Enterprise security consists of the strategies and procedures an organization uses to defend itself from bad actors. Bad actors might be external hackers, or they could be internal employees and contractors. Both small and large businesses should use enterprise-level security best practices and cybersecurity defenses to stop attackers from exploiting their unknown vulnerabilities and stealing their data.

Why Is Enterprise Security Important?
Enterprise security is crucial for safeguarding an organization’s digital assets and reputation. In today’s interconnected world, businesses handle vast amounts of sensitive data, from financial records to customer information. A robust security framework protects this data from cyberattacks, preventing financial loss, reputational damage, and legal consequences. Additionally, it ensures business continuity by minimizing disruptions caused by security breaches. Ultimately, strong enterprise security fosters trust among customers, partners, and employees, allowing businesses to operate with confidence.
Cyber threats don’t always come from outside. Insider threats are also a real issue for organizations. Although employees require trust, cybersecurity strategies are based on not trusting users. Aggregated permissions, unnecessarily high-level permissions and terminated users with active accounts all leave organizations vulnerable to phishing or social engineering attacks. To reduce risks from insider threats, organizations should use enterprise security strategies like least privilege access, updating and revoking permissions when an employee changes jobs, and deactivating accounts of terminated employees.
Enterprise security architecture
Enterprise security architecture must ensure secure physical access while mitigating the threat of social engineering and various malware attacks. Any system that requires a password before granting entry also needs to be protected, particularly because upon entry, a malicious actor could use their access to escalate their privileges or navigate to other areas of the network to compromise them. This may necessitate multi-factor authentication (MFA) measures and limiting which individuals have access rights to specific systems.
Firewalls are an integral part of any enterprise security solution. Because firewalls can inspect traffic coming in and exiting the network, they do not only prevent external attacks but also stop a threat actor from using the organization’s network as a launchpad for attacks on other networks. Also, because a firewall can be configured in a number of ways, it can be placed within the organization’s network to isolate threats that have been able to breach the outer defenses.
Next-generation firewalls (NGFWs) can focus on existing threats and new, zero-day attacks. By using artificial intelligence (AI) to isolate new attacks, an NGFW can protect an organization from a wider range of cyber criminals. It does this using deep packet inspection (DPI) that examines both the basic information about where a data packet came from and what is inside.
In the event an attack breaches the outer edge of a network’s security, an organization should include sandboxing technologies that can contain threats. Within the sandboxed environment, IT admins can study the behavior of a threat and then use that information for future threat intelligence.

Enterprise Security Advantages
Enterprise security is a critical component of any successful business, providing a robust shield against a myriad of threats.
Protection of Sensitive Data
- Data breaches: Prevents unauthorized access to confidential information, safeguarding customer data, financial records, intellectual property, and trade secrets.
- Financial loss: Minimizes the risk of financial losses due to data theft or extortion.
- Reputation damage: Protects the company’s reputation and brand image by preventing data leaks and scandals.
Compliance and Risk Mitigation
- Regulatory adherence: Ensures compliance with industry-specific regulations (e.g., GDPR, HIPAA, PCI DSS), avoiding hefty fines and legal repercussions.
- Risk management: Identifies and mitigates potential security threats, reducing the likelihood of costly incidents.
- Business continuity: Implements disaster recovery plans to ensure minimal disruption in case of a security breach.
Improved Efficiency and Productivity
- Secure infrastructure: Provides a stable and secure IT environment, enabling employees to focus on their core tasks without worrying about security threats.
- Streamlined operations: Automates security processes, reducing manual effort and improving overall efficiency.
- Cost savings: Prevents costly downtime and data recovery efforts.
Enhanced Customer Trust
- Data privacy: Demonstrates a commitment to protecting customer data, building trust and loyalty.
- Competitive advantage: Gain a competitive edge by showcasing a strong security posture.
Specific Security Measures and Their Benefits
- Firewall: Protects the network from unauthorized access.
- Anti-virus software: Prevents malware infections.
- Intrusion detection and prevention systems (IDPS): Detects and blocks malicious activity.
- Encryption: Protects data in transit and at rest.
- Access controls: Restricts access to sensitive information based on user roles and permissions.
