Cybersecurity risk management is a strategic approach to prioritizing threats. Organizations implement cybersecurity risk management in order to ensure the most critical threats are handled in a timely manner. This approach helps identify, analyze, evaluate, and address threats based on the potential impact each threat poses.

Why Is Cyber Risk Management Important?
Cyber risk management is crucial to safeguarding an organization’s sensitive information. It involves an ongoing and dynamic set of processes that support regular assessment and adaptation to the changing threat landscape:
- Threat Intelligence Integration: Integrating cyberthreat intelligence into your security operation delivers up-to-date information on emerging threats that helps you enhance your security measures.
- Advanced Analytics: The power of advanced cybersecurity analytics, driven by AI and machine learning, cannot be overstated.
- Third-Party Risk Management: An organization’s cybersecurity posture is only as strong as its weakest link, which is often a vendor or supply chain partner.
Cyber Risk Management Frameworks
There are several cyber risk management frameworks, each of which provides standards organizations can use to identify and mitigate risks. Senior management and security leaders use these frameworks to assess and improve the security posture of the organization.
NIST CSF
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a popular framework. The NIST CSF framework provides a comprehensive set of best practices that standardize risk management.
ISO 27001
The International Organization for Standardization (ISO) has created the ISO/IEC 270001 in partnership with the International Electrotechnical Commission (IEC).
DoD RMF
The Department of Defense (DoD) Risk Management Framework (RMF) defines guidelines that DoD agencies use when assessing and managing cybersecurity risks.

Who Is Responsible for Cyber Risk Management?
Responsibility for cyber risk management falls across various organizational roles and functions. The level of responsibility may vary depending on the organization’s size, structure, and industry.
Chief Information Security Officer: CISOs are often the senior executives responsible for an organization’s overall cybersecurity strategy and management. CISOs usually lead in identifying, assessing, and mitigating cyber risks and developing and implementing cybersecurity policies and practices.
IT Security Team: Security professionals within the IT department are directly involved in implementing and managing security measures, monitoring systems for potential threats, and responding to incidents. This team may include security analysts, engineers, and administrators.
Risk Management Team: In larger organizations, a dedicated risk management team may assess and mitigate various types of risks, including cyber risks. This team may work closely with IT and cybersecurity professionals to integrate cyber risk into the broader risk management framework.
Chief Information Officer : The CIO drives your information technology’s overall management and strategy. While the CISO focuses on cybersecurity specifically, the CIO ensures that the IT infrastructure and systems align with the organization’s overall goals and objectives, including cybersecurity-related ones.
Legal and Compliance Teams: Professionals in legal and compliance roles ensure that the organization adheres to relevant laws, regulations, and industry standards. They play a crucial role in managing legal and regulatory risks associated with cybersecurity.

Different Types of Cyber Security Risks
In general, we have 7 common cyber security risks.
Malware: Malware, or malicious software, is any program or file that is intentionally harmful to a computer, network, or server. Malware is malicious software such as spyware, ransomware, viruses, and worms.
Emotet: The Cyber security and Infrastructure Security Agency or CISA describes Emotet as “an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans.
Denial of Service: A denial of service or DoS is a cyber-attack that floods a computer or network so it can’t respond to requests. A distributed DoS or DDoS does the same thing, but the attack originates from a computer network.
Phishing: Phishing attack uses a fake email or communication to trick the recipient into opening the email or communication message and carrying out the instructions provided in such email or communication, such as providing a credit card number.
Man in the Middle: A man-in-the-middle attack occurs when the hackers insert themselves into a two-party transaction. After interrupting the traffic, they can filter and steal the information or data.
SQL Injection: A Structured Query Language or SQL injection is a cyber-attack resulting from inserting malicious code into the SQL server. When infected through the SQL code, the server releases information.
Password Attacks: A cyber attacker may gain access to a system and information with the right password. Social engineering is a type of password attack strategy that cyber attackers use that relies heavily on human interaction and often involves tricking people into breaking standard security practices.

