information Security Officer (CISO): Responsible for the overall security strategy and risk management.
Job Outlook and Salary
- High Salaries: Cybersecurity professionals generally command competitive salaries due to the demand for their skills.
- Growth Potential: The field is constantly evolving, offering ample opportunities for career advancement and skill development.
Challenges and Rewards
- Fast-Paced: The cybersecurity landscape is dynamic, requiring continuous learning and adaptation. threats can be stressful, but it also comes with the satisfaction of protecting critical systems.
- Intellectual Stimulation: Cybersecurity involves solving complex puzzles and staying ahead of cybercriminals.

Conclusion
Cybersecurity management is an indispensable component of modern organizations. It’s a dynamic field that requires constant adaptation to counter evolving threats. While challenges such as financial costs, human error, and the rapid pace of technological change persist, the potential consequences of neglecting cybersecurity are far greater.
A robust cybersecurity posture involves a multifaceted approach. It encompasses technical controls, such as network security, application security, and data protection, as well as human factors like employee training and awareness. Effective risk assessment, incident response planning, and compliance adherence are also critical.
Ultimately, cybersecurity is not merely a technological issue but a strategic one. It requires a commitment from the highest levels of an organization, integrating security into every aspect of operations. By investing in skilled personnel, implementing comprehensive security measures, and fostering a culture of cybersecurity awareness, organizations can significantly enhance their resilience against cyber threats.
The journey towards optimal cybersecurity is ongoing. It demands continuous evaluation, improvement, and adaptation. As technology continues to advance, so too must cybersecurity practices to safeguard digital assets and ensure business continuity.
FAQs
Cybersecurity management refers to an organization’s strategic efforts to safeguard information resources. It focuses on the ways businesses leverage their security assets, including software and IT security solutions, to safeguard business systems.
An effective cybersecurity management policy takes into account the risks that exist for an organization’s resources. Those that administer the program formalize processes and procedures. Once vulnerabilities are found, the management policy will outline solutions to stop malicious code from infiltrating the organization’s perimeter defense systems, servers, and desktops.