- Employee training: Educates employees about security best practices to prevent human error.
Disadvantages of Enterprise Security
While enterprise security is crucial, it’s not without its challenges.
Financial Implications
- High Costs: Implementing and maintaining robust security measures can be expensive, including hardware, software, personnel, and ongoing updates.
- Opportunity Costs: The budget allocated to security might divert resources from other essential business areas.
Operational Challenges
- Complexity: Managing a complex security infrastructure can be time-consuming and requires specialized expertise.
- False Positives: Security systems might sometimes flag legitimate activities as threats, leading to interruptions and reduced productivity.
- User Friction: Excessive security measures can hinder employee productivity and user experience.
Other Considerations
- Evolving Threat Landscape: Cyber threats constantly evolve, making it difficult to stay ahead of attackers.
- Skill Shortages: Finding qualified cybersecurity professionals can be challenging.
- Internal Threats: Employees can pose security risks through accidental or intentional actions.
- Balancing Security and Usability: Striking the right balance between security and user experience is often difficult.
Enterprise security challenges
The challenges facing enterprise security are numerous, dynamic, and evolving. However complex, understanding these challenges helps organizations overcome them. Examples of the many enterprise security challenges that organizations must contend with include the following.
Advanced persistent threats
APTs pose several challenges. For one, they are constantly evolving, which makes it difficult for signature-based security solutions to detect them. They are also executed over a long period, hiding in the background, evading detection until the attack is launched.
Additionally, APTs are developed and executed by well-resourced adversaries who have the time and technical know-how to develop highly sophisticated, complex attacks.
Cyber-physical system vulnerabilities
The convergence of cyber and physical systems has created a number of known and unknown vulnerabilities. Prime examples of this are the Internet of Things and industrial control systems. Both are fraught with security gaps and present enterprise security teams with a rapidly expanding and evolving attack surface.
Data privacy regulations
Because of the number of global privacy laws, almost any organization that touches personally identifiable information (PII) must ensure that appropriate protections are in place to ensure compliance. In addition to securing PII, organizations must also have systems in place to support auditing and reporting requirements.
Mobile malware
Taking advantage of the proliferation of mobile devices, cybercriminals have unleashed mobile malware. Users, accustomed to downloading apps and clicking Quick Response (QR) codes, are susceptible to mobile malware that disguises itself as legitimate downloads.
Ransomware
Ransomware is a top-of-mind challenge for every security professional, because its most common point of entry is every organization’s weakest link—people. Just one click on a malicious link can result in an organization being paralyzed by ransomware.
Security skills shortage
The long-time shortage of skilled cybersecurity professionals continues, making it difficult to hire and retain staff. Even with outsourcing and security services, organizations struggle to address their security needs adequately.
Third-party vulnerabilities
Since most organizations work with third-party vendors and suppliers in some capacity, they become susceptible to external vulnerabilities. Even with third-party risk assessments, organizations find it difficult to identify all third-party vulnerabilities and are often compromised through these less secure vectors.
Best Practices for Enterprise Security
Enterprise security is a multifaceted challenge requiring a comprehensive approach.
People
- Security Awareness Training: Educate employees about common threats, phishing attacks, and social engineering tactics.
- Strong Access Controls: Implement robust password policies, multi-factor authentication (MFA), and role-based access controls.
- Incident Response Planning: Develop and regularly test an incident response plan to effectively handle security breaches.
Process
- Risk Assessment: Identify and prioritize potential threats to your organization.
- Regular Security Audits: Conduct thorough security audits to identify vulnerabilities and weaknesses.
- Patch Management: Keep software and systems up-to-date with the latest patches to address vulnerabilities.
- Data Loss Prevention (DLP): Implement measures to protect sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction.
- Business Continuity and Disaster Recovery (BCDR): Have a plan in place to continue operations in case of a disruption.
Technology
- Network Security: Employ firewalls, intrusion detection and prevention systems (IDPS), and network segmentation.
- Endpoint Protection: Protect devices like laptops, desktops, and mobile devices with antivirus and endpoint detection and response (EDR) solutions.
- Data Encryption: Encrypt sensitive data both at rest and in transit.
- Cloud Security: Implement strong security measures for cloud-based applications and data.
