A penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. In the context of web application security, penetration testing is commonly used to augment a web application firewall (WAF).

Why is penetration testing important?
Penetration testing helps an organization discover vulnerabilities and flaws in their systems that they might not have otherwise been able to find. This can help stop attacks before they start, as organizations can fix these vulnerabilities once they have been identified.
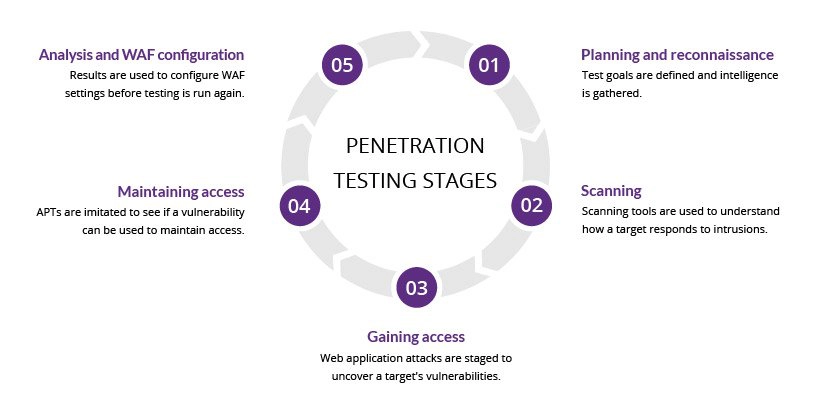
Penetration testing stages
The pen testing process can be broken down into five stages.
1. Planning and reconnaissance
The first stage involves:
- Defining the scope and goals of a test, including the systems to be addressed and the testing methods to be used.
- Gathering intelligence (e.g., network and domain names, mail server) to better understand how a target works and its potential vulnerabilities.
2. Scanning
The next step is to understand how the target application will respond to various intrusion attempts. This is typically done using:
- Static analysis – Inspecting an application’s code to estimate the way it behaves while running.
3. Gaining Access
This stage uses web application attacks, such as cross-site scripting, SQL injection and backdoors, to uncover a target’s vulnerabilities.
4. Maintaining access
The goal of this stage is to see if the vulnerability can be used to achieve a persistent presence in the exploited system— long enough for a bad actor to gain in-depth access.
5. Analysis
The results of the penetration test are then compiled into a report detailing:
- Specific vulnerabilities that were exploited
- Sensitive data that was accessed
- The amount of time the pen tester was able to remain in the system undetected
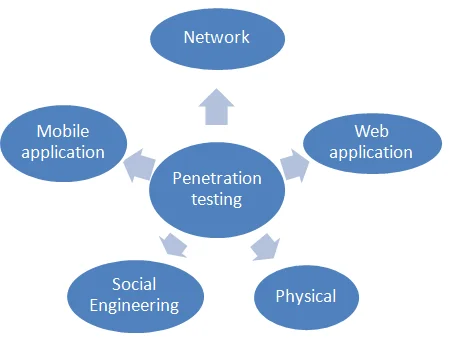
Types of penetration testing
There are many types of penetration tests. Following are the most common types used as shown in the figure above. Let us understand these different types of penetration testing performed to evaluate security robustness of a network or system of the organization.
Network penetration test : In this test, tester tests network environment for potential security threats or vulnerabilities. This can be categorized into two types viz. external and internal. In external test, tester can test public IP addressese where as in internal test, tester will become part of internal network and test it. In this testing, organization provides physical access as well as VPN access to the tester.
Web application penetration test : Now-a-days web application hosts and collects critical customers data such as credit or debit card numbers, usernames/passwords and so on. Hence it is essential to perform web app penetration testing
Mobile application penetration test : This test has also become very essential today. This is due to the fact that all the organizations are developing and providing access access to their customers through mobile apps on android and iOS mobile phones. This test ensure that mobile apps are secure enough to protect personal informations of their clients while using mobile apps.
Physical penetration test : In this test, testers will be asked by the organization to physical perform tests on their security controls such as locks and RFID/NFC or other scanning mechanisms.
