Operational Technology (OT)
Operational technology (OT) uses hardware and software to manage industrial equipment and systems. OT controls high-tech specialist systems, like those found in the energy, industrial, manufacturing, oil and gas, robotics, telecommunications, waste control, and water control industries.
Industrial control systems (ICS) are one of the most prominent forms of OT. They control and monitor the performance of industrial processes and deploy systems like supervisory control and data acquisition (SCADA), which gather and analyze data in real time to manage plant equipment. These systems typically use programmable logic controllers (PLCs), which use information from sensors or devices to perform tasks like monitoring machine productivity, tracking operating temperatures, and automating machine processes.

Information Technology (IT)
Information technology (IT) is the development, management, and application of computer equipment, networks, software, and systems. IT is crucial to modern business operations because it enables people and machines to communicate and exchange information.
- Operations: The day-to-day management of IT departments, which includes managing devices, maintaining networks, testing the security of applications and systems, and providing technical support.
- Infrastructure maintenance: The process of setting up and maintaining infrastructure equipment, such as cabling, laptops, phones and phone systems, and physical servers.

Benefits of Operation Technology (OT)
Operation Technology (OT) is the backbone of industrial processes, ensuring they are optimized, reliable, efficient, and safe. Here are some key benefits:
Improved Efficiency and Productivity
- Real-time data analysis: OT provides instant insights into operational processes, enabling data-driven decisions.
- Process optimization: By analyzing data, processes can be fine-tuned for maximum efficiency and output.
- Reduced downtime: Predictive maintenance and anomaly detection minimize equipment failures and interruptions.
- Automation: OT automates repetitive tasks, freeing up human resources for higher-value activities.
Enhanced Decision Making
- Data-driven insights: OT generates valuable data that informs strategic and operational decisions.
- Faster response times: Real-time information allows for swift responses to changing conditions.
- Improved forecasting: Historical data and analytics enable accurate predictions.
Increased Safety
- Hazard detection: OT systems can identify potential safety risks and initiate preventive measures.
- Remote monitoring: Operators can monitor hazardous processes from a safe distance.
- Compliance: OT helps ensure adherence to industry safety standards and regulations.
Cost Reduction
- Energy efficiency: OT can optimize energy consumption through data analysis and control.
- Reduced waste: Identifying and eliminating inefficiencies leads to material and resource savings.
- Optimized maintenance: Predictive maintenance extends equipment life and reduces repair costs.
Other Benefits
- Improved product quality: Consistent process control leads to higher product quality.
- Increased flexibility: OT enables rapid adaptation to changing market demands.
- Enhanced sustainability: OT supports environmentally friendly practices through energy efficiency and waste reduction.
Benefits of Information Technology (IT)
Information Technology (IT) has revolutionized the way we live and work. Its impact is felt across industries and sectors, driving efficiency, innovation, and growth. Here are some key benefits:
Enhanced Communication and Collaboration
- Real-time communication: Tools like email, instant messaging, and video conferencing facilitate seamless communication across distances.
- Improved collaboration: Cloud-based platforms and project management tools enable teams to work together efficiently.
- Knowledge sharing: IT facilitates the easy sharing of information and expertise.
Increased Productivity and Efficiency
- Automation: IT automates repetitive tasks, freeing up human resources for more strategic work.
- Data analysis: IT tools help analyze large datasets to identify trends and improve decision-making.
- Process optimization: IT enables the streamlining of business processes, reducing errors and increasing efficiency.
Improved Decision Making
- Data-driven insights: IT provides access to data that can be analyzed to inform better decisions.
- Business intelligence: IT tools help visualize data and identify patterns, leading to improved strategic planning.
- Risk management: IT systems can help identify and mitigate potential risks.
Enhanced Customer Experience
- Personalized service: IT enables businesses to deliver tailored experiences based on customer data.
- Improved customer support: IT tools facilitate efficient customer support channels.
- E-commerce: IT has enabled online shopping, providing customers with convenience and choice.
Innovation and Growth
- New business models: IT has created opportunities for new business models and revenue streams.
- Competitive advantage: IT can help businesses differentiate themselves from competitors.
- Market expansion: IT facilitates global reach and market expansion.
Other Benefits
- Cost reduction: IT can help reduce operational costs through automation and efficiency.
- Security: IT systems can protect sensitive data from cyber threats.
- Accessibility: IT can improve access to information and services for people with disabilities.
Overcome the obstacles to IT/OT convergence
IT/OT convergence is a significant challenge that involves altering procedures for both technical disciplines.
- Scale of connectivity. OT typically connects far more devices than an IT network. The sheer number of devices involved in a convergence effort must be considered before networks converge.