- Email Security: Use email filtering, spam protection, and anti-phishing measures.
Additional Considerations
- Third-Party Risk Management: Evaluate the security practices of third-party vendors and suppliers.
- Mobile Device Management (MDM): Manage and secure corporate-owned mobile devices.
- Security Information and Event Management (SIEM): Centralize log management and threat detection.
Enterprise security and new technological threats
While new technologies help organizations enhance their cybersecurity postures, adversaries also leverage them. Following are several new technologies that are being weaponized by cybercriminals.
5G technology
The adoption of 5G technology introduces new security challenges due to configuration errors and unpatched vulnerabilities that could allow attackers to move laterally across 5G network slices.
Artificial intelligence and machine learning
AI and ML are increasingly seen in emerging enterprise security threats and advanced persistent threats (APTs). Cybercriminals are using AI and ML to:
- Automate large-scale spear-phishing campaigns using AI algorithms to identify targets and craft personalized messages
- Create targeted phishing emails with detailed personalization drawn from public sources (e.g., social media) and using natural language processing (NLP)
- Use AI-generated deepfake voices for voice phishing (vishing)
Augmented reality and virtual reality
AR and VR technologies present a risk to user’s privacy, because AR technologies collect a lot of data about who the user is and what they are doing. Enterprise security is put at risk in a number of ways, including vulnerabilities being exploited to steal network credentials, initiate a social engineering campaign, propagate malware, or launch a distributed denial-of-service (DDoS) attack.
Blockchain
Despite its rich security features, blockchain technology poses enterprise security risks when relied upon by organizations. Among the blockchain risks are:
- A malicious user taking over 51% of a blockchain
- Consensus algorithm issues
- Regulatory challenges
- Smart contract vulnerabilities
Quantum computing
The power of quantum computing that is advancing cryptography could well be its undoing. Quantum computing poses an existential risk to enterprise security by threatening to compromise classical encryption protocols by breaking the codes
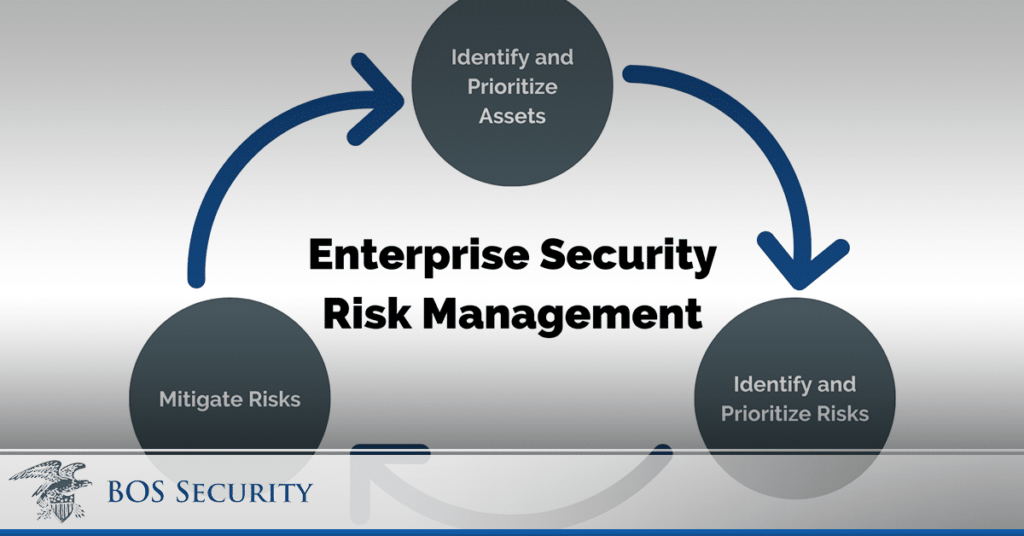
What Is Enterprise Security Risk Management?
Along with creating strategies to secure data, organizations should also plan to manage risk. Enterprise risk management is distinctly different from enterprise security. However, it falls under the same umbrella of services. Enterprise risk management is about identifying every resource that could be source of risks so that the organization can avoid and mitigate any threats.