Social Engineering penetration test : This test verifies adherence of employees to security policies/practices defined by management of their organization.
Advantages of Penetration Testing
Penetration testing, often referred to as pen testing, is a crucial component of a robust cybersecurity strategy.
Identification of Vulnerabilities
- Reveals weaknesses: Pen testing uncovers hidden vulnerabilities that could be exploited by malicious actors.
- Prioritizes risks: Helps identify the most critical vulnerabilities and focuses remediation efforts accordingly.
Risk Mitigation
- Reduces financial loss: Prevents costly data breaches and downtime.
- Protects reputation: Safeguards brand image and customer trust.
Compliance and Assurance
- Meets regulatory requirements: Demonstrates compliance with industry standards and regulations.
- Builds confidence: Provides assurance to stakeholders, clients, and partners.
Improved Security Posture
- Enhances security awareness: Raises awareness of potential threats among employees.
- Strengthens defenses: Allows for the implementation of countermeasures to protect against identified vulnerabilities.
- Optimizes security investments: Helps allocate resources effectively to address the most significant risks.
Business Continuity
- Ensures system availability: Identifies potential disruptions and helps maintain business operations.
- Reduces downtime: Minimizes the impact of incidents by preparing for potential threats.
Other Benefits
- Third-party validation: Provides an independent assessment of security posture.
- Competitive advantage: Demonstrates a commitment to security and customer protection.
Disadvantages of Penetration Testing
While penetration testing is a valuable security tool, it also comes with certain drawbacks:
Cost
- Expensive: Professional penetration testing can be costly, particularly for large-scale or complex systems.
- Resource-intensive: Requires specialized skills and tools.
False Positives
- Time-consuming: Investigating false positives can be time-consuming and resource-intensive.
- Potential disruption: Can disrupt normal operations if not managed carefully.
Damage Potential
- Accidental system damage: There is a risk of accidental system damage if not conducted carefully.
- Data exposure: Although unlikely, there’s a potential for sensitive data exposure.
Limited Scope
- Snapshot in time: A penetration test provides a snapshot of security at a specific point in time.
- Not a complete guarantee: It does not guarantee complete protection from all threats.
Ethical Considerations
- Legal and ethical boundaries: Testers must adhere to legal and ethical guidelines to avoid legal repercussions.
- Potential for abuse: The information gained could potentially be misused by malicious actors.
Employee Morale
- Stressful for staff: The testing process can be stressful for employees.
- Impact on productivity: Testing can temporarily disrupt workflows and reduce productivity.
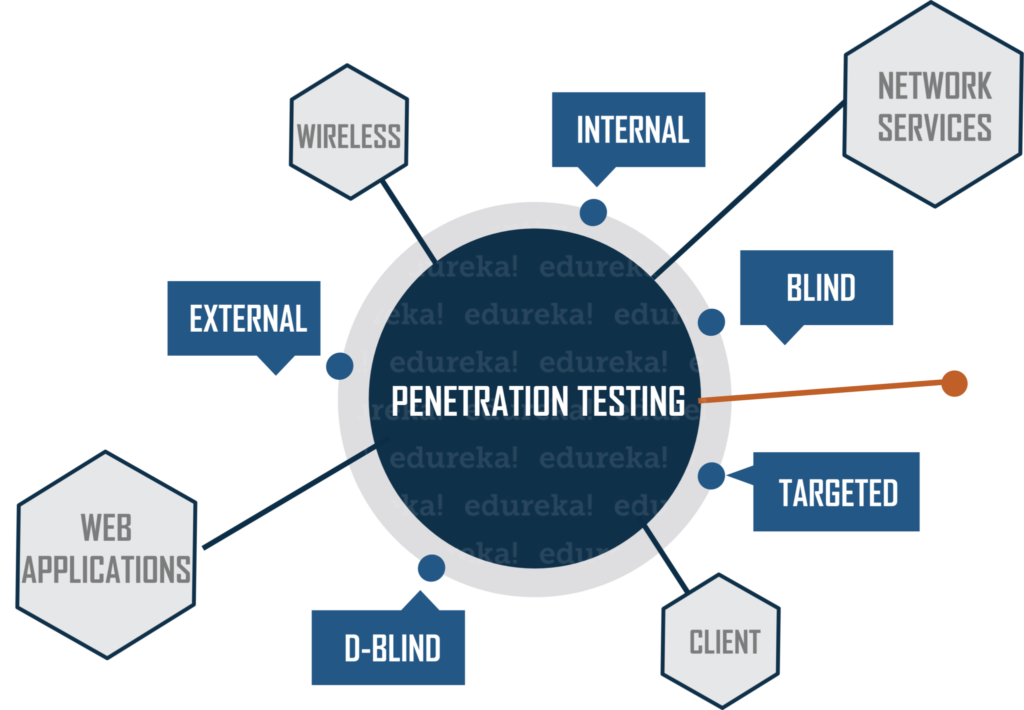
Penetration testing methods
External testing
External penetration tests target the assets of a company that are visible on the internet, e.g., the web application itself, the company website, and email and domain name servers (DNS). The goal is to gain access and extract valuable data.