- Device inventory. Everything that’s connected to OT and IT networks must be accounted for to ensure that devices aren’t left unsecured or orphaned. Communication between diverse devices must be tested and confirmed. This also suggests that IT and OT personnel develop a basic understanding of the operation of each other’s equipment to enhance troubleshooting and remediation efforts.
- Encryption. The converged systems should encrypt all communications between devices and other processing resources, whether they are internal to the organization or provided by outside services.
- Hybrid storage systems. In most cases, the data collected in OT and IT environments will be merged at some point. Combining edge storage with more traditional centralized storage can pose problems because of the differing natures of the data each environment supports.
- Ask for a software bill of materials. SBOM is a list of all the software components and dependencies that go into a device deployed in an IoT environment.
Why Cybersecurity Is Essential in OT and IT
Operational technology (OT) and information technology (IT) security protect devices, networks, systems, and users.
Cybersecurity has long been critical in IT and helps organizations keep sensitive data safe, ensure users connect to the internet securely, and detect and prevent potential cyberattacks. Cybersecurity is also vital to OT systems to protect critical infrastructure. Any momentary delay or period of unplanned downtime can cause manufacturing plants, power plants, or water supply systems to shut down.
Protecting these systems becomes even more critical as they become more connected, which opens up new vulnerabilities for cyber criminals to exploit and gain access to industrial networks. As a result, attacks are increasing, with more than 90% of organizations that operate OT systems having experienced one or more damaging security events in a two-year period, according to Ponemon Institute research.
Why IT and OT Collaboration Is Necessary
In the past, IT and OT environments were typically isolated from one another. This “air gap” helped to protect OT systems from potential cyber threats. Since these systems are often long-lived and infrequently updated, they commonly contain exploitable vulnerabilities.
- Greater Efficiency: IT/OT integration enables real-time monitoring of OT environments from IT systems. This enables operators to rapidly detect issues and make adjustments as needed, increasing efficiency and effectiveness.
- Decreased Overhead: Standalone IT and OT networks may have required duplicate systems with the same role in each network. IT/OT convergence enables reduced overhead by eliminating these redundant systems.
- Security Monitoring: Collaboration between IT and OT environments provides security personnel with greater visibility into OT networks and systems. This can enable greater OT security monitoring and the potential to more effectively prevent, detect, and respond to cybersecurity threats.
Protecting Against OT Vulnerabilities
Now that we understand the consequences of cyberattacks on OT systems in critical infrastructure organizations, it’s important to understand the definition of OT vulnerabilities and how to protect against them.
1. Lack of segmentation:
If OT networks are not properly segmented, an attacker who gains access to one part of the network has the potential to move laterally through the entire OT environment.
2. Outdated software:
In critical infrastructure organizations, it is common to have a mix of new and legacy devices in the environment.
3. Lack of secure access:
If remote access to OT by internal personnel and/or third-parties such as maintenance technicians or original equipment manufacturers .
4. Poor password hygiene:
Weak passwords that can be easily guessed or are used across various personal and professional platforms make it simple for hackers to breach OT systems. Without visibility into user sessions, breaches can be difficult to identify and mitigate.
IT and OT Cybersecurity with Check Point
Cybersecurity is essential in both IT and OT environments, and Check Point offers solutions tailored to the security needs of both. At the network level, it’s critical for an organization to be able to identify and block threats before they reach vulnerable systems. Check Point Quantum Network Security provides the visibility and control needed to achieve this.
In addition to its numerous IT security offerings, Check Point also offers security solutions tailored to OT/ICS systems.
Differences between OT and IT cybersecurity
There are significant OT and IT differences. The primary ones are that OT systems are autonomous, isolated, self-contained, and run on proprietary software.
1. Operational environment
Possibly the most significant difference between IT and OT cybersecurity is the environment they operate in and serve to protect. OT cybersecurity safeguards industrial environments, which typically involve machinery, PLCs, and communication across industrial protocols.
2. Confidentiality vs. safety
The purpose of OT vs. IT security also differs based on what they aim to achieve for organizations. The primary objective of OT cybersecurity is to ensure the availability and safety of critical equipment and processes.
3. Frequency vs. destruction
Another noteworthy OT vs. IT difference is the type of security events they defend against. OT cybersecurity is typically put in place to prevent highly destructive events. OT systems generally have fewer entry points, yet the magnitude of a compromise is comparatively greater—even a minor incident can result in vast financial losses and can affect an entire nation through a power outage or water contamination.