Threat mitigation is vital for stopping current risks, but risk management focuses on reducing the organization’s overall risks related to its technology. Compliance is also important in risk management. However, most regulatory standards focus on ways to mitigate threats and stop data from being accessed. Risk management helps businesses realize their threat surface and identify ways to reduce the chance of a successful attack.
Just like enterprise security, effective risk management also requires considerable planning and strategic implementation. The first step is to map risks so that they can be visualized and realized. A heat map of risks is often used to determine the priority for each area of the network that contains the biggest risk factors.
After risk factors are determined, an action plan is established to determine the technology and methods that will be deployed. If it costs more to mitigate a risk than it would be if it were exploited, an organization might choose to leave it vulnerable or leave it as a low priority. Organizations often focus on the most expensive vulnerabilities first.
Both enterprise security and risk management focus on the protection of corporate data and other digital assets. They’re both critical for enterprise integrity and business continuity. As such, it’s important that they’re implemented by experts. Poorly projects could mean overlooked vulnerabilities and cybersecurity threats, leading to a significant data breach and possible data loss.
Plan for enterprise security success
Planning is vital to meet enterprise security objectives successfully. When beginning the project, it is important to develop a plan that aligns with the organization’s strategic goals and addresses tactical concerns.
Planning should also be built into the enterprise security maintenance program. Periodically, teams should schedule a time to review the plan and iterate to take changing requirements and evolving threats into account.
The success of enterprise security depends on investing time in detailed planning. From holistic to very specific, all aspects of enterprise security need to be considered and accounted for in the plan. With this, organizations find numerous benefits beyond enabling better security, including increased efficiency, reduced costs, and improved employee satisfaction.
What is Enterprise Cybersecurity?
Enterprises face a wide range of security threats and are a prime target of attack due to their large IT environments and access to valuable data. Enterprise cybersecurity is the practice of implementing strategies and security controls to manage the cybersecurity risks that an organization faces.
The Importance of Enterprise Cybersecurity
Enterprise cybersecurity programs are designed to manage the various impacts of cyberattacks, and are important for several reasons, including:
- Data Security: Enterprises have access to large volumes of sensitive data, including customer data, company data, and intellectual property. One objective of an enterprise security program is to protect this data against unauthorized access and potential misuse.
- Business Continuity: Cyberattacks have the potential to disrupt an organization’s business operations in various ways, such as the loss of access to important data due to a ransomware attack. Enterprise cybersecurity helps to manage these risks to the enterprise and to ensure that the company can continue to operate.
- Regulatory Compliance: Enterprises are subject to various regulations related to the protection of sensitive data and their business operations. Regulatory compliance is another key objective of an enterprise cybersecurity program.
- Reputation Management: A cyberattack against an enterprise can cause reputational damage and potential loss of existing or new customers. Managing cybersecurity risk helps an enterprise protect itself against potential threats to its reputation and customer base.
- Incident Response: Enterprise cybersecurity programs include strategies and tools for incident response. This enables companies to more promptly and effectively respond to security incidents.
Enterprise Cybersecurity Architecture
1. Risk Assessment
- Threat Identification: Identifying potential threats both internal and external to the organization.
- Vulnerability Assessment: Determining weaknesses in systems, applications, and networks.
- Impact Analysis: Evaluating the potential consequences of a successful attack.
- Risk Prioritization: Ranking threats based on their likelihood and potential impact.
2. Security Controls
- Technical Controls: Employing technology to protect systems and data (firewalls, intrusion detection systems, encryption).
- Administrative Controls: Implementing policies, procedures, and guidelines for security management.
- Physical Controls: Protecting hardware and facilities (access controls, surveillance, environmental controls).
3. Network Security
- Perimeter Security: Protecting the network boundary (firewalls, intrusion prevention systems).
- Internal Network Segmentation: Dividing the network into smaller segments to limit damage.
- Network Traffic Analysis: Monitoring network activity for suspicious patterns.
- Wireless Security: Protecting wireless networks from unauthorized access.
4. Endpoint Security
- Antivirus and Anti-malware: Protecting devices from malicious software.
- Endpoint Detection and Response (EDR): Identifying and responding to threats on endpoints.
- Data Loss Prevention (DLP): Preventing sensitive data from leaving the organization.