Internal testing
In an internal test, a tester with access to an application behind its firewall simulates an attack by a malicious insider. This isn’t necessarily simulating a rogue employee. A common starting scenario can be an employee whose credentials were stolen due to a phishing attack.
Blind testing
In a blind test, a tester is only given the name of the enterprise that’s being targeted. This gives security personnel a real-time look into how an actual application assault would take place.
Double-blind testing
In a double blind test, security personnel have no prior knowledge of the simulated attack. As in the real world, they won’t have any time to shore up their defenses before an attempted breach.
Targeted testing
In this scenario, both the tester and security personnel work together and keep each other appraised of their movements. This is a valuable training exercise that provides a security team with real-time feedback from a hacker’s point of view.
What are the types of pen testing tools?
There is no one-size-fits-all tool for pen testing. Instead, different targets require different sets of tools for port scanning, application scanning, Wi-Fi break-ins, or direct penetration of the network. Broadly speaking, the types of pen testing tools fit into five categories.
- Reconnaissance tools for discovering network hosts and open ports
- Vulnerability scanners for discovering issues in-network services, web applications, and APIs
- Proxy tools such as specialized web proxies or generic man-in-the-middle proxies
- Exploitation tools to achieve system footholds or access to assets
- Post exploitation tools for interacting with systems, maintaining and expanding access, and achieving attack objectives
How is a typical pen test carried out?
Pen tests start with a phase of reconnaissance, during which an ethical hacker spends time gathering data and information that they will use to plan their simulated attack. After that, the focus becomes gaining and maintaining access to the target system, which requires a broad set of tools.
Tools for attack include software designed to produce brute-force attacks or SQL injections. There is also hardware specifically designed for pen testing, such as small inconspicuous boxes that can be plugged into a computer on the network to provide the hacker with remote access to that network. In addition, an ethical hacker may use social engineering techniques to find vulnerabilities. For example, sending phishing emails to company employees, or even disguising themselves as delivery people to gain physical access to the building.
Methodologies for Standardized Penetration Testing
1. OSSTMM
The OSSTMM framework, one of the most recognized standards in the industry, provides a scientific methodology for network penetration testing and vulnerability assessment. This framework contains a comprehensive guide for testers to identify security vulnerabilities within a network (and its components) from various potential angles of attack.
2. OWASP
For all matters of application security, the Open Web Application Security Project (OWASP) is the most recognized standard in the industry. This methodology, powered by a very well-versed community that stays on top of the latest technologies, has helped countless organizations to curb application vulnerabilities.
3. MITRE ATT&CK
The MITRE ATT&CK framework has become a cornerstone in understanding modern security threats, allowing security professionals to replicate attacker techniques. This framework assists organizations in identifying vulnerabilities and developing tailored counter-measures:
- ATT&CK for Enterprise: covers adversarial behavior in Windows, Mac, Linux, and cloud environments.
- ATT&CK for Mobile: focuses on Android and iOS systems.
