Cybersecurity Mesh
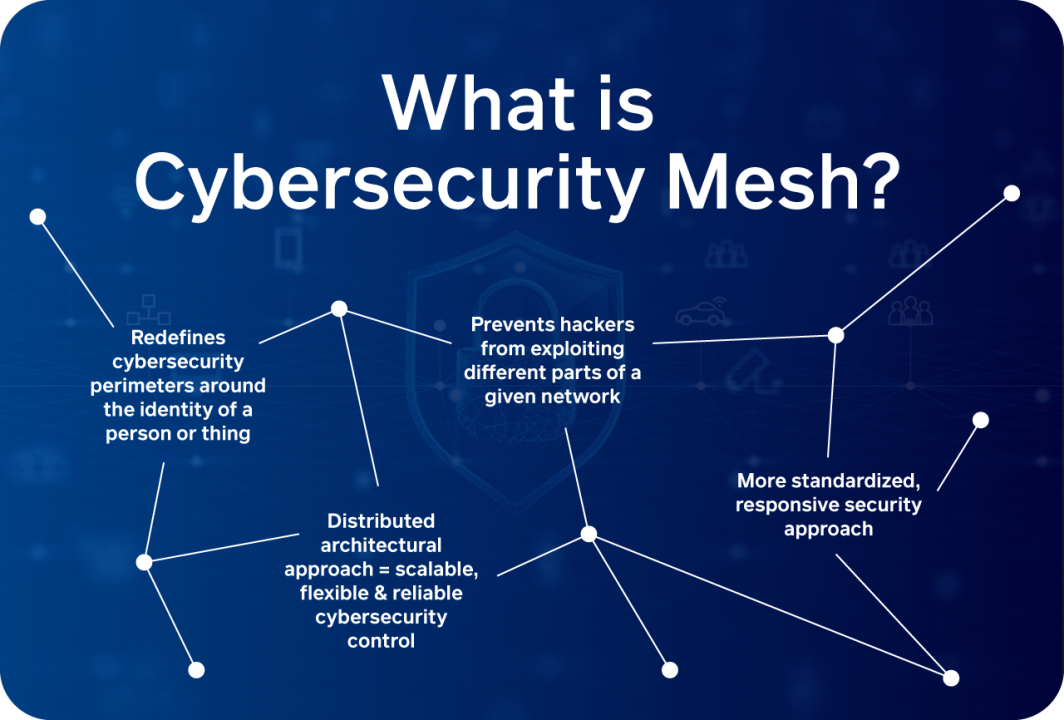
Gartner defines cybersecurity mesh architecture (CSMA) as “a composable and scalable approach to extending security controls, even to widely distributed assets. Its flexibility is especially suitable for increasingly modular approaches consistent with hybrid multicloud architectures. CSMA enables a more composable, flexible, and resilient security ecosystem. Rather than every security tool running in a silo, a … Read more