Advantages of Cybersecurity Risk Management
Cybersecurity risk management is a critical component of any organization’s security strategy. It involves identifying, assessing, and mitigating potential threats to digital assets. Here are some key advantages:
Protection of Assets
- Data Security: Safeguards sensitive information from unauthorized access, theft, or damage.
- Financial Protection: Prevents financial loss due to cyberattacks like ransomware or fraud.
- Intellectual Property Protection: Safeguards valuable proprietary information and trade secrets.
- System Integrity: Ensures the reliability and availability of critical systems and infrastructure.
Risk Mitigation
- Prioritization: Helps focus resources on the most critical risks.
- Incident Response: Improves preparedness for and response to cyber incidents.
- Business Continuity: Supports the continuity of operations in the event of a cyberattack.
- Compliance: Helps meet regulatory requirements and industry standards.
Cost-Effectiveness
- Risk-Based Approach: Optimizes resource allocation by focusing on high-impact risks.
- Loss Prevention: Reduces the financial impact of cyber incidents.
- Insurance Premiums: May lower insurance costs due to improved risk profile.
Reputation Management
- Customer Trust: Builds and maintains customer trust by demonstrating a commitment to security.
- Investor Confidence: Protects the organization’s reputation and financial standing.
- Brand Protection: Safeguards the brand from damage caused by data breaches or cyberattacks.
Competitive Advantage
- Business Agility: Enables the organization to adapt to changing threats and opportunities.
- Innovation: Fosters a culture of innovation by reducing the fear of cyberattacks.
- Decision Making: Provides valuable insights for informed decision-making.
By implementing effective cybersecurity risk management practices, organizations can significantly reduce their exposure to cyber threats and protect their valuable assets.
Disadvantages of Cybersecurity Risk Management
While cybersecurity risk management is essential, it’s not without its challenges:
Resource Intensive
- Costly: Implementing and maintaining robust cybersecurity measures can be expensive, requiring significant investments in technology, personnel, and training.
- Time-consuming: Risk assessments, policy development, and ongoing monitoring demand substantial time and effort.
Complexity
- Evolving Threat Landscape: Cyber threats constantly evolve, making it difficult to stay ahead of emerging risks.
- Complex Systems: Modern IT environments are highly complex, making risk identification and management challenging.
- Human Error: Despite training, human error remains a significant vulnerability.
Balancing Act
- Security vs. Usability: Strong security measures can sometimes hinder user experience and productivity.
- Risk Tolerance: Determining the appropriate level of risk to accept is a complex decision with potential consequences.
False Sense of Security
- Overreliance: Excessive reliance on security measures can create a false sense of security, leading to complacency.
- Risk Blind Spots: Despite efforts, some risks may be overlooked or underestimated.
Regulatory Burden
- Compliance Costs: Adhering to cybersecurity regulations can be costly and time-consuming.
- Regulatory Overload: The increasing number of cybersecurity regulations can be overwhelming.
It’s important to note that while these challenges exist, they can be mitigated through careful planning, effective implementation, and continuous improvement of cybersecurity risk management programs.
What Is a Cybersecurity Risk Assessment?

A cybersecurity risk assessment evaluates the threats to your organization’s IT systems and data, as well as your capacity to safeguard those assets from cyber-attacks.
Organizations can (and should) use cybersecurity risk assessment to identify and prioritize opportunities for improvement in existing information security programs. Risk assessment also helps companies to communicate risks to stakeholders and to make educated decisions about deploying resources to mitigate those security risks.
Cyber Threat Actors
In order to respond effectively to a cyberattack, it’s imperative to know the threat actors and understand their tactics, techniques, and procedures.