4. Patching frequency
The nature of OT and IT systems also means they have very different patching requirements. OT networks are typically rarely patched as doing so may require the entire production process to be halted.
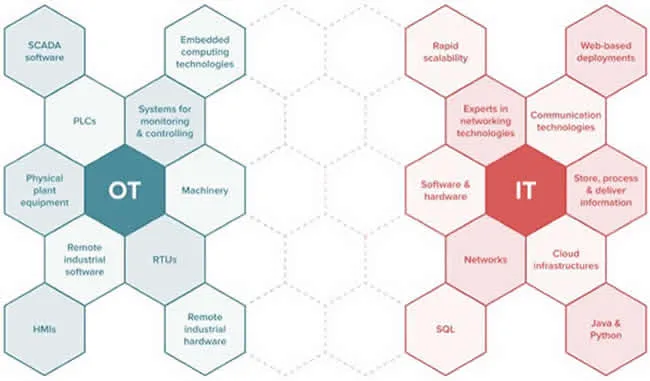
How do OT and IT networks differ?
OT and IT network infrastructure have similar elements, like switches, routers, and wireless technology. Therefore, OT networks can benefit from the rigor and experience that IT has built over the years with common network management and security controls to build a solid network foundation.
Form factor: OT network devices come in smaller and modularized form factors so they can be mounted in different ways, such as on rails, walls, or light poles, in cars, or even embedded within other equipment.
Network interfaces: Depending on their purpose, OT devices may support networks such as LoraWAN or WiSun to connect industrial IoT (IIoT) devices.
Bridging the IT/OT Divide
The tug-of-war between innovative technology and reliable operations is a tale as old as time. New technologies promise progress, but established practices ensure stability. Today, this tension defines the IT/OT divide in industrial security, where the drive for digital transformation clashes with the need to maintain critical operations.
- IT Security Solutions Don’t Always Work in OT: IT security prioritizes rapid fixes, but these solutions may disrupt sensitive OT systems, causing shutdowns, malfunctions, or communication failures that can halt production.
- Conflicting Priorities: IT and OT have different security priorities. IT focuses on data confidentiality, while OT prioritizes uninterrupted operations and safety. This misalignment means security decisions created for IT environments often fail to account for the unique requirements of OT systems.
- The Expertise Gap: Many IT teams don’t have experience with OT systems. This makes it difficult to understand, assess, and prioritize risks based on their true impact on operations, leading to misaligned security decisions.
Why are OT networks at risk?
Internet connectivity introduces ease of operability, but apart from those benefits, this transformation has exposed the system to vulnerabilities that cannot be stopped by an armed guard.
- Direct Internet Connections: Most organizations have direct connections to the public internet. It is common knowledge that only one internet-connected device is enough to provide a gateway for attackers to introduce malware into OT networks.
- Insecure Passwords: Operators have been using insecure passwords for convenient entry to the networks. This makes it easy for attackers to use brute-force discovery of credentials to gain unauthorized operator access.
- Unnecessary Exposure: Many industries have at least one misconfigured wireless access point that many devices, such as laptops, can access. To prevent malware attacks, access point configurations must be audited to reveal any misconfigurations.
- Outdated Operating System: An outdated operating system that no longer receives security updates is extremely vulnerable to security attacks. All machines, including access points, must be inventoried and patched to the latest manufacturers’ specifications to prevent compromise.
Why are IT networks at risk?
. Increased Complexity:
- Interconnected systems: Modern networks are complex webs of devices, applications, and systems, making it difficult to secure every point.
- Remote work: The rise of remote work has expanded the attack surface as more devices connect to the network from various locations.
2. Advancements in Technology:
- IoT devices: The proliferation of IoT devices creates new entry points for attackers.
- Cloud computing: While offering benefits, cloud environments also introduce security challenges.
3. Human Error:
- Phishing attacks: Employees can be tricked into clicking malicious links or downloading harmful attachments.
- Weak passwords: Poor password practices leave networks vulnerable to brute-force attacks.
4. Cybercriminals:
- Sophisticated attacks: Cybercriminals are becoming more skilled and organized, developing new attack methods.
- Financial motivation: The potential for financial gain drives cyberattacks, making them a lucrative business.
5. Outdated Systems and Software:
- Vulnerabilities: Unpatched systems and software contain known vulnerabilities that can be exploited.
- Slow updates: Delayed updates increase the risk of attacks.
6. Data Privacy Regulations:
- Compliance challenges: Adhering to data privacy regulations can be complex and costly, increasing the risk of data breaches.
- Financial penalties: Non-compliance can result in significant financial penalties.
To mitigate these risks, organizations must implement robust security measures, including firewalls, intrusion detection systems, employee training, and regular security audits.