- ATT&CK for ICS: targets industrial control systems (ICS), detailing potential adversarial actions
4. NIST
The NIST 800-115 testing methodology, developed by The National Institute of Standards and Technology (NIST), is an essential resource for organizations aiming to bolster their information security.
Structured Approach: It emphasizes a methodical process in security assessment, covering planning, execution, and post-execution analysis. This structure helps organizations systematically address potential security vulnerabilities.
Diverse Testing Methods: The methodology incorporates various testing and examination methods, such as technical testing, examination, and interviewing. This multifaceted approach enables a more thorough evaluation of security controls.
5. PTES
The PTES Framework (Penetration Testing Methodologies and Standards) highlights the most recommended approach to structure a penetration test. This standard guides testers on various steps of a penetration test including initial communication, gathering information, as well as the threat modeling phases.
6. ISSAF
The ISSAF standard (Information System Security Assessment Framework) contains an even more structured and specialized approach to penetration testing than the previous standard. If your organization’s unique situation requires an advanced methodology entirely personalized to its context, then this manual should prove useful for the specialists in charge of your penetration test.
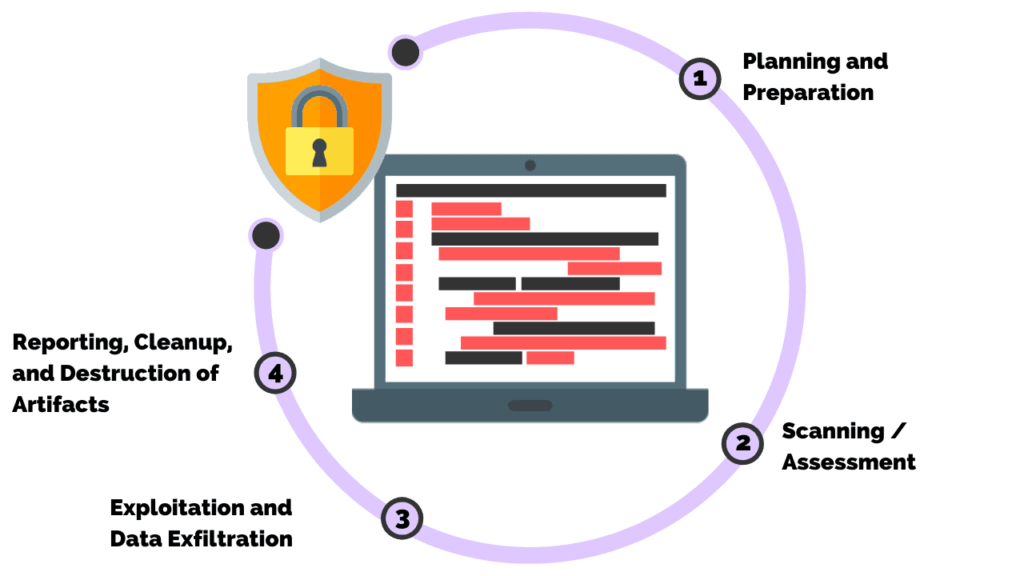
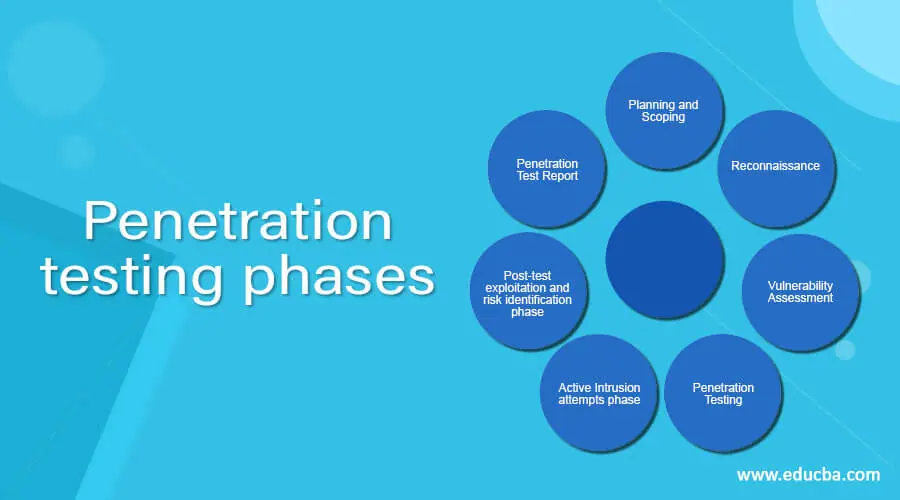
What are the phases of pen testing?