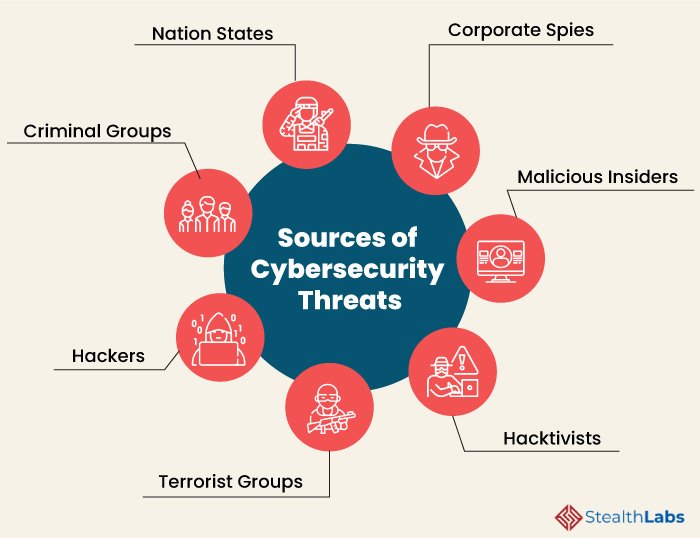
Here are some of the common sources of cyber threats:
1) Nation States
Cyber attacks by a nation can inflict detrimental impact by disrupting communications, military activities, and everyday life.
2) Criminal Groups
Criminal groups aim to infiltrate systems or networks for financial gain. These groups use phishing, spam, spyware, and malware to conduct identity theft, online fraud, and system extortion.
3) Hackers
Hackers explore various cyber techniques to breach defenses and exploit vulnerabilities in a computer system or network. They are motivated by personal gain, revenge, stalking, financial gain, and political activism.
4) Terrorist Groups
Terrorists conduct cyber attacks to destroy, infiltrate, or exploit critical infrastructure to threaten national security, compromise military equipment, disrupt the economy, and cause mass casualties.
5) Hacktivists
Hacktivists carry out cyberattacks in support of political causes rather than for financial gain. They target industries, organizations, or individuals who don’t align with their political ideas and agenda.
6) Malicious Insiders
97% of surveyed IT leaders expressed concerns about insider threats in cyber security. Insiders can include employees, third-party vendors, contractors, or other business associates who have legitimate access to enterprise assets but misuse that accesses to steal or destroy information for financial or personal gain.
7) Corporate Spies
Corporate spies conduct industrial or business espionage to either make a profit or disrupt a competitor’s business by attacking critical infrastructure, stealing trade secrets, and gaining access.
What Are Cyber Threats?
The term cyber threat generally applies to any vector that can be exploited in order to breach security, cause damage to the organization, or exfiltrate data.
Adversarial threats—including third-party vendors, insider threats, trusted insiders, established hacker collectives, privileged insiders, ad hoc groups, suppliers, corporate espionage, and nation-states. This category also includes malicious software (malware) created by any of these entities.
Natural disasters—hurricanes, floods, earthquakes, fire, and lightning can cause as much damage as a malicious cyber attacker. A natural disaster can result in loss of data, disruption of services, and the destruction of an organization’s physical or digital resources.
System failure—when a system fails, it may cause data loss and also lead to a disruption in business continuity.
Human error—any user may accidentally download malware or get tricked by social engineering schemes like phishing campaigns. A storage misconfiguration may expose sensitive data.
Here are key threat vectors that affect the majority of organizations:
- Unauthorized access—may be the result of malicious attackers, malware, and employee error.
- Misuse of information by authorized users—an insider threat may misuse information by altering, deleting, or using data without authorization.
- Data leaks—threat actors or cloud misconfiguration may lead to leaks of personally identifiable information (PII) and other types of sensitive data.
- Loss of data—poorly configured replication and backup processes may lead to data loss or accidental deletion.
- Service disruption—downtime may cause reputational damages and revenue losses. It may be accidental, or the result of a denial of service attack.
Examples of Risk Management in Cybersecurity
Here are some cybersecurity risk management example:

Risk assessment
Risk assessment is one of the most crucial steps in a comprehensive risk management plan for cybersecurity. This process involves identifying, analyzing, and evaluating risks potentially threatening the organization’s assets and networks.