How should organizations secure their OT environment?
Managing operational technology security is one of the most important tasks for organizations. To secure an OT environment from any type of cyber threat, organizations can create a Smarter Security Operations Center using the MITRE ATT&CK framework.
- Secure Access/Centralized Logging: Providing secure access is challenging for many organizations. Organizations need to establish different access for different users via various access routes. To provide secure access, user access should be secured by multi-factor authentication. Secure access control can be achieved with centralized logging.
- Asset Management: OT systems serve as the brain of any industry, and an organization’s primary task is to protect them. Many OT systems face a lack of visibility. Many organizations do not know the exact umber of OT systems they have in their organization. As a part of asset management, every organization must have a full inventory of its OT systems. This will enable them to know what they are protecting and plan accordingly.
- Software Vulnerability Analysis: Organizations must be cognizant of all software versions, updates, and compatibility with the OT systems in the environment. Vulnerability scanning is also an important part of understanding where weaknesses may exist.
- Patching Management: Patching is an important part of hardware and software stewardship. Organizations must know the patching requirements of the assets in their possession. OT patching is a complex process, so the process must be handled judiciously. This means that sometimes, automatic OT patching may not be the best approach.
How should organizations secure their IT environment?
Securing an IT environment is a multifaceted approach that involves a combination of technological, procedural, and human elements.
Technological Measures:
Network Security:
- Firewalls: Protect network perimeters from unauthorized access.
- Intrusion Detection and Prevention Systems (IDPS): Monitor network traffic for suspicious activity.
- Virtual Private Networks (VPNs): Secure remote access.
Endpoint Protection:
- Antivirus and Antimalware Software: Protect devices from malicious threats.
- Endpoint Detection and Response (EDR): Identify and respond to threats on endpoints
Data Protection:
- Encryption: Protect data at rest and in transit.
- Data Loss Prevention (DLP): Prevent sensitive data from being leaked.
- Regular Backups: Protect data from accidental loss or ransomware attacks.
Identity and Access Management (IAM):
- Strong Password Policies: Enforce complex and unique passwords.
- Multi-Factor Authentication (MFA): Require multiple forms of verification.
- Access Controls: Limit user access to necessary data and systems.
Procedural Measures:
- Incident Response Plan: Develop a comprehensive plan for responding to security incidents.
- Regular Security Assessments: Conduct vulnerability assessments and penetration testing.
- Employee Training: Educate employees about cybersecurity best practices.
- Patch Management: Keep software and systems up-to-date with the latest patches.
- Supply Chain Security: Evaluate the security practices of third-party vendors.
Conclusion
IT (Information Technology) and OT (Operational Technology) are distinct but increasingly intertwined domains. While IT focuses on managing and processing information, OT is concerned with controlling physical devices and processes.
Key Differences:
- Focus: IT prioritizes data, while OT prioritizes physical processes.
- Goals: IT aims for efficiency and information accessibility, while OT seeks optimized operations and production.
- Technology: IT often leverages standardized, commercial off-the-shelf (COTS) technologies, while OT relies on specialized, often proprietary hardware and software.
- Security: IT has a longer history of security focus, while OT is catching up due to increasing cyber threats.
- Downtime Impact: IT failures typically result in productivity losses, while OT failures can lead to physical damage, safety hazards, and financial losses.
The Convergence of IT and OT:
Despite their differences, the lines between IT and OT are blurring. The rise of IoT, Industry 4.0, and digital transformation is driving convergence. This convergence offers significant opportunities for increased efficiency, data-driven decision making, and innovation. However, it also presents new challenges, particularly in terms of security and integration.
To fully realize the benefits of IT and OT convergence, organizations must:
- Bridge the gap: Foster collaboration between IT and OT teams.
- Prioritize security: Implement robust security measures to protect both IT and OT systems.
- Invest in skilled personnel: Develop a workforce with expertise in both IT and OT.
- Adopt a holistic approach: View IT and OT as interconnected parts of a larger system.
By understanding the unique characteristics of IT and OT, and by effectively managing their convergence, organizations can achieve operational excellence, improve safety, and gain a competitive edge.
FAQs
There are significant OT and IT differences. The primary ones are that OT systems are autonomous, isolated, self-contained, and run on proprietary software. In contrast, IT systems are connected, lack autonomy, and typically run on popular operating systems like iOS and Windows.
These systems manage and monitor physical processes, making them susceptible to disruptions that could have severe consequences. OT systems face a range of security vulnerabilities, including malware infiltration, human error, lack of visibility, outdated software, and insecure remote access.