- Patch Management: Keeping software up-to-date with the latest security patches.
5. Data Security
- Data Classification: Categorizing data based on sensitivity.
- Data Encryption: Protecting data at rest and in transit.
- Access Controls: Limiting access to data based on user roles and permissions.
- Data Backup and Recovery: Protecting data from loss or corruption.
6. Identity and Access Management
- Identity Provisioning: Creating and managing user identities.
- Authentication: Verifying user identities.
- Authorization: Granting appropriate access privileges.
- Single Sign-On (SSO): Simplifying user access to multiple systems.
7. Security Incident and Event Management
- Log Management: Collecting and analyzing security logs.
- Threat Detection: Identifying potential security incidents.
- Incident Response: Coordinating response efforts to contain and mitigate incidents.
- Forensics: Gathering evidence for investigation and legal purposes.
8. Security Awareness and Training
- Employee Education: Raising awareness of cybersecurity threats and best practices.
- Phishing Simulations: Testing employees’ ability to identify phishing attacks.
- Incident Response Training: Preparing employees to respond to security incidents.
9. Business Continuity and Disaster Recovery
- Business Impact Analysis: Assessing the impact of disruptions on business operations.
- Disaster Recovery Planning: Developing strategies for restoring IT systems and operations.
- Business Continuity Planning: Ensuring continued business operations during disruptions.
Additional Considerations
- Cloud Security: Protecting data and applications in the cloud.
- Mobile Security: Securing mobile devices and applications.
- IoT Security: Protecting Internet of Things devices.
- Supply Chain Security: Managing risks associated with third-party suppliers.
Enterprise Security Solutions
Cyber attacks and data breaches are on the rise and continue to pose serious threats to our digital economy. New and existing infrastructure, including Internet backbones, mobile and fixed broadband networks, data centers, and cloud-based platforms, are constantly being exposed to these threats. Today’s hackers have an evolving arsenal of tools that can penetrate both public and private networks and attack vulnerable systems, devices and programs. To protect business assets and customer privacy, it is imperative that an enterprise’s security be continuously maintained and improved to effectively guard against internal and external threats.
Broadcom is a leading provider of enterprise security solutions worldwide leveraging the breadth and depth of expertise in both hardware and software security. Broadcom offers a broad portfolio of embedded security solutions, industry-leading mainframe security and payment authentication software, and a best-in-class suite of integrated Symantec cyber security software. From software to silicon, security solutions from Broadcom are widely deployed and used in networks across the globe. With such unparalleled and industry-unique offerings plus an extensive foothold in enterprise security, Broadcom is best equipped to address today’s constantly evolving challenges of protecting data and digital infrastructure from multifaceted threats while enabling enterprises to navigate risk and thrive in a fast-changing world.

Conclusion
Enterprise security is an evolving, complex challenge that demands constant vigilance and adaptation. The digital landscape, characterized by increasing interconnectedness and the proliferation of data, presents both unprecedented opportunities and significant risks.
A robust enterprise security strategy is no longer a luxury but a necessity. It encompasses a multifaceted approach that includes:
- People: Employees must be educated and trained to recognize and mitigate threats.
- Process: Effective security policies and procedures are crucial for operational efficiency and risk management.
- Technology: Advanced tools and solutions are essential for detecting, preventing, and responding to cyberattacks.
However, it’s important to recognize that security is an ongoing journey, not a destination. Threats are constantly evolving, and organizations must stay ahead of the curve by investing in research, development, and continuous improvement.
Ultimately, the success of enterprise security depends on a holistic approach that prioritizes data protection, business continuity, and customer trust. By fostering a culture of security awareness and implementing comprehensive measures, organizations can significantly reduce their risk exposure and build resilience in the face of cyber threats.
FAQs
Enterprise security involves the various technologies, tactics, and processes used to protect digital assets against unauthorized use, abuse, or infiltration by threat actors. Enterprise security systems also include the people and policies that organizations use to secure their network infrastructure, including assets such as devices and various endpoints.
Cybersecurity protects digital assets within the organization’s network. Enterprise security not only includes the protection of cybersecurity but also involves securing data while in transit and as it goes to servers, the network, and end-users.