Employee training
Cybersecurity education and awareness training are vital components of a risk management plan. Providing employees with the knowledge they need to identify potential threats can help protect the organization from becoming a victim of cyber-attackers.
Network security audits
Regular audits of an organization’s network can effectively detect vulnerabilities or unauthorized access attempts before they become a significant threat.
Penetration testing
Penetration testing is another valuable tool for assessing an organization’s security posture against potential cyber threats by simulating attacks on systems and networks to discover any existing vulnerabilities or weaknesses that must be addressed before real-world attackers find them first.
Disaster recovery planning
To ensure continuity of operations after a cyber attack occurs, organizations should have robust plans in place for responding quickly and restoring operations as soon as possible following an incident.
Challenges of Cybersecurity Risk Management
Cybersecurity risk management is a complex and ever-evolving field. Organizations face numerous challenges in effectively managing these risks:
1. Evolving Threat Landscape
- New Threats: The constant emergence of new threats, such as ransomware, supply chain attacks, and zero-day vulnerabilities, makes it difficult to stay ahead.
- Sophisticated Attacks: Cybercriminals are becoming increasingly sophisticated, making it harder to detect and prevent attacks.
2. Resource Constraints
- Budget Limitations: Many organizations struggle with limited budgets for cybersecurity initiatives.
- Talent Shortage: There is a global shortage of cybersecurity professionals, making it difficult to find qualified personnel.
3. Complex IT Environments
- Interconnected Systems: The increasing complexity of IT infrastructures, with multiple systems and networks, makes risk assessment and management challenging.
- Cloud Adoption: The migration to cloud-based services introduces new security challenges and risks.
4. Regulatory Compliance
- Burdensome Requirements: Complying with various cybersecurity regulations can be time-consuming and costly.
- Changing Standards: Regulations are constantly evolving, making it difficult to stay updated.
5. Risk Assessment Challenges
- Quantifying Risk: Accurately assessing and quantifying cyber risks is complex and often subjective.
- Prioritization: Determining which risks to prioritize can be difficult, especially with limited resources.
6. Cultural Challenges
- Security Awareness: Building a strong security culture within an organization can be challenging.
- Employee Behavior: Human error remains a significant security risk.
7. Third-Party Risk Management
- Supply Chain Attacks: Managing risks associated with third-party vendors and suppliers is increasingly complex.
- Dependency: Organizations often rely heavily on third parties, making them vulnerable to supply chain attacks.
8. Data Privacy and Protection
- Regulations: Complying with data privacy regulations like GDPR and CCPA is challenging.
- Data Breaches: The consequences of data breaches can be severe, including financial losses and reputational damage.
Addressing these challenges requires a comprehensive and proactive approach to cybersecurity risk management, including the use of advanced technologies, skilled personnel, and effective risk assessment and mitigation strategies.
How to build a cybersecurity risk management plan
You can build a complete cybersecurity risk management plan by implementing these four steps mentioned below:
Pinpoint cybersecurity risks
With so many potential threats, the modern security team faces an uphill battle regarding risk identification. After all, Gartner defines IT risk as “the potential for an unplanned, negative business outcome involving the failure or misuse of IT.”
Essentially, this deciphers if any existing threats target a given vulnerability but also measures the direness of the outcome should an attack be successful.
Evaluate cybersecurity risks
Assessing cybersecurity risks is an essential task for any organization. It’s not just about keeping data safe; it’s also about encouraging communication and collaboration between team members while they take steps to manage the risk.
When you assess the risk within your organization, you can identify the assets and prioritize their importance, plus identify any threats or vulnerabilities that could impact your system.
You can evaluate the risks in your environment using the following steps:
- Identify assets: Identifying your assets such as endpoints, IoT devices, networks, servers, hard drives, and more. This includes both cloud hosted and on-premise assets.
- Prioritize the assets: Create an inventory to keep track of everything and prioritize based on its importance. Assign a value to know the impact of its loss.
- Identify threats: Now that you have identified the assets, identify the threats based on the asset type. For example, physical devices can be stolen while data deployed on clouds can be compromised by cyber attacks.
- Identify vulnerabilities: Identifying the security loopholes and vulnerabilities is the first step to minimizing the negative impact on your organization’s assets and making informed decisions to reduce the attack surface.
Mitigation measures
Once you’ve identified and assessed risks to your organization, the next step is to develop a strategy for mitigating those risks. This calls for an understanding of available options, which often entails a combination of technological solutions like encryption, firewalls, threat-hunting software, and automation—along with best practices designed to meet organizational needs.
Some of the best practices include:
- Businesses take a multipronged approach to risk mitigation, and sound practices can significantly reduce anxiety about security threats.
- Cybersecurity training programs, along with up-to-date software
- Privileged access management solutions, multi-factor authentication, and dynamic data backup are all essential components of an effective strategy
Monitoring
With changes happening around us at the speed of light, monitoring the IT environment is paramount to ensure your organization complies with risk-assessment guidelines and internal controls.

Best Practices for Mitigating Cybersecurity Risks
A cybersecurity threat mitigation strategy reduces the overall risk or impact of a cybersecurity incident by employing security policies and procedures. There are three components to risk mitigation: prevention, detection, and remediation.
1. Risk assessment: Before you start your risk mitigation strategy, your IT security team should conduct a cybersecurity risk assessment, which will identify potential gaps in your organisation’s security controls. Your organisation’s assets can be identified through a risk assessment, along with the security controls currently in place.
2. Establish network access controls: Once you’ve identified high-priority problem areas and assessed your assets, the next step is to establish network access controls to help mitigate the risk of insider threats.
3. Continuously monitor network traffic: Cybersecurity risk can be effectively minimized through the use of proactive action. Every day, there are approximately 2,200 cybercrime attacks, necessitating constant monitoring of network traffic as well as an organization’s cybersecurity posture.
4. Create an incident response plan: An incident response plan is one of the most critical aspects of an organization’s cybersecurity strategy. It must be comprehensive enough to allow all portions of the IT security team and non-tech staff to understand what to do if a data breach occurs or an attack occurs.
5. Minimize your attack surface: A business’s security posture and threat landscape can be identified by surveying all of its entry points, vulnerabilities, or sensitive information.
6. Stay on top of patch updates: Threat actors can quickly exploit vulnerabilities that remain unpatched. Because many software providers release patches continuously, today’s cybercriminals are aware of that.

Conclusion
Cybersecurity risk management is an indispensable component of modern organizational resilience. It is a dynamic process that requires continuous adaptation to the ever-evolving threat landscape. By proactively identifying, assessing, and mitigating potential threats, organizations can significantly reduce their exposure to cyberattacks, protect critical assets, and maintain business continuity.
While challenges such as resource constraints, complex IT environments, and regulatory burdens exist, the benefits of effective cybersecurity risk management far outweigh the obstacles. A robust risk management program is essential for safeguarding sensitive data, preserving organizational reputation, and ensuring compliance with industry standards and regulations.
Ultimately, cybersecurity risk management is not merely a technical function but a strategic imperative. It requires a holistic approach that involves collaboration across departments, investment in technology and personnel, and a strong security culture. By prioritizing cybersecurity risk management, organizations can build a resilient infrastructure capable of withstanding the challenges of the digital age.
FAQs
Protecting your institution from the harmful effects of cyber threats should be a top priority. To do so, you must understand and prepare for malware, ransomware, and DDoS attacks
Companies have cyber security risk management to handle critical threats promptly. Through this method, you can detect, scrutinize, assess, and address threats based on the impact they may cause.
Analyse the severity of each risk by assessing how likely it is to occur and how significant the impact might be if it does. Evaluate how each risk fits within your risk appetite (your predetermined level of acceptable risk). Prioritise the risks.