Pen testers simulate attacks by motivated adversaries. To do this, they typically follow a plan that includes the following steps:
Reconnaissance. Gather as much information about the target as possible from public and private sources to inform the attack strategy. Sources include internet searches, domain registration information retrieval, social engineering, nonintrusive network scanning, and sometimes even dumpster diving
Scanning. Pen testers use tools to examine the target website or system for weaknesses, including open services, application security issues, and open source vulnerabilities. Pen testers use a variety of tools based on what they find during reconnaissance and during the test.
Gaining access. Attacker motivations can include stealing, changing, or deleting data; moving funds; or simply damaging a company’s reputation. To perform each test case, pen testers determine the best tools and techniques to gain access to the system, whether through a weakness such as SQL injection or through malware, social engineering, or something else.
Maintaining access. Once pen testers gain access to the target, their simulated attack must stay connected long enough to accomplish their goals of exfiltrating data, modifying it, or abusing functionality. It’s about demonstrating the potential impact.
Penetration testing and web application firewalls
Penetration testing and WAFs are exclusive, yet mutually beneficial security measures.
For many kinds of pen testing (with the exception of blind and double blind tests), the tester is likely to use WAF data, such as logs, to locate and exploit an application’s weak spots.
In turn, WAF administrators can benefit from pen testing data. After a test is completed, WAF configurations can be updated to secure against the weak spots discovered in the test.
Finally, pen testing satisfies some of the compliance requirements for security auditing procedures, including PCI DSS and SOC 2. Certain standards, such as PCI-DSS 6.6, can be satisfied only through the use of a certified WAF. Doing so, however, doesn’t make pen testing any less useful due to its aforementioned benefits and ability to improve on WAF configurations.
What happens in the aftermath of a pen test?
After completing a pen test, the ethical hacker will share their findings with the target company’s security team. This information can then be used to implement security upgrades to plug up any vulnerabilities discovered during the test.
For web applications, these upgrades can include rate limiting, new WAF rules, and DDoS mitigation, as well as tighter form validations and sanitization. For internal networks, such upgrades could include a secure web gateway or moving to a Zero Trust security model. If the ethical hacker used social engineering tactics to breach the system, the company may consider better educating their employees, or examining and upgrading their access control systems to prevent lateral movement.
Secures companies’ applications, networks, and people with a combination of web application security solutions and a Zero Trust security platform.
How does pen testing differ from automated testing?
Although pen testing is mostly a manual effort, pen testers do use automated scanning and testing tools. But they also go beyond the tools and use their knowledge of the latest attack techniques to provide more in-depth testing than a vulnerability assessment .
Manual pen testing
Manual pen testing uncovers vulnerabilities and weaknesses not included in popular lists (e.g., OWASP Top 10) and tests business logic that automated testing can overlook (e.g., data validation, integrity checks). A manual pen test can also help identify false positives reported by automated testing.
Automated testing
Automated testing generates results faster and needs fewer specialized professionals than a fully manual pen testing process
Challenges of Penetration Testing
Penetration testing, while essential, is not without its challenges. These obstacles can impact the effectiveness and efficiency of the testing process.
Technical Challenges
- Complex IT Environments: Modern IT infrastructures are often complex, with multiple systems, networks, and applications interacting. This complexity can make testing difficult and time-consuming.
- Evolving Threat Landscape: Cyber threats constantly evolve, making it challenging to keep up with the latest attack techniques and tools.
- False Positives: Identifying genuine vulnerabilities amidst a sea of false positives can be time-consuming and resource-intensive.
- Limited Testing Scope: It’s often impractical to test every aspect of a system, leaving potential vulnerabilities undetected.
Organizational Challenges
- Resource Constraints: Penetration testing can be expensive, requiring skilled professionals and specialized tools.
- Scheduling Conflicts: Coordinating testing with business operations can be challenging, as it often requires system downtime or restrictions.
- Scope Definition: Clearly defining the scope of the test can be difficult, as it involves balancing comprehensive coverage with resource limitations.
- Overreliance on Automation: While automation can speed up testing, it may miss complex or human-error-based vulnerabilities.
Human Factors
- Skill Shortages: Finding qualified penetration testers with the necessary expertise can be challenging.
- Ethical Considerations: Testers must operate within legal and ethical boundaries, which can limit testing techniques.
- Organizational Resistance: Some organizations may resist penetration testing due to fear of exposing vulnerabilities.
Addressing these challenges requires careful planning, experienced professionals, and a strong commitment to security.
Practices for Penetration Testing
Effective penetration testing requires a structured approach and adherence to best practices. Here are some key guidelines:
Planning and Preparation
- Clear Objectives: Define the specific goals of the test, such as identifying vulnerabilities, assessing compliance, or testing incident response procedures.
- Scope Definition: Clearly outline the systems, applications, and networks to be included in the test.
- Risk Assessment: Prioritize targets based on their potential impact and likelihood of exploitation.
- Legal and Ethical Compliance: Ensure the test complies with relevant laws and regulations.
- Communication and Coordination: Establish clear communication channels with stakeholders and obtain necessary approvals.
Test Execution
- Experienced Testers: Employ skilled penetration testers with a deep understanding of attack methodologies.
- Diverse Testing Techniques: Utilize a combination of manual and automated tools to cover a broad attack surface.
- Real-world Simulations: Mimic real-world attack scenarios to assess system resilience.
- Documentation: Thoroughly document findings, including evidence and exploitation steps.
Reporting and Remediation
- Comprehensive Report: Provide detailed reports outlining vulnerabilities, their severity, and potential impact.
- Prioritized Recommendations: Offer actionable recommendations for addressing critical vulnerabilities.
- Remediation Verification: Follow up to ensure that recommended actions have been implemented effectively.
- Continuous Testing: Incorporate penetration testing into a regular security assessment program.
Additional Considerations
- Third-Party Validation: Consider using an external penetration testing provider for an unbiased assessment.
- Employee Training: Raise awareness among employees about potential threats and the importance of security best practices.
- Incident Response Planning: Develop and test an incident response plan to handle potential security breaches.
By following these best practices, organizations can maximize the benefits of penetration testing and strengthen their overall security posture.
Conclusion
Penetration testing is an indispensable component of a comprehensive cybersecurity strategy. By simulating real-world attacks, organizations can proactively identify and address vulnerabilities before malicious actors exploit them.
Through rigorous testing, businesses can:
- Mitigate risks: Reduce the likelihood of data breaches, financial loss, and reputational damage.
- Enhance security posture: Strengthen defenses against emerging threats and improve overall system resilience.
- Demonstrate compliance: Meet industry regulations and build trust with stakeholders.
- Optimize resource allocation: Focus security efforts on the most critical vulnerabilities.
While challenges and costs are associated with penetration testing, the potential benefits far outweigh the drawbacks. By adopting best practices and investing in skilled professionals, organizations can effectively leverage this critical security measure to safeguard their digital assets.
Continuous penetration testing and vulnerability management are essential for maintaining a strong security posture in today’s evolving threat landscape.
FAQs
These are called “zero-day vulnerabilities” i.e., you have no protection against them because penetration testing relies on known attack vectors and types. Successful cyber-attacks often come from the hacker who has the most skills and imagination.
To simplify this further, vulnerability scans focus primarily on identifying exploitable weaknesses of an IT infrastructure, while pen tests exploit these weaknesses to give you an assessment of how your security systems hold up against a real attack
If you’re unsure about how secure your systems are, a pentest is a great way to gain insights into any vulnerabilities before it’s too late. It may also be required for you to carry out a pen test to achieve or maintain compliance with security standards like PCI